Passwordless Sign In with Microsoft Entra ID (Azure AD) and YubiKey (FIDO2)
Last Updated on 18. January 2025
Passwordless Sign In with a FIDO2-enabled security key such as a YubiKey in conjunction with Microsoft Entra ID (Azure AD) provides high security while maintaining ease of use. There is no longer any need to enter a username and password.
For users with private mobile devices who do not want to install the Microsoft Authenticator app, a security key from YubiKey offers a good alternative.
This tutorial sets up a YubiKey 5 security key for passwordless sign in to Microsoft Azure and Microsoft 365 services.
Prerequisites and Licensing
Licenses
No paid license in Microsoft Azure is required to use a FIDO2-enabled security key. The Microsoft Entra ID Free (Azure AD Free) license in Azure Active Directory is sufficient.
Microsoft Entra multi-factor authentication (MFA)
Users must setup Azure multi-factor authentication. User guide: Enabling multi-factor authentication – cloudcoffee.ch explains the necessary procedure.
YubiKey FIDO2 Security Key
A YubiKey security key with FIDO2 support from Yubico.
To find the right YubiKey for you, the Yubico website will help you:
Which YubiKey is right for you | Quiz | Yubico
Order the YubiKey security key directly from Yubico:
Buy YubiKeys at Yubico.com | Shop hardware authentication security keys
Of course, FIDO2 security keys from other brands work too.
Enable Authentication method FIDO2 security key
Authentication method FIDO2 will be enabled in the Azure Portal (https://portal.azure.com).
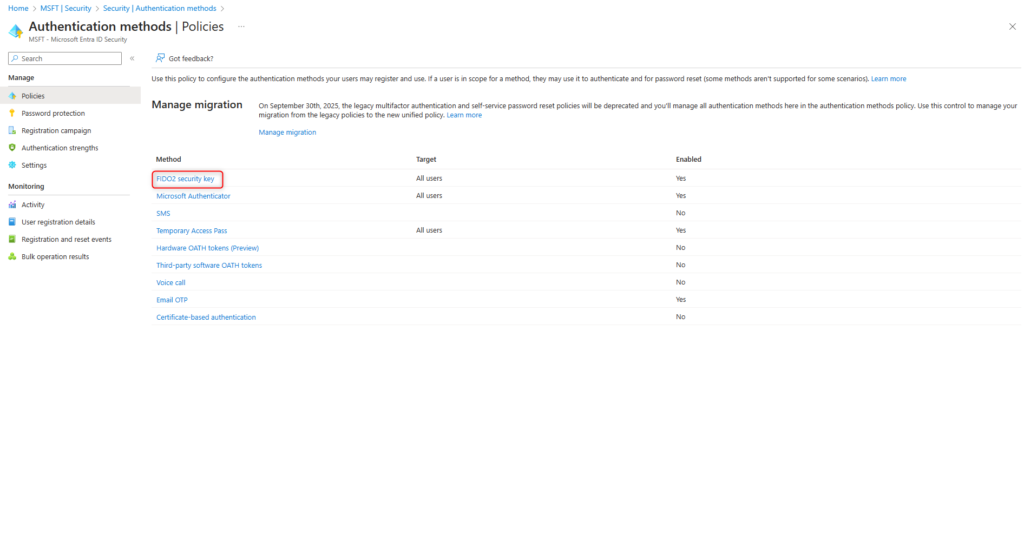
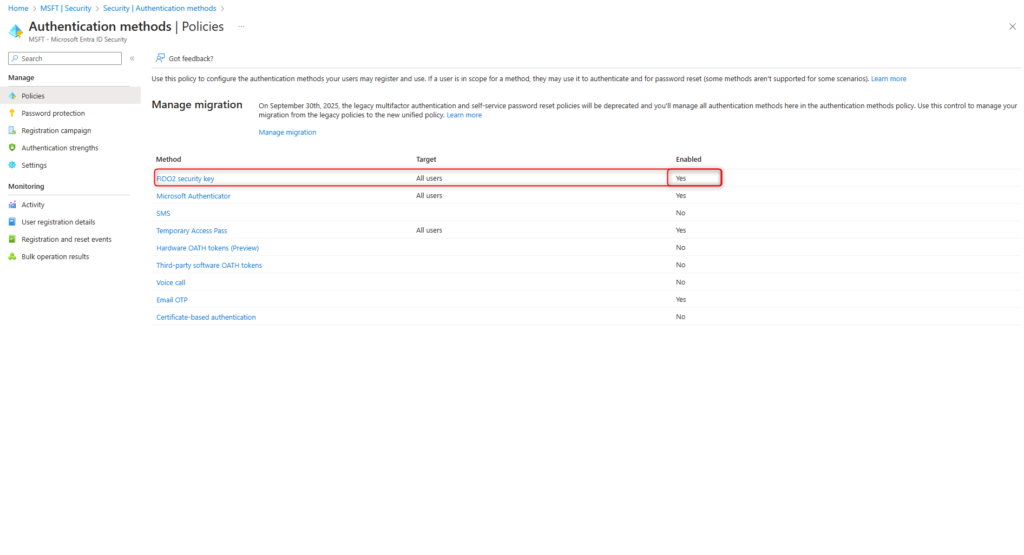
