Hardening your Identities: Microsoft Authenticator device-bound passkey
Last Updated on 18. January 2025
A device-bound passkey is an advanced security feature implemented in Microsoft Authenticator. It is a unique security key that is tied to a specific device. When a user logs in to their account, they use this key to verify their identity. Since the key is bound to the device, no one else can access the user’s account, even if they know the password, unless they also have access to the device.
This technology provides a strong authentication method that is both cost-effective and user-friendly. Here are some advantages:
- Phishing-Resistant: Device-bound passkeys are phishing-resistant
- Device-Bound: The passkey doesn’t leave the device on which it was created
- Cost-Effective: Microsoft Authenticator device-bound passkey come at no additional cost
- No More Passwords: With passkeys, users don’t have to remember complex passwords
- Ease of Use: The passkey is easy to use. Once set up, users just need to unlock their device and approve the notification
With this technology, users can effectively protect their digital identities and navigate securely in the digital world. It represents a significant step toward a safer digital future.
This article outlines the necessary configuration steps to rollout the Microsoft Authenticator device-bound passkey and create a passkey for a user.
At the time of publishing this article, Microsoft Authenticator device-bound passkey is still in the preview phase. The article will be continuously updated.
Prerequisites and Licensing
Licenses
For the use of Microsoft Authenticator device-bound passkey, no paid license is required. A license from Microsoft Entra ID Free is sufficient. This license is part of every Microsoft tenant.
User account
The user account that sets up the passkey is configured for multi-factor authentication.
Devices
- iOS 17 or later
with the latest version of Microsoft Authenticator
If Microsoft Authenticator is not the primary password manager used on the device, iOS 18 is recommended. This operating system allows the simultaneous use of multiple password managers. - Androis 14 or later
with the latest version of Microsoft Authenticator
Enable passkey (FIDO2) authentication method
The Passkey (FIDO2) authentication method is configured in the Microsoft Entra admin center.
Sign in to the Microsoft Entra admin center (https://entra.microsoft.com/) > Protection > Authentication methods > Policies and select Passkey (FIDO2).

In the Enable and Target tab, toggle the Enable switch and select All Users.
If necessary, you can also add individual security groups.

In the Configure tab, the following options can be set:
Allow self-service set up
This option must be enabled for users to set up the Microsoft Authenticator device-bound passkey.
Enforce attestation
This option ensures that security keys adhere to FIDO Alliance Metadata.
Note that the preview for Microsoft Authenticator device-bound passkey does not support this feature and should be disabled.
Enforce key restriction
This option must be enabled for using Microsoft Authenticator device-bound passkey during the preview phase.
Restrict specific keys
This option allows you to restrict the use of specific FIDO2 security keys.
An overview of the common AAGUIDs is provided by Clayton Tyger with the Entra Compatible Attestation FIDO Key Explorer.
Microsoft Authenticator (Preview)
This option must be enabled and directly enters the AAGUIDs of the Microsoft Authenticator for iOS and Android.
The following AAGUID entries are included:
Authenticator for iOS: 90a3ccdf-635c-4729-a248-9b709135078f
Authenticator for Android: de1e552d-db1d-4423-a619-566b625cdc84

Click Save and then users can set up device-bound passkeys in Microsoft Authenticator.

Set up Microsoft Authenticator device-bound passkey
Every user sets up the Microsoft Authenticator device-bound passkey independently. This guide explains how to set up a Microsoft Authenticator device-bound passkey for an Apple iPhone.
Prepare Apple iPhone
Install the latest version of Microsoft Authenticator on Apple iOS 17 or later.
If multiple password managers are to be used simultaneously, iOS 18 is required.
On an Apple iPhone with iOS 18, the following options must be configured under Settings > General > AutoFill & Passwords:
- Enable AutoFill Passwords and Passkeys
- Use passwords and passkeys from: Authenticator

