The Microsoft Entra Conditional Access for authentication flows regulates the use of the device code flow and authentication transfer. The device code flow is used to authenticate devices that do not have a browser or whose input is restricted, such as smart TVs, IoT devices, or printers. The device code flow represents a high-risk authentication flow, which could be exploited in phishing attacks or to gain access to corporate resources on unmanaged devices. The authentication transfer is a new flow that provides a seamless way to transfer the authenticated state from one device to another. In the desktop version of Outlook, users might be presented with a QR code. When they scan it on their mobile device, their authenticated state is transferred to the mobile device.
This post demonstrates blocking the device code flow and authentication transfer using Microsoft Entra Conditional Access.
Prerequisites and Licensing
For the feature Microsoft Entra Conditional Access in Microsoft Entra, the following license is required:
- Microsoft Entra ID P1 or higher
This license is included in various plans, including Microsoft 365 Business Premium and more.
Block device code flow or authentication transfer
A Microsoft Entra Conditional Access policy is created to block the device code flow or authentication transfer.
Sign in to the Microsoft Entra admin center (https://entra.microsoft.com/).
Protection > Conditional Access > Policies > New policy
Enter Name for policy, e.g. Authentication flows
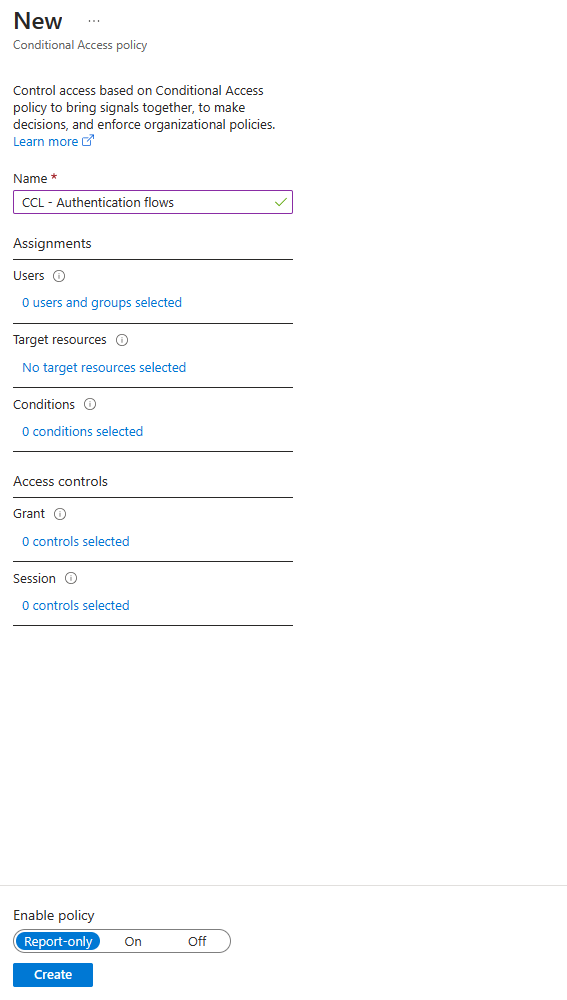
Select Users and include All users in the policy.
If necessary, exclude emergency access accounts (Break Glass Accounts).
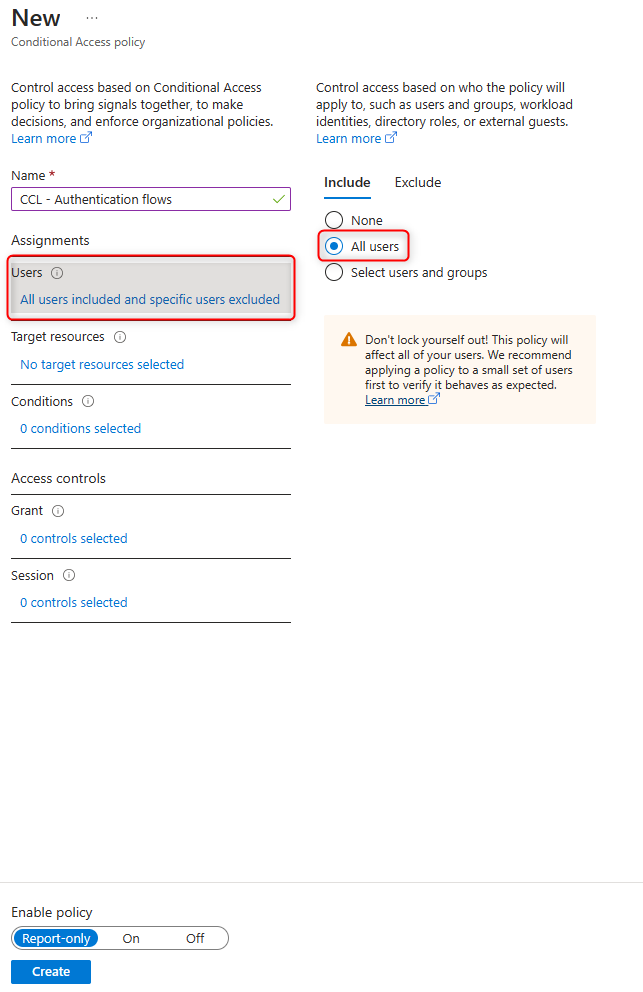
Select Target resources and enable All cloud apps.