FIDO2 security key authentications are enabled in the Authentication methods menu of Microsoft Entra ID.
Select Microsoft Entra ID > Security
Select Authentication methods
Select FIDO2 security key
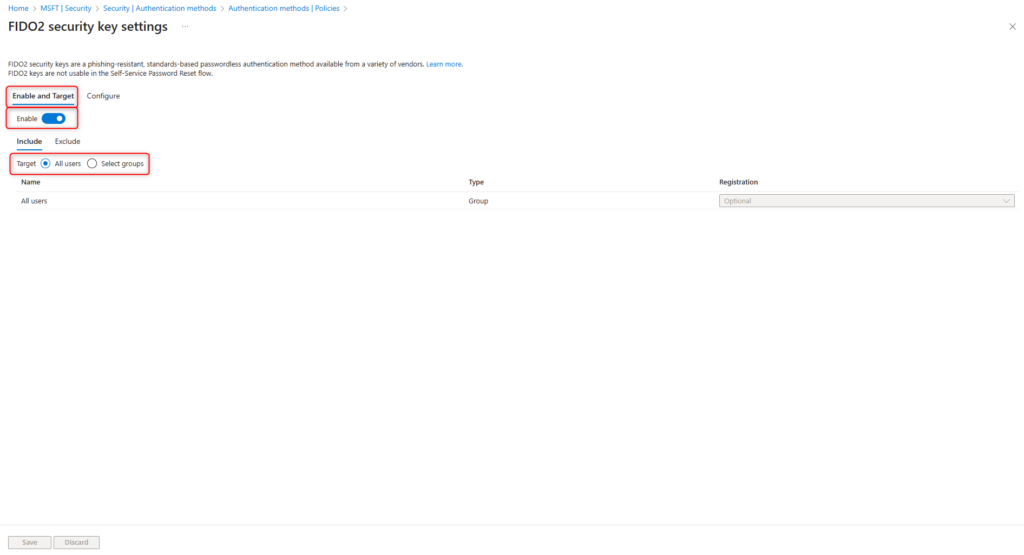
Switch on the Enable Toggle and select All users in the register Enable and Target
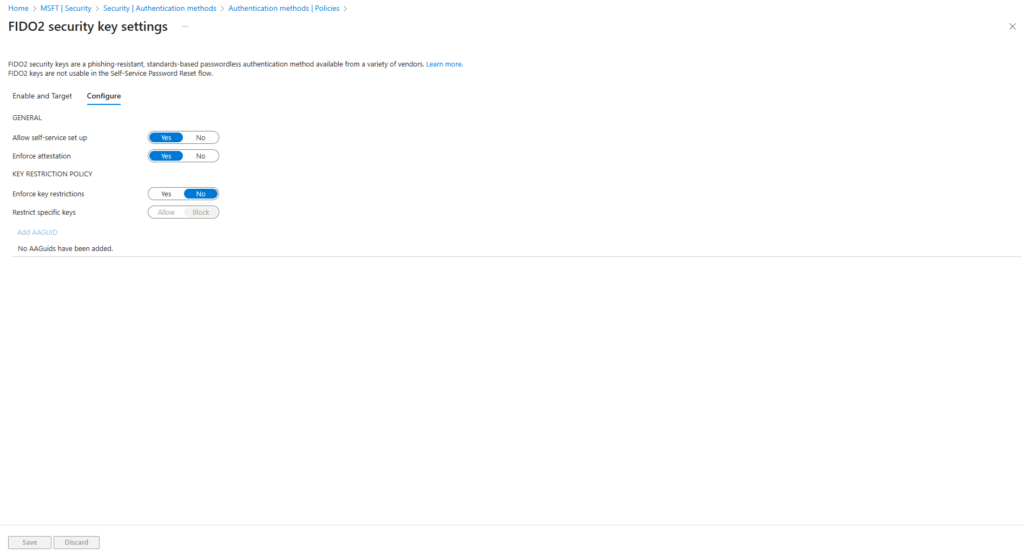
The following options can be set in the Configure tab:
Allow self-service setup
The option must be enabled for users to activate the YubiKey 5 security keys.
Enforce attestation
This option must be enabled and verifies that the FIDO2 security key identifies itself to Microsoft Entra ID (Azure AD) during registration. Among other things, this checks whether the security key actually corresponds to the specified model and supports the corresponding features.
Enforce key restrictions