Once the Apple iPhone is prepared, the passkey can be set up.
Set up passkey for Apple iPhone
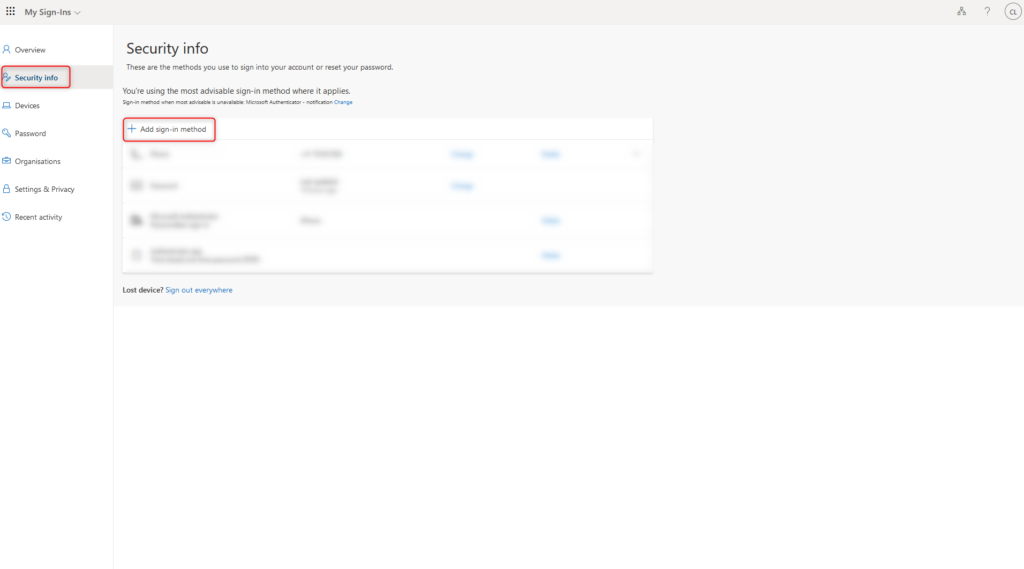
The user sign in at https://aka.ms/mysecurityinfo and clicks on Security info > Add sign-in method.
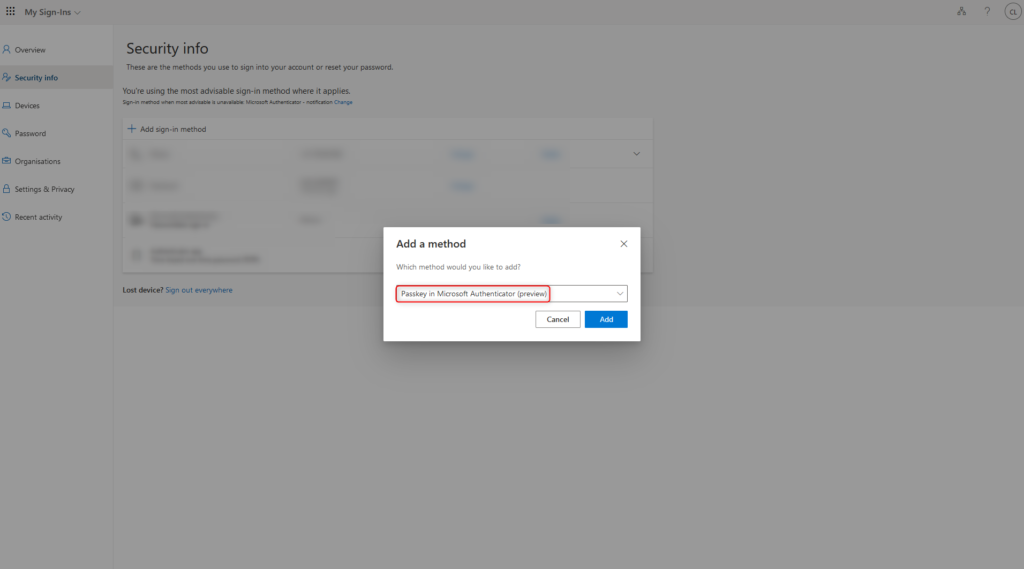
Select Passkey in Microsoft Authenticator and click on Add.
Click Next

Select iPhone or iPad

Passkey support for Microsoft Authenticator has already been enabled and can be confirmed with Continue.

Click I’m ready to set up the passkey.

