A Temporary Access Pass (TAP) is a time-limited passcode that can be configured for single or multiple use. The Temporary Access Pass (TAP) allows the user to securely sign in to the Microsoft Cloud within a defined time period to set up additional authentication methods. These secure authentication methods include passwordless methods such as FIDO2 security keys or the Microsoft Authenticator App. The limited time period for access authorisations makes the Temporary Access Pass (TAP) an indispensable tool for security guidelines and compliance requirements.
This blog post explains how to activate, configure, and use the Temporary Access Pass (TAP).
Prerequisites and Licensing
The following licence is required for the Temporary Access Pass (TAP) feature in Microsoft Entra ID:
- Microsoft Entra ID P1 or higher
The licence is part of Microsoft 365 Business Premium and many more.
Enabling and configuration of the Temporary Access Pass (TAP) requires the role of Authentication Policy Administrator.
Several roles are suitable for creating a passcode for the Temporary Access Pass: Global Administrator, Privileged Authentication Administrator or Authentication Administrator. A detailed description of the possibilities of each role can be found in the following chapter: Create Temporary Access Pass
Enable Temporary Access Pass policy
Before users can sign-in with a Temporary Access Pass, the Temporary Access Pass policy must be enabled and it must be defined which users or groups can use a Temporary Access Pass to sign-in. This configuration is done in the Microsoft Entra admin center (https://entra.microsoft.com).
Enable Temporary Access Pass in Protection > Authentication methods > Policies.
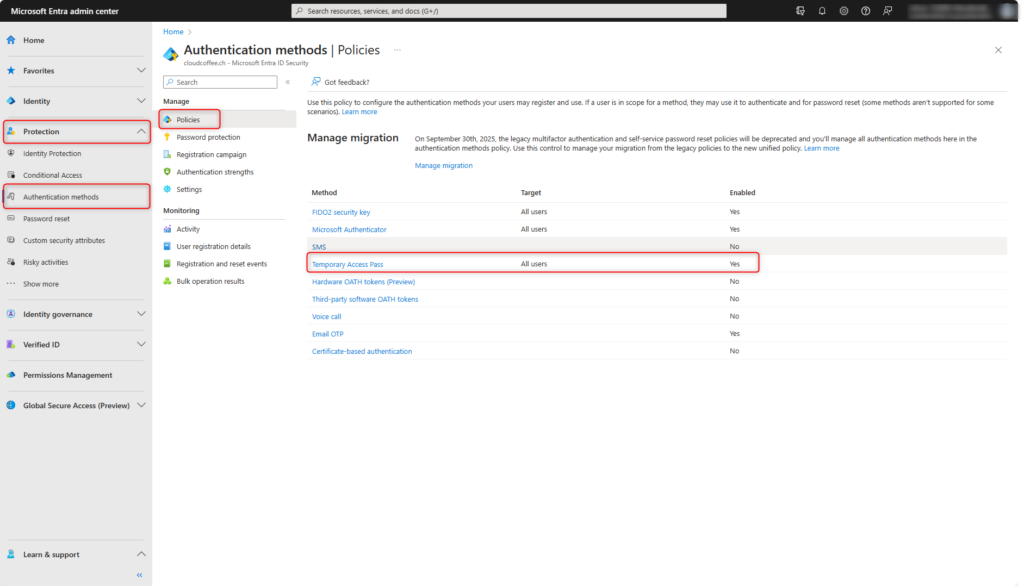
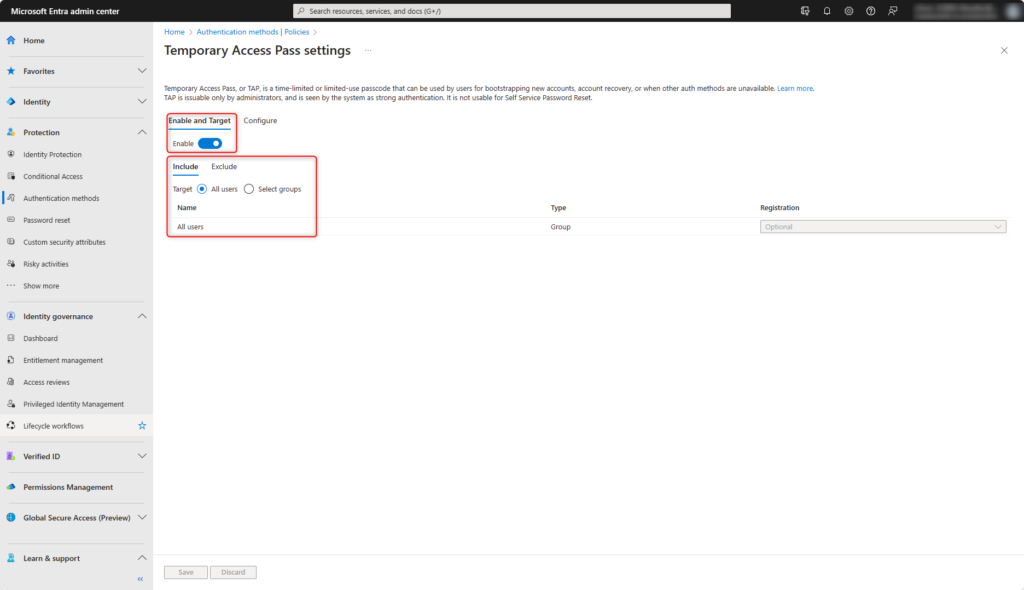
Enable Temporary Access Pass and select users or groups who are authorised to use this sign-in method.