Select Conditions > Authentication flow
Enable Device code flow and/or Authentication transfer

Select Grant and enable Block access.
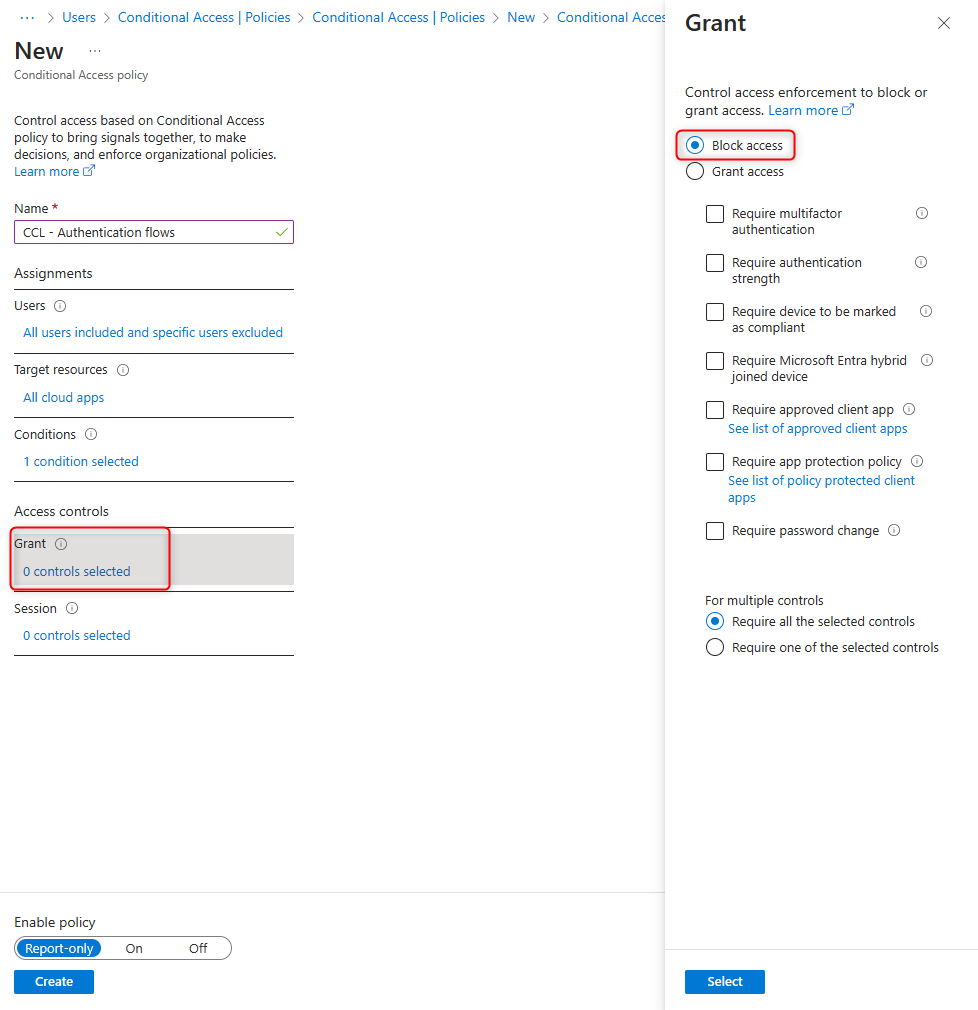
Activate the policy with On and save by clicking Create.