Select iPhone, iPad or Android device.
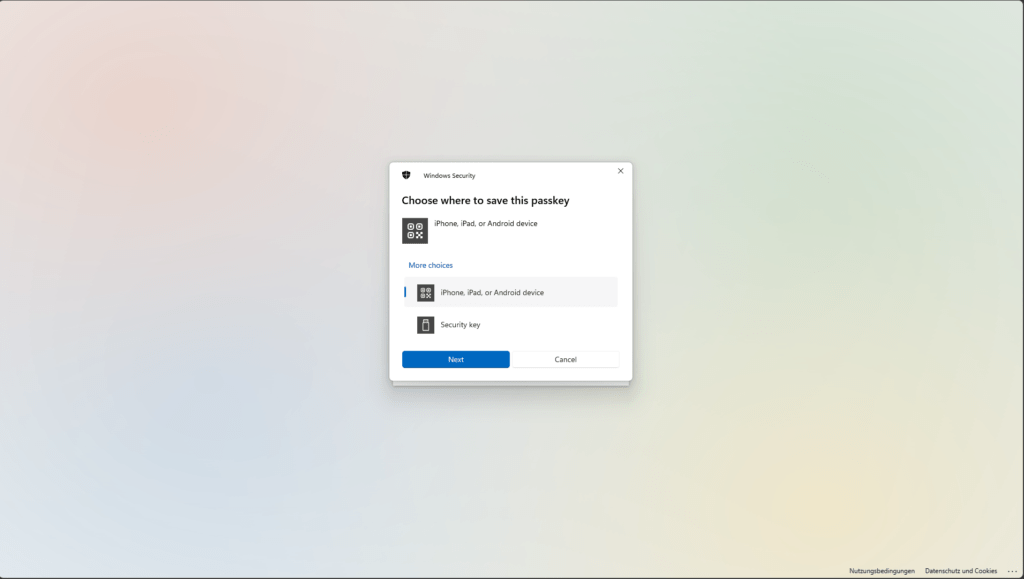
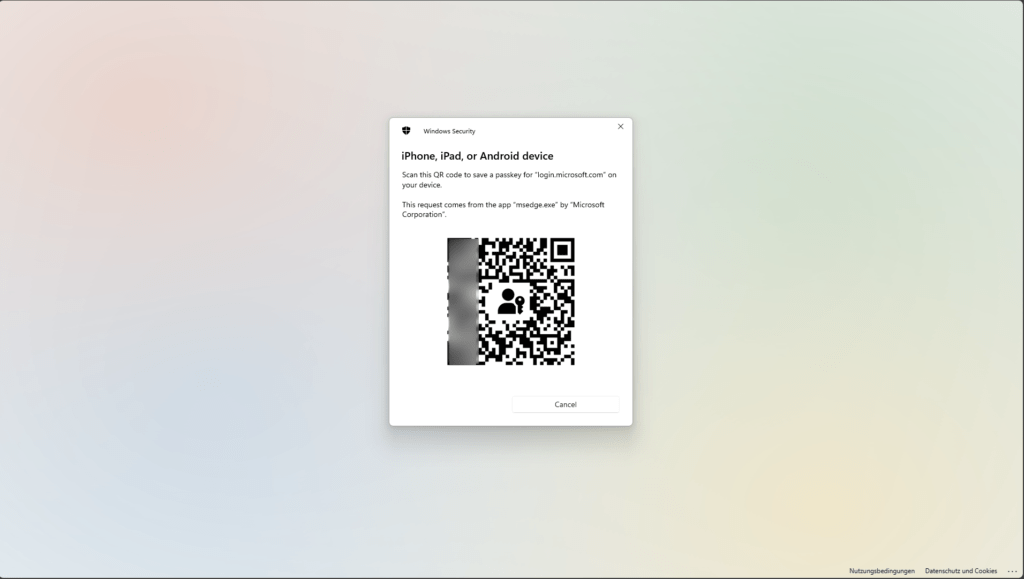
Scan QR code
Important: Scan this QR code with the Apple iPhone Camera app, not with “Scan QR code” from the Microsoft Authenticator app.
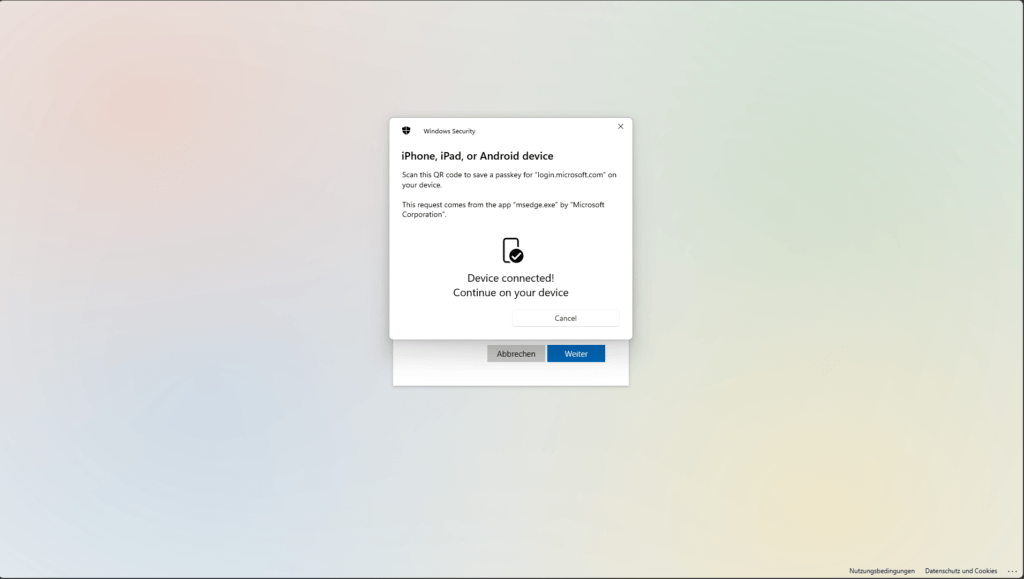