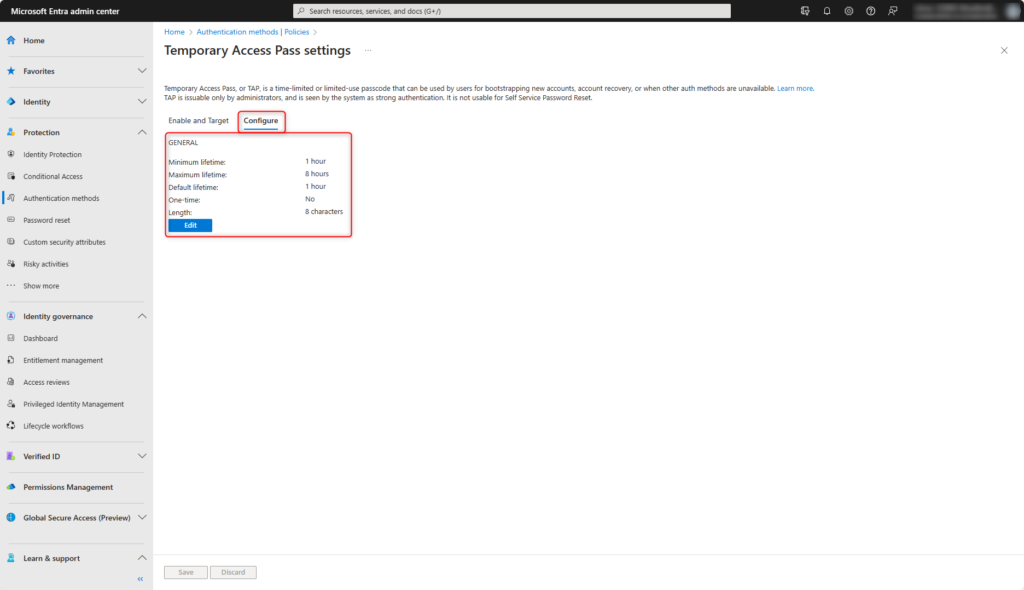
Optionally, adjust the default settings of the Temporary Access Pass under Configure.
| Setting | Default | Values | Comments |
| Minimum lifetime | 1 hour | 10 – 43.200 minutes (30 days) | Minimum number of minutes for which the Temporary Access Pass is valid |
| Maximum lifetime | 8 hours | 10 – 43.200 minutes (30 days) | Maximum number of minutes for which the Temporary Access Pass is valid |
| Default lifetime | 1 hour | 10 – 43.200 minutes (30 days) | |
| One-time use | False | True / Fase | If the policy is set to No, the Temporary Access Pass can be used either once or multiple times during its validity period. If the policy is set to Yes, the Temporary Access Pass can only be used once during its validity period. |
| Length Passcode | 8 characters | 8-48 characters |
Hint
Set the One-time value to No so that each time a Temporary Access Pass is created, it can be individually defined whether it can be used once or several times during the validity period and thus better fulfil the security guidelines and compliance requirements.