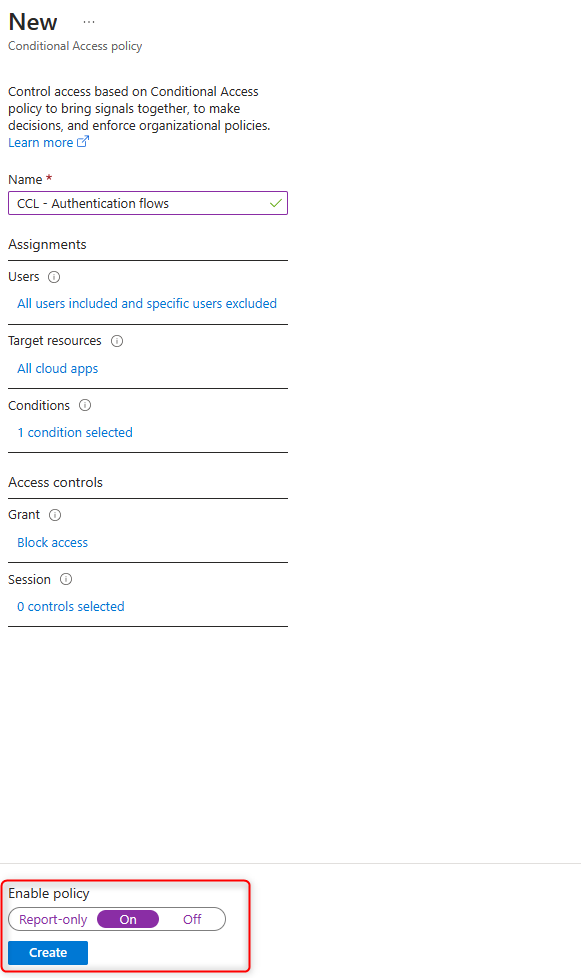
The policy for blocking device code flow and/or authentication transfer with authentication flows has been set up.
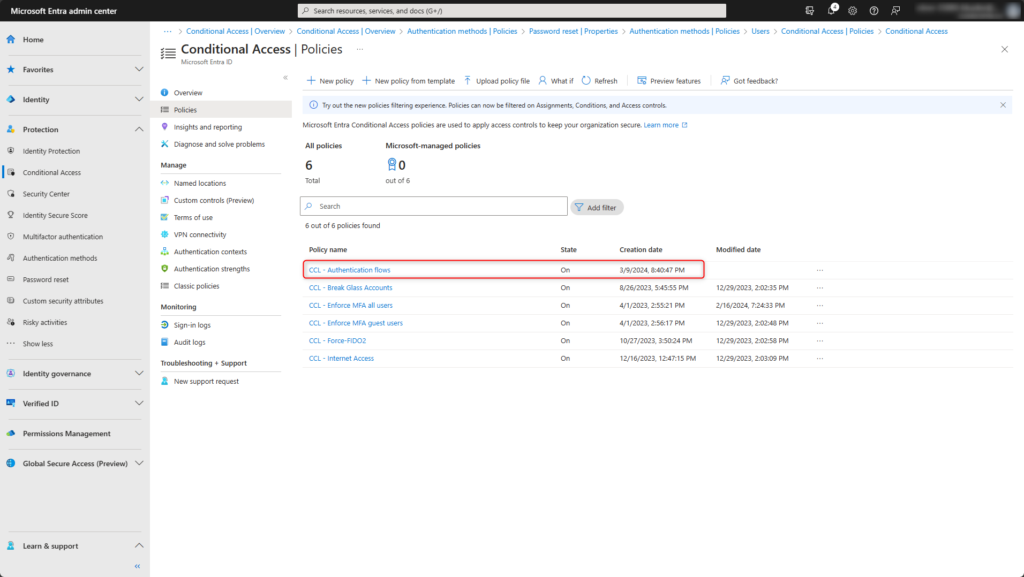
Test configuration
To verify the new Microsoft Entra Conditional Access policy, a sign-in is performed using a device code flow. Azure CLI is excellent for this purpose. The following PowerShell cmdlet initiates the sign-in.