Continue with setting up the passkey on the Apple iPhone.
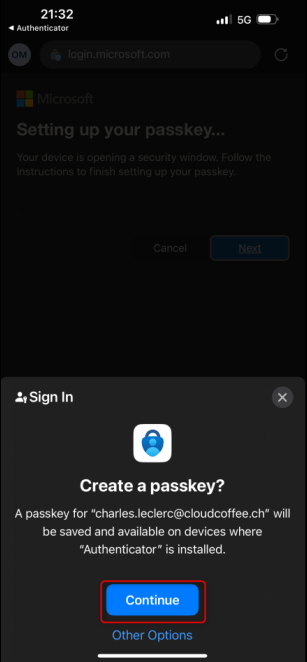
Click Continue on the Apple iPhone and set up the passkey with it.
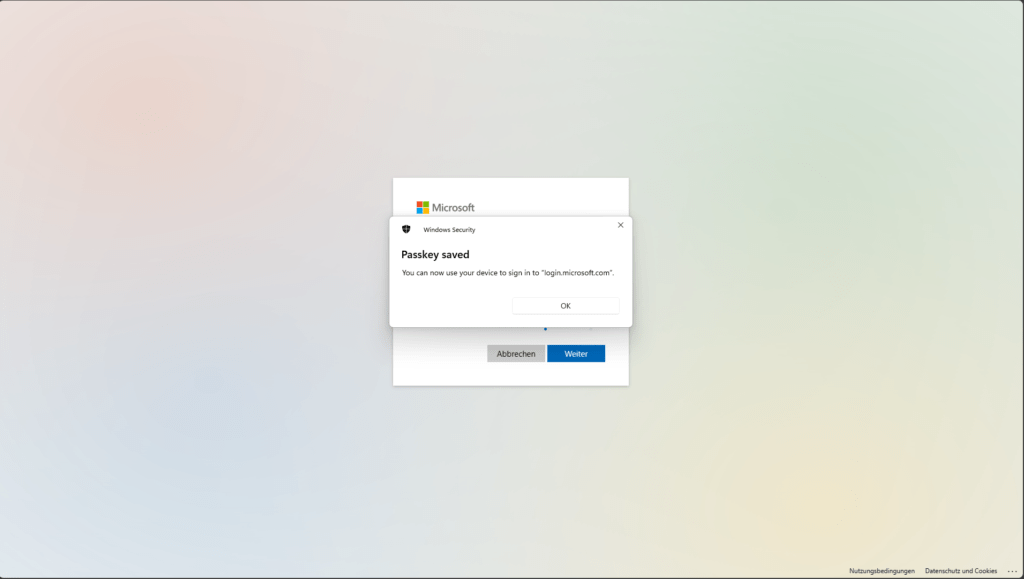
The passkey has now been successfully set up on the Apple iPhone.
Enter a friendly name for better identification of the passkey.