Create Temporary Access Pass
After the policy has been enabled, it is possible to create a Temporary Access Pass for an authorized user in Microsoft Entra ID. Depending on the role, different administrators can perform these actions. The following roles can perform the following actions with regard to a Temporary Access Pass:
- Global Administrator can create, view and delete a Temporary Access Pass for any user except itself.
- Privileged Authentication Administrator can create, view and delete a Temporary Access Pass for administrators and members with the exception of themselves.
- Authentication Administrators can create, view and delete a Temporary Access Pass for members with the exception of themselves.
- Global Reader can view the details of the Temporary Access Pass for users, but without being able to read the passcode itself.
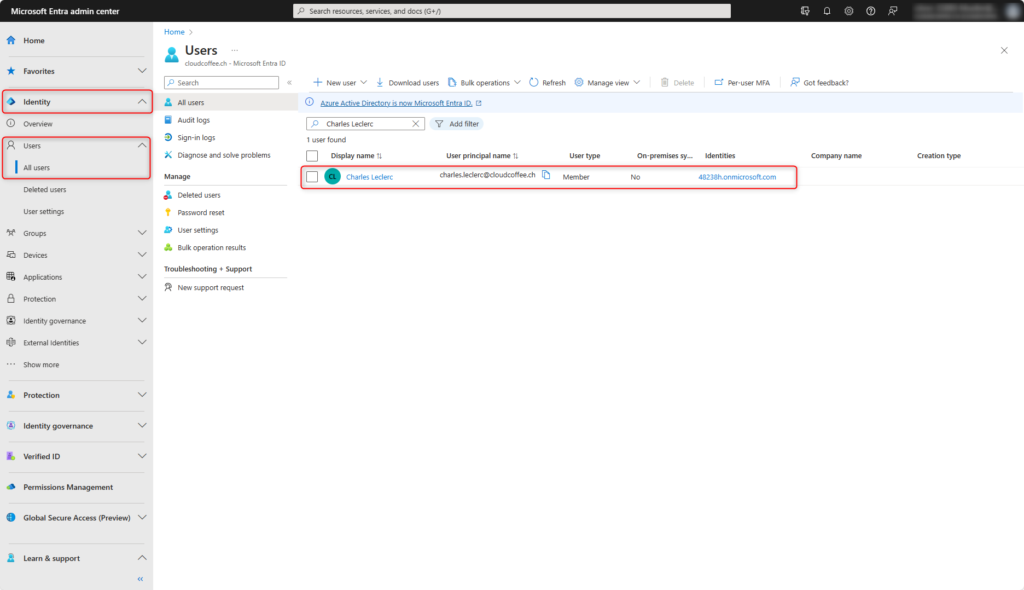
A user with an authorised role creates a Temporary Access Pass in the Microsoft Entra admin center (https://entra.microsoft.com)
Select user in Identity > Users > All users
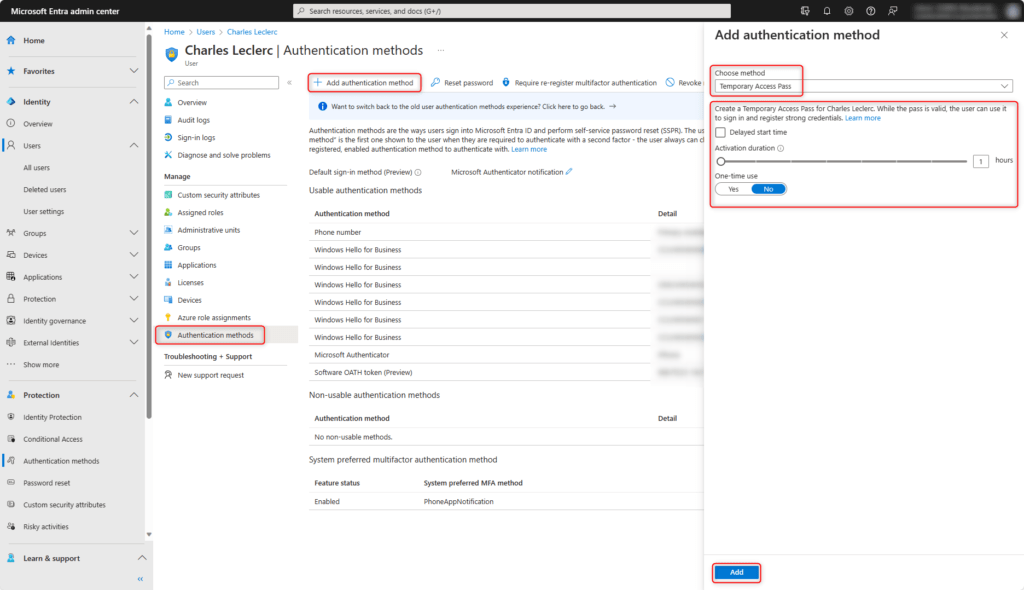
Authentication methods > Add authentication method > Temporary Access Pass
The delayed start time, activation duration and single or multiple use can be customised to your own requirements.