With this option you can control which security keys may be used and which not. There is a possibility of an Allow or Block list. AAGUIDS (Authenticator Attestation Global Unique Identifier) are used for this function. An overview of the common AAGUIDs is provided by Clayton Tyger with the Entra Compatible Attestation FIDO Key Explorer.
Click on Save and Users can now register and use FIDO2-enabled security keys.
Setup YubiKey for Passwordless Sign In
Users sets up their personal YubiKey independently.
To do this, the user sign in at https://myprofile.microsoft.com.
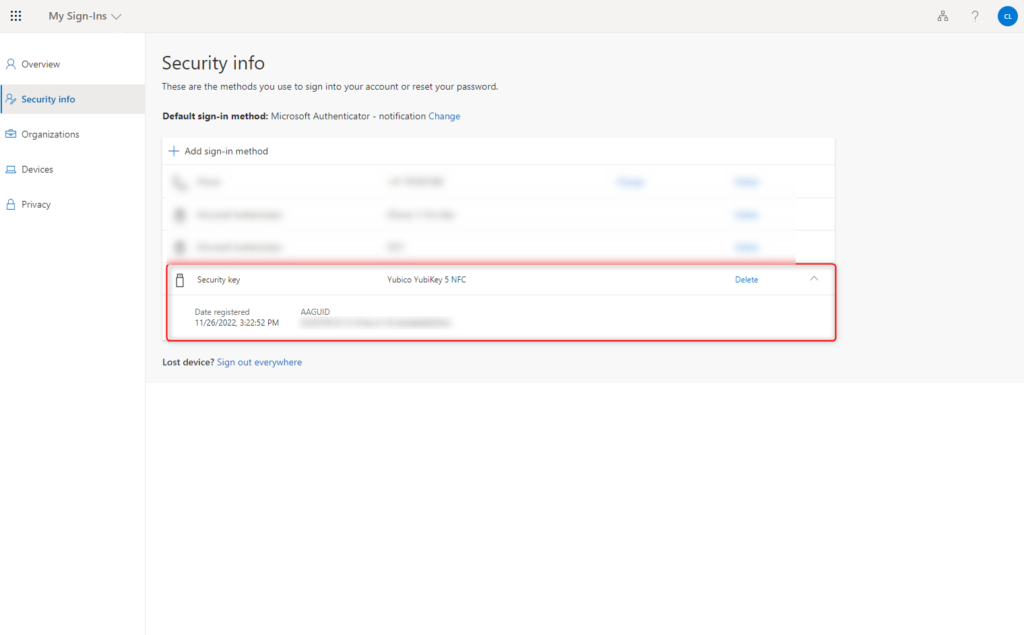
Select Security info
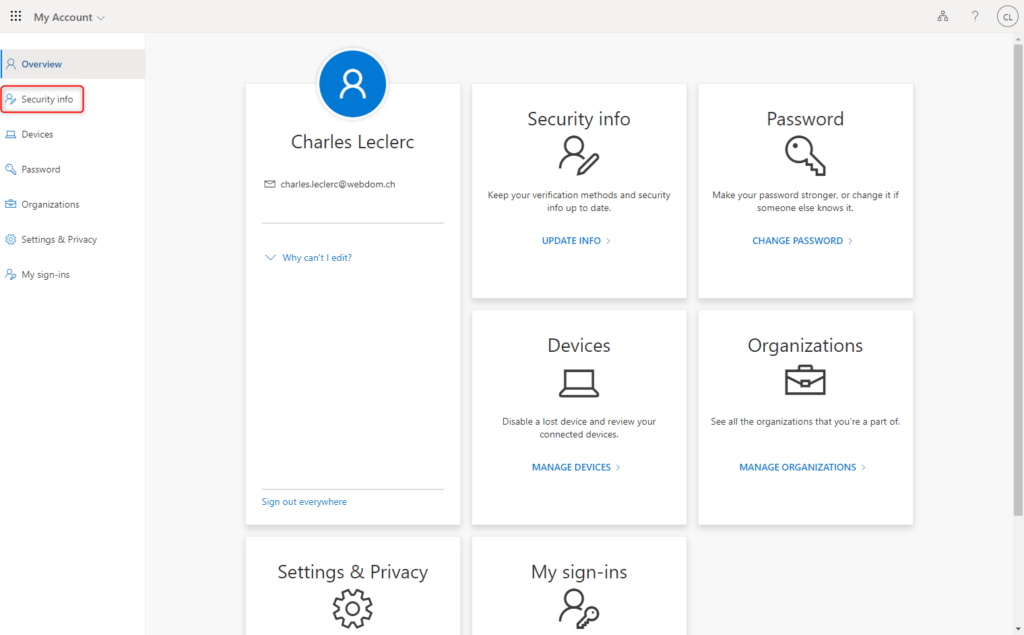
Start registration for the YubiKey security key by clicking Add sign-in method.
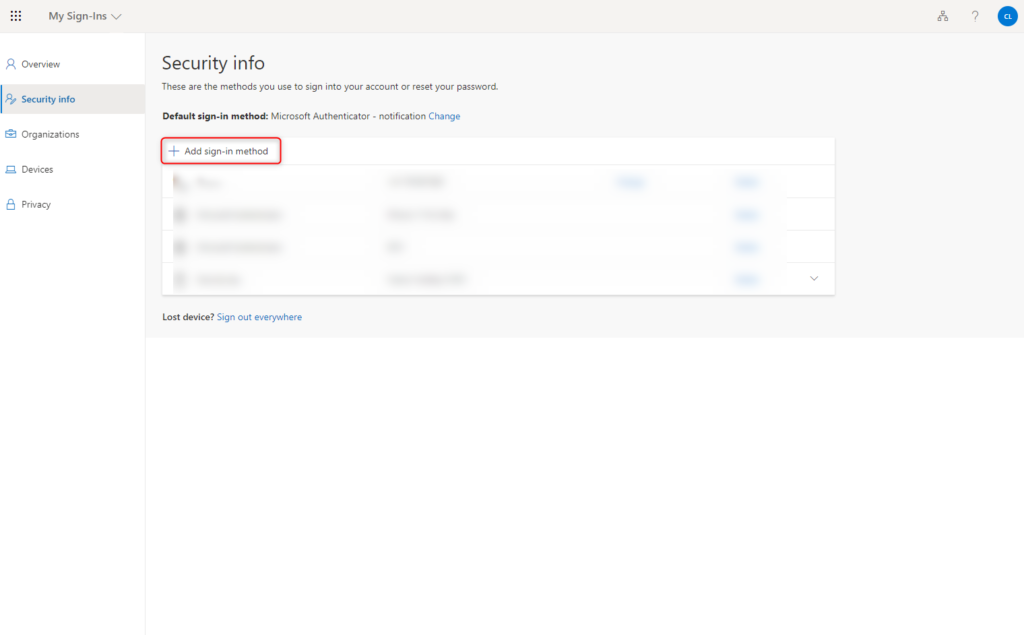
Select method Security key.