The passkey has now been successfully set up and can be used.

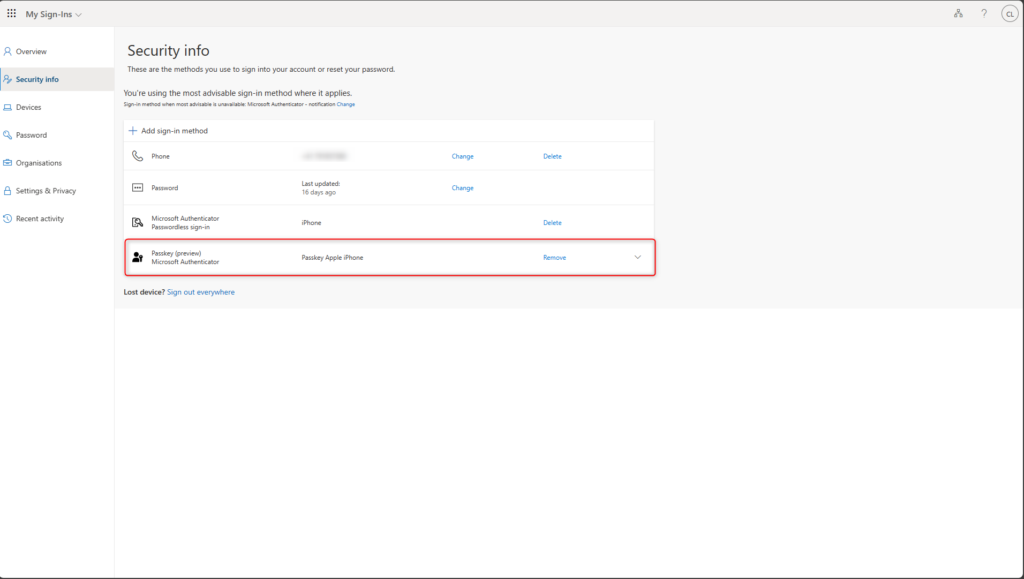
Sign in with device-bound passkey
In services from Microsoft Azure, Microsoft 365, or Enterprise applications with Microsoft Entra ID authentication, select the Sign-in options.
For example: https://aka.ms/mysecurityinfo
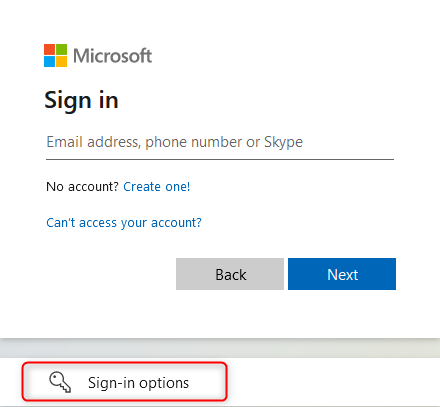
Select Face, fingerprint, PIN or security key
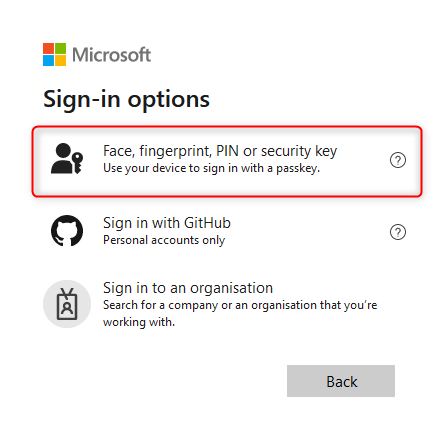
Select iPhone, iPad or Android device
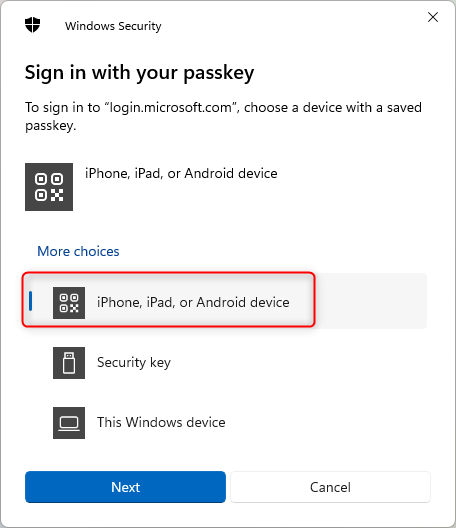
Scan the QR code with camera.