To finish, click on Add.
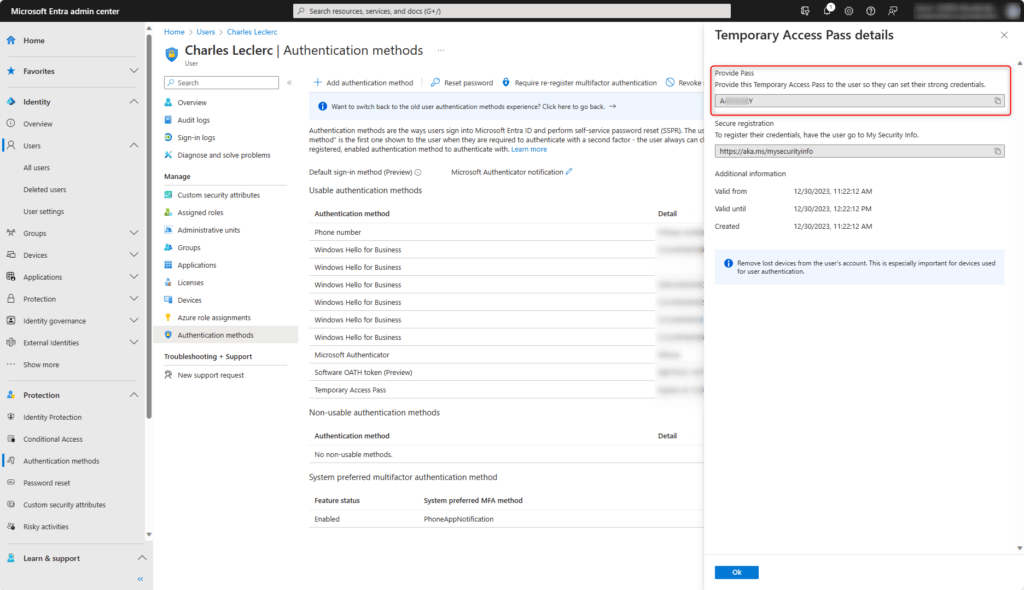
The details of the Temporary Access Pass are now shown. The passcode is shown only once and cannot be read again after leaving the window. So please make a note.
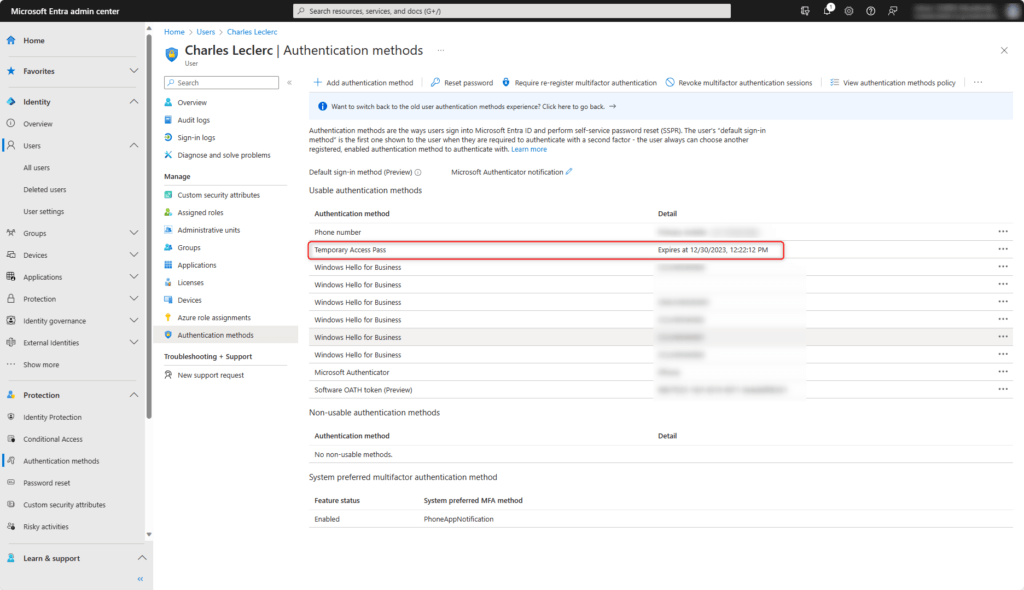
The user can now sign-in with the created passcode.