1 | az login --use-device-code |
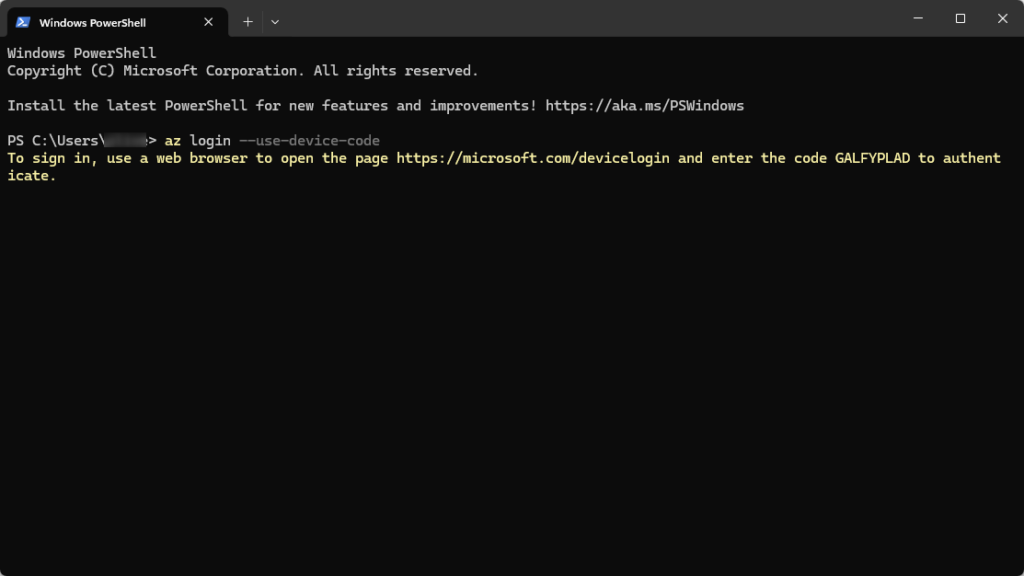
Open the website https://microsoft.com/devicelogin and insert Code.
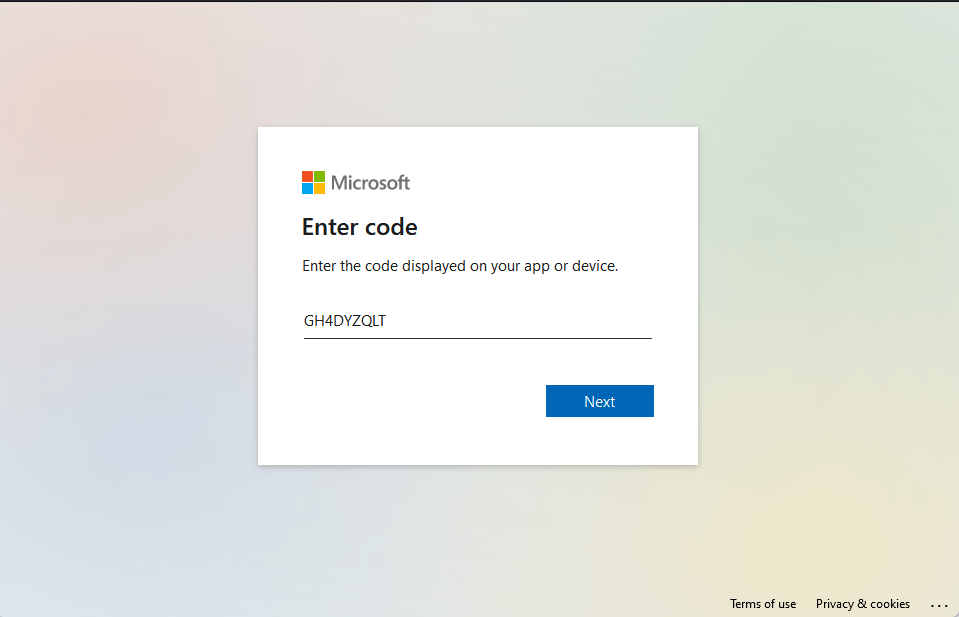
Perform sign-in.

Even though sign-in is successful, the Microsoft Entra Conditional Access policy created prevents sign-in.