Confirm the sign in on the mobile by clicking Continue.
If multiple passkeys are stored in Microsoft Authenticator, the user account can be selected.
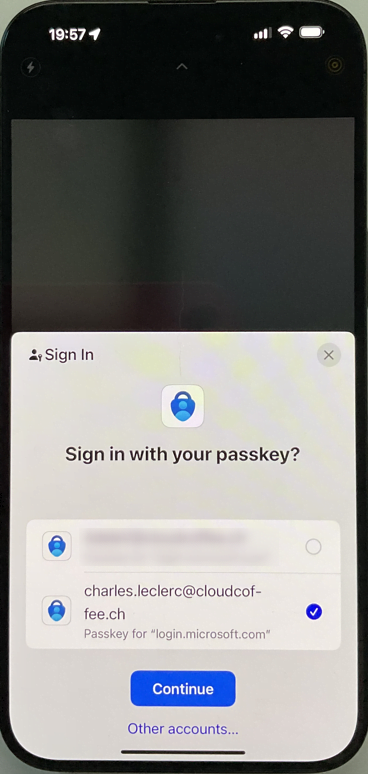
The sign-in with the Microsoft Authenticator device-bound passkey to https://aka.ms/mysecurityinfo has been successfully completed.
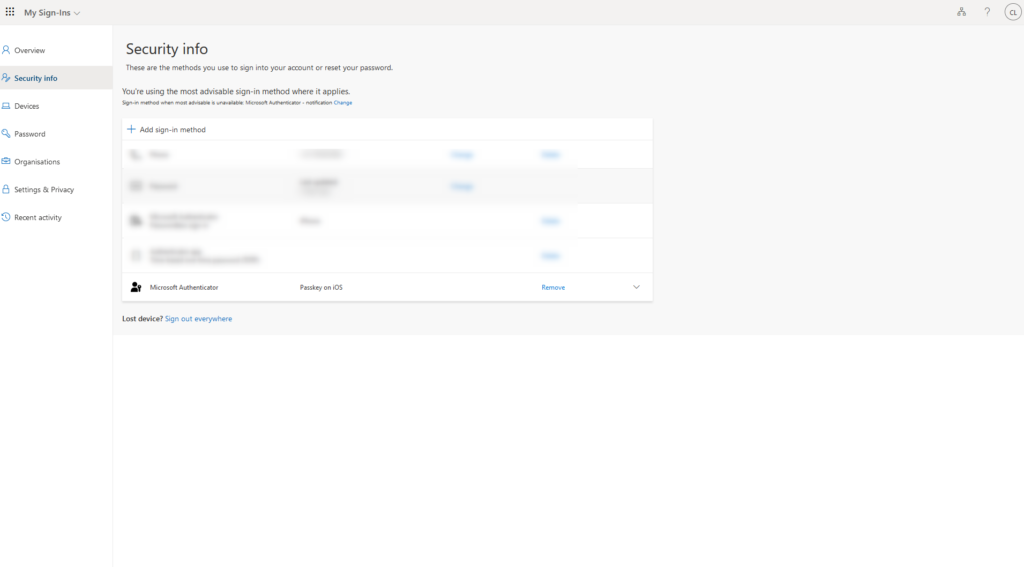
Troubleshooting
Passkey setup gets stuck
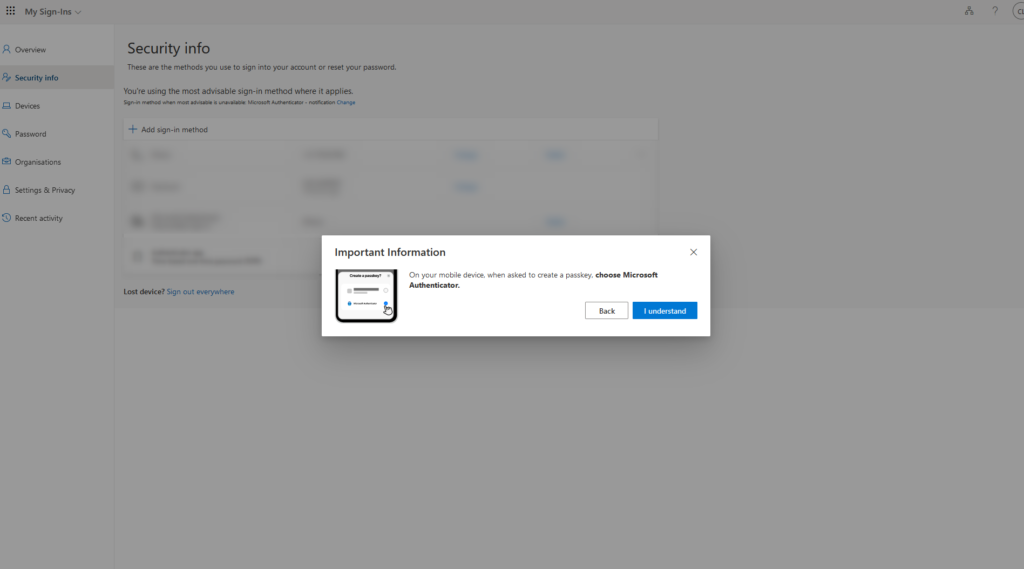
When setting up the Micosoft Authenticator device-bound passkey, the following message appears in the loop after clicking on I understand:
On your mobile device, when asked to create a passkey, choose Microsoft Authenticator.
Solution
The AAGUIDs for Microsoft Authenticator were not entered in the authentication methods of Microsoft Entra. Click here for the instructions.
Delete passkey
Delete passkey with access to device
Open the Microsoft Authenticator app and select the user whose passkey needs to be deleted