The Security key option is not visible in Microsoft Entra ID until about 15 minutes after initial activation.
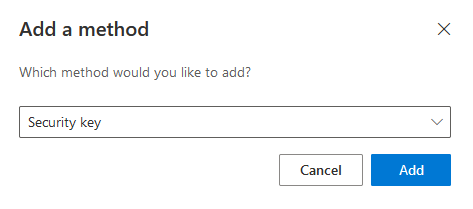
In order for the YubiKey security key to be setup, the user must sign in with multi-factor authentication.
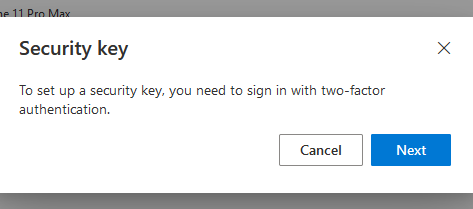
Choose the type of connection method for the security key (USB or NFC).
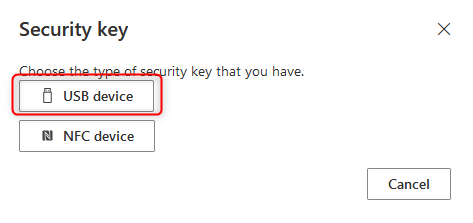
Connect YubiKey security key to the device and click Next.
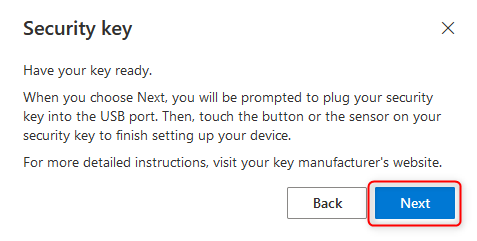
The security key will now be connected.
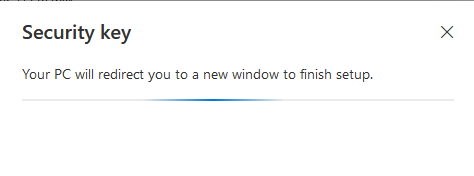
The connected security key is setup for the currently signed in user.


To continue setting up the YubiKey security key, simply touch it.

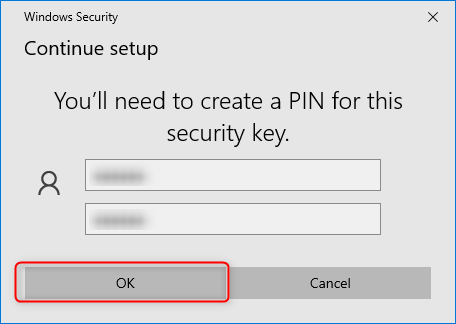
Set a PIN for the security key.
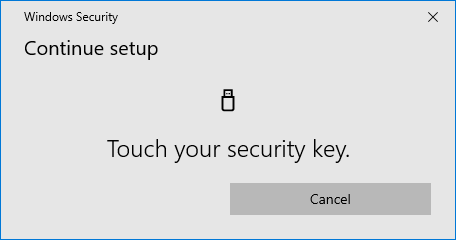
Touch the security key again.