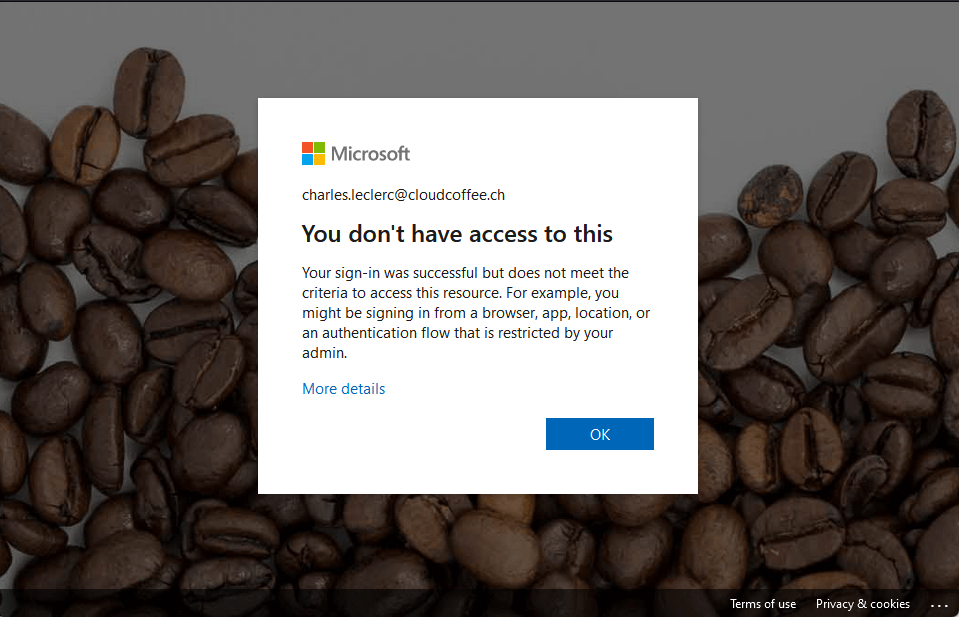
The sign-in attempt is written to the Microsoft Entra ID sign-in log, see the section Monitoring authentication flow events.
Monitoring authentication flow events
All authentication flow events are written to the Microsoft Entra ID sign-in log.
Sign in to the Microsoft Entra admin center (https://entra.microsoft.com/).
Identity > Monitoring & health > Sign-in logs
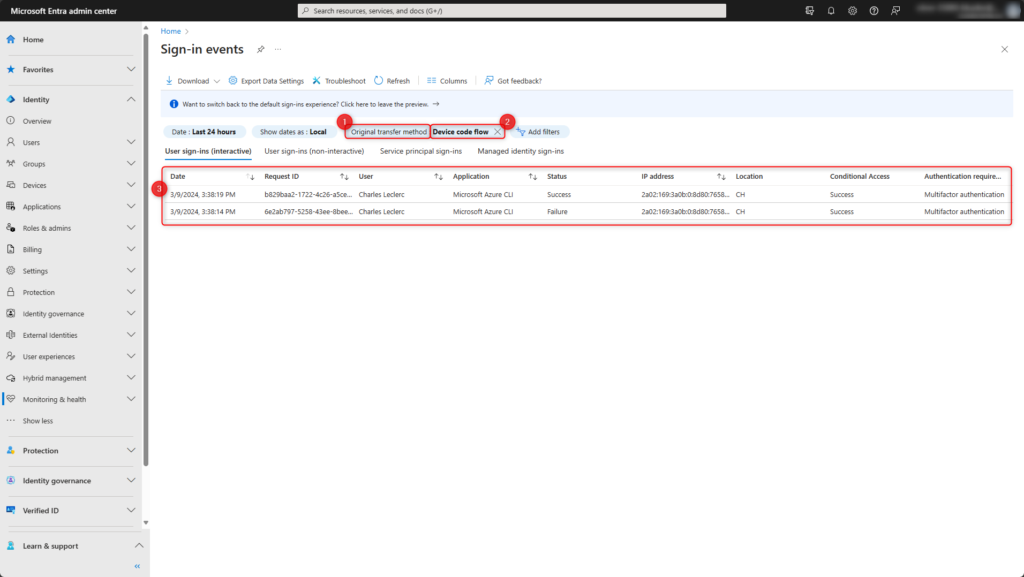
Set filter Original transfer method (1) to Device code flow (2) or Authentication transfer (2). All successful and error events (3) will be shown.
Follow me on LinkedIn to always stay updated on my recent posts.
Was this post helpful to you? Show your enthusiasm with the delightful aroma of a freshly brewed coffee for me!