Use Temporary Access Pass
Usually, a user registers authentication methods during the first signin. The Temporary Access Pass is therefore perfect for setting up or updating multifactor-, passwordless-, or phishing-resistant authentications without having to perform additional security verificatoins.
Registering authentication methods
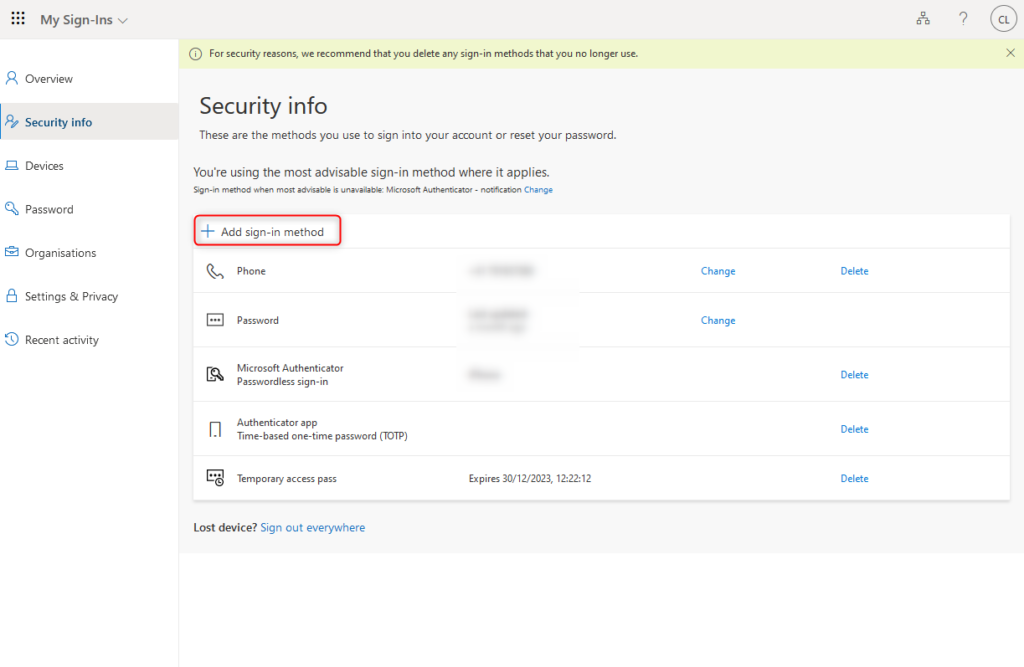
The registration of authentication methods is done at https://aka.ms/mysecurityinfo. Users can also update existing authentication methods here.
If a user account has activated a Temporary Access Pass, the user automatically uses this authentication method when sign-in.
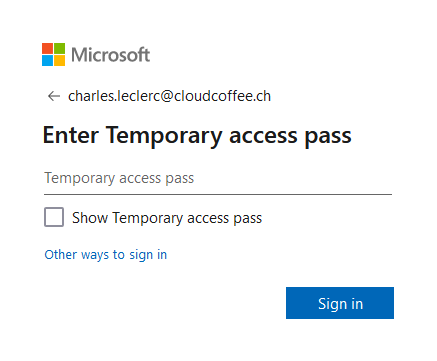
After successfull sign-in, the user can now register or update passwordless authentication methods such as FIDO2 security keys or Microsoft Authenticator App.
Users who update their authentication methods due to lost credentials or devices should ensure that the old authentication methods are removed here.
Good to know
Registering a security key (FIDO2)
If a one-time Temporary Access Pass is used to register a security key (FIDO2), the user must complete the registration within 10 minutes of signing in with the one-time Passcode. This restriction does not apply to a Temporary Access Pass created for multiple uses.
Follow me on LinkedIn to always stay updated on my recent posts.
Was this post helpful to you? Show your enthusiasm with the delightful aroma of a freshly brewed coffee for me!