Click on Passkey (preview)

Click Delete

Select Visit link and sign in.

The security information is shown.
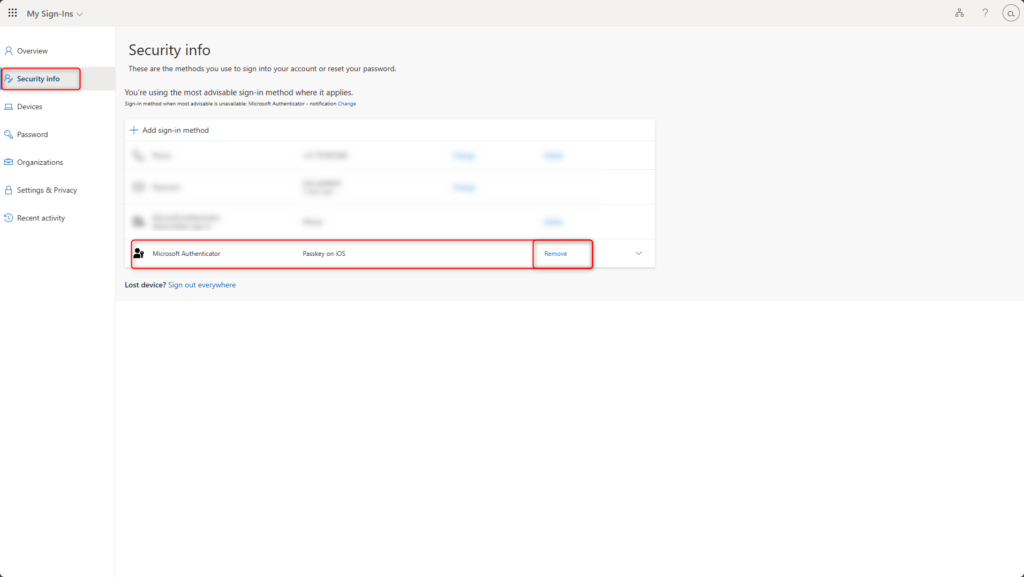
Select the passkey and delete it from the user account with Remove.
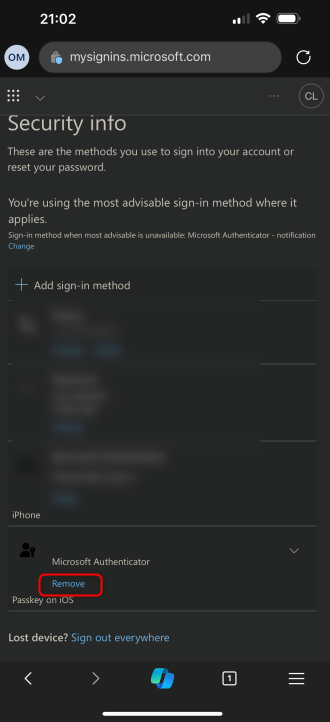
Delete passkey without access to device
If there is no longer access to the device with the Microsoft Authenticator device-bound passkey, the passkey can be removed from the personal security information.
Sign in to https://aka.ms/mysecurityinfo > Security info > passkey > Delete