Finally, assign a meaningful name for the YubiKey security key.
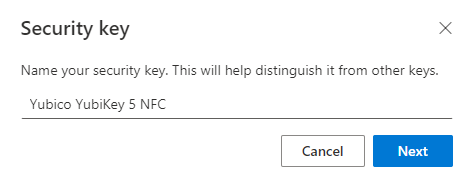
The YubiKey FIDO2 security key is now successfully setup and can be used for sign in.
The security key is displayed as active for sign in.
Passwordless Sign In with YubiKey 5 Security Key
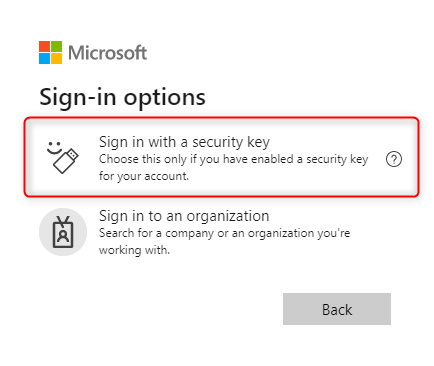
In the sign in window for Microsoft Azure, Microsoft 365 or Enterprise applications with Microsoft Entra ID authentication, select Sign-in options.
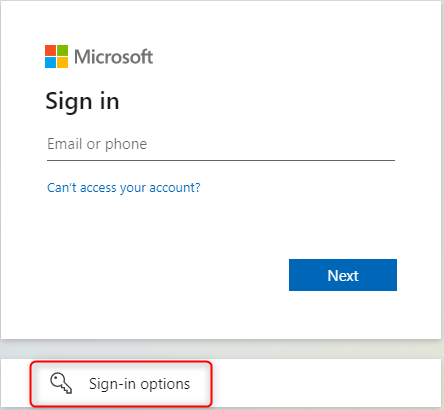
Select Sign in with a security key and connect the security key to device.
(Optional) If multiple modern authentication methods are active on the device, a prompt will appear. Select the Security key.
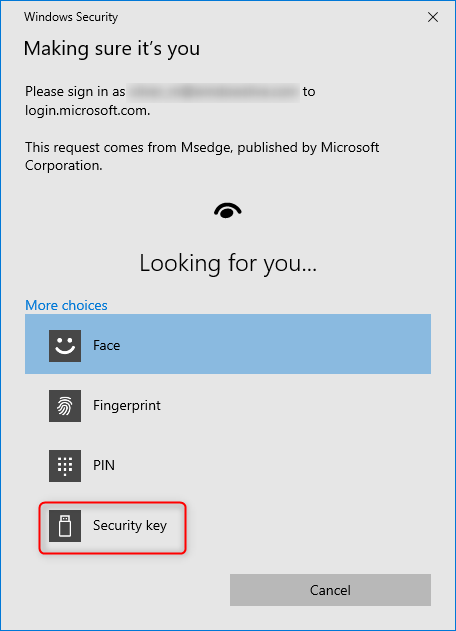
Touch the security key and enter PIN, after PIN entry touch security key again.


(Optional) If multiple identities exist for the security key, select the desired identity.
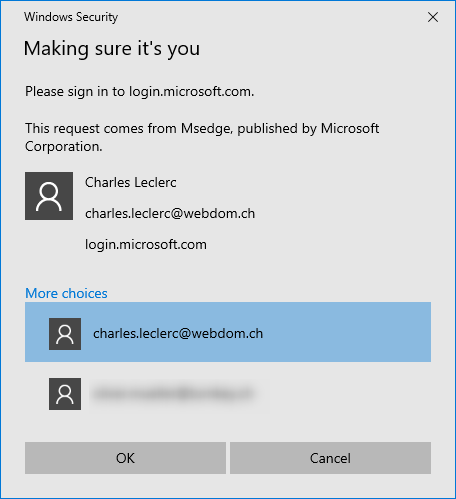
The sign in with the YubiKey security key is successfully performed.