Migrating from Passthrough Authentication to Password Hash Sync (PHS) synchronizes passwords from the on-premises Active Directory instance to Azure AD.
This is a considerable gain in convenience for users. From now on, they can sign in with the same credentials (user name, password and optionally with multi-factor authentication).
This increases productivity and at the same time reduces user support costs.
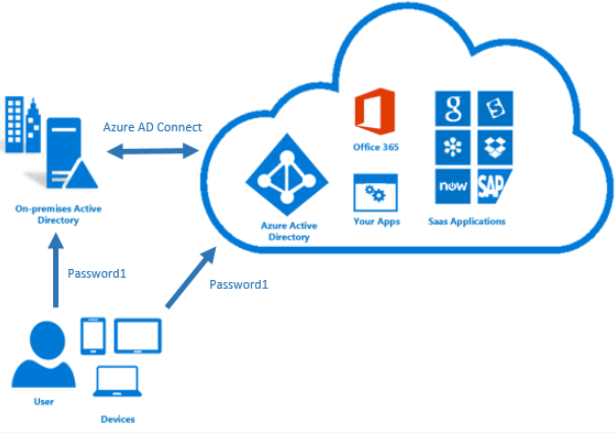
User sign in with this method works with all Azure AD integrated cloud apps, even if the local Active Directory instance is not accessible online. This can be the case, for example, due to an Internet or power outage, but also in the case of a simple restart of the services after a Windows update.
A much more important benefit of Password Hash Synchronization is security. Microsoft works with darknet investigators and judicial authority to find published user credentials. If a username and password pair is found, the corresponding Azure AD account is classified as “high risk” and the administrator is informed.
If you want to install Azure Active Directory Cloud Sync instead of Azure AD Connect, you can find the instructions here:
Installation and configuration Azure Active Directory Cloud Sync – cloudcoffee.ch
Enable Password Hash Synchronization
First, all password hashes must be synchronized.
Only if the synchronization was successful, the sign in method should be changed in a next step.
Notice:
Approximately 20,000 hashes can be synchronized per hour.
Open “Azure AD Connect” to begin the configuration
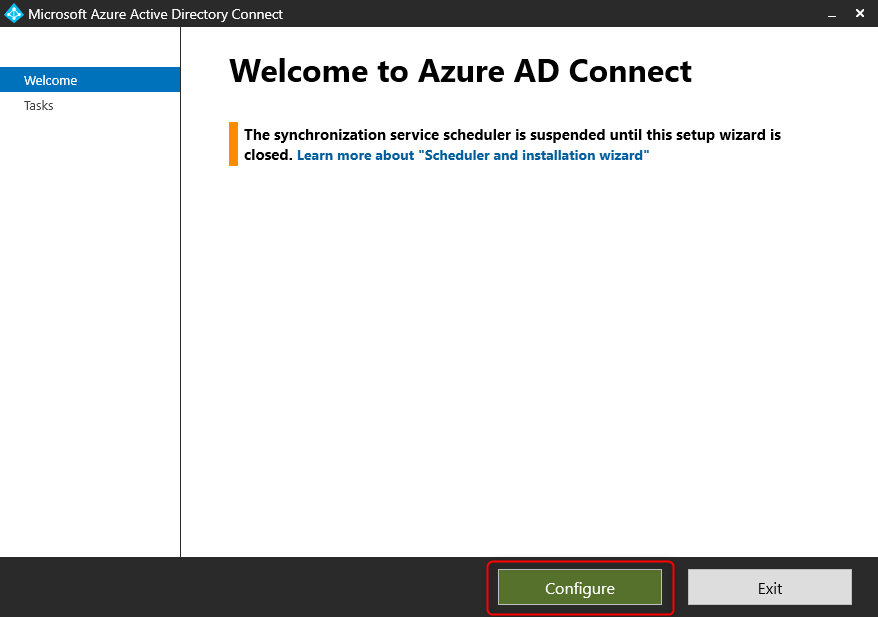
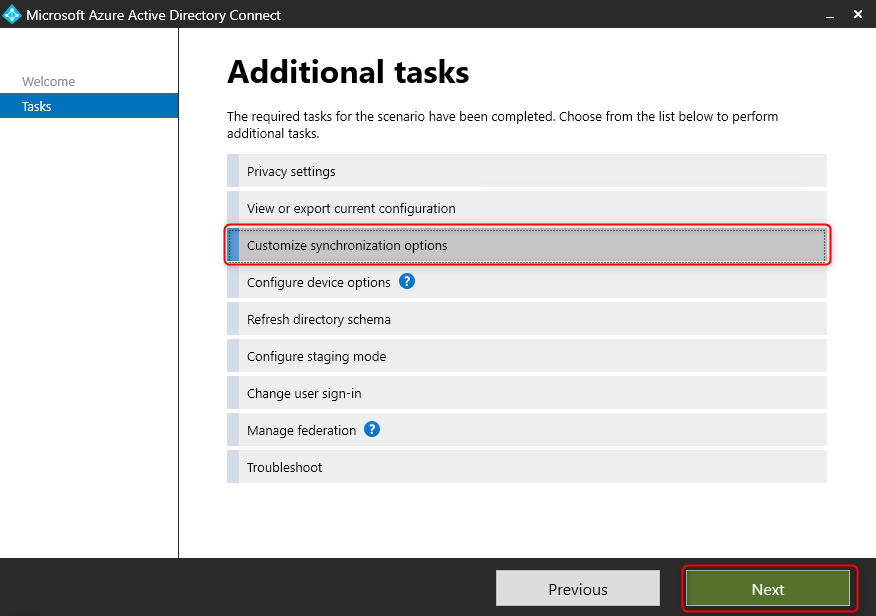
Select “Customize synchronization options”
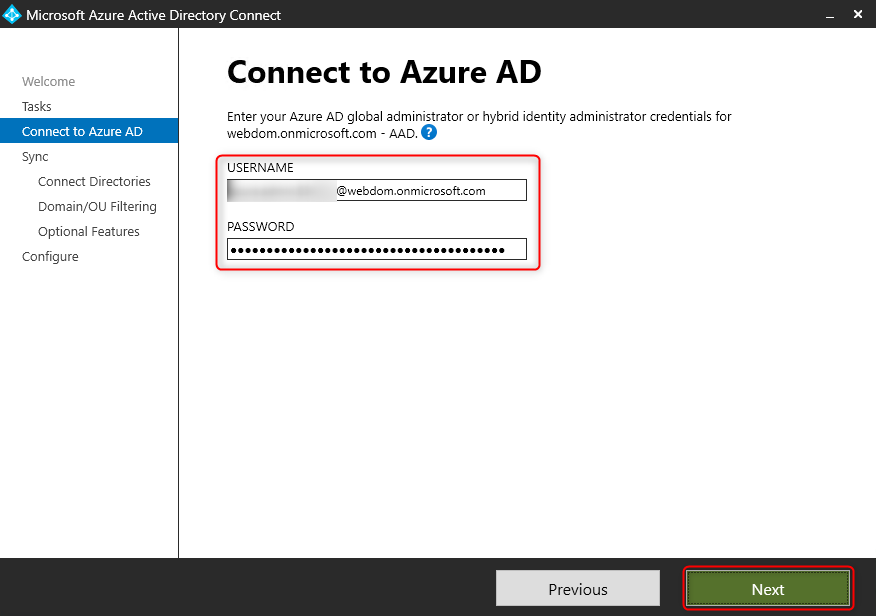
Sign in to Azure AD requires an account with global administrator privileges.
The connection to the on-premise Active Directory must be established successfully, click “Next”.
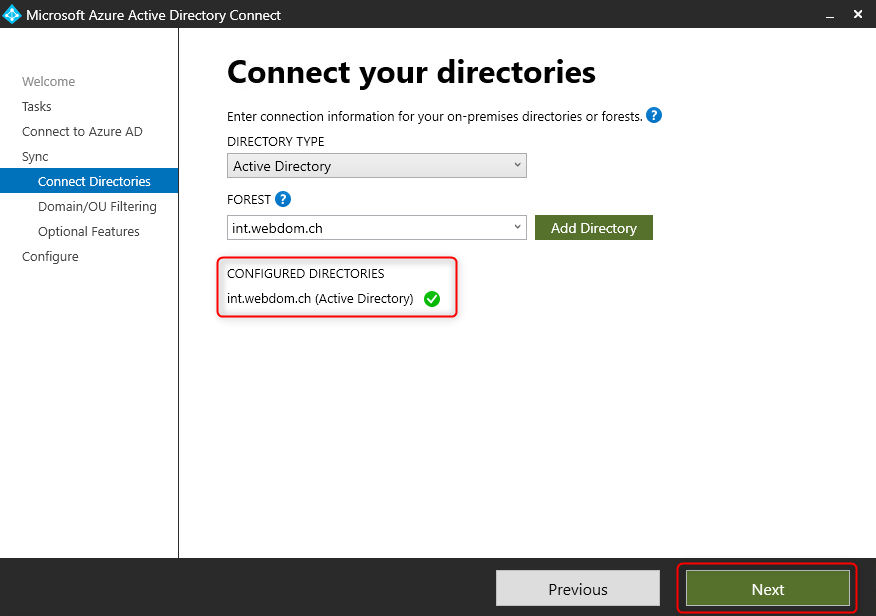
Select “Password Hash Synchronization”
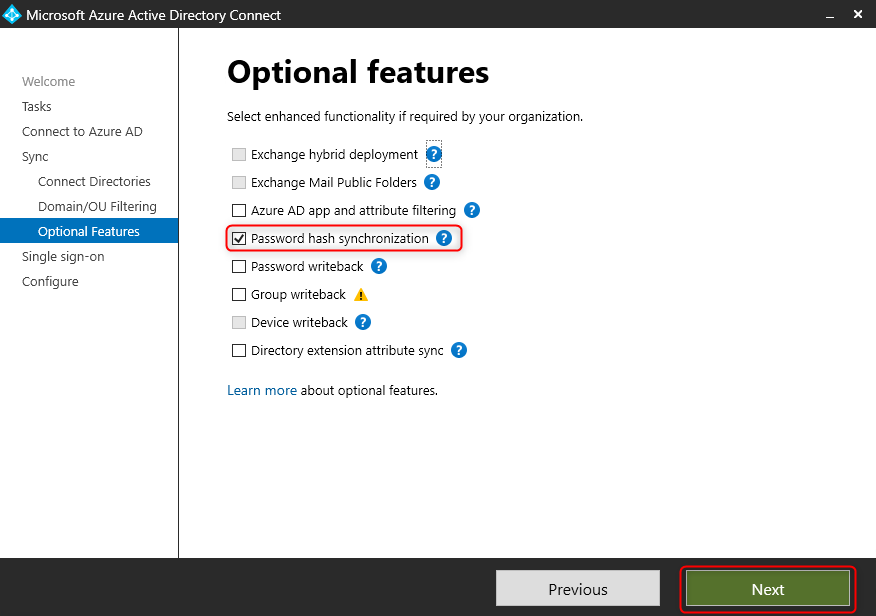
Single Sign On (SSO) increases user convenience and should be enabled.
If the connection is not established successfully, it can be established with a user account from the on-premise domain and Domain Administrator privileges.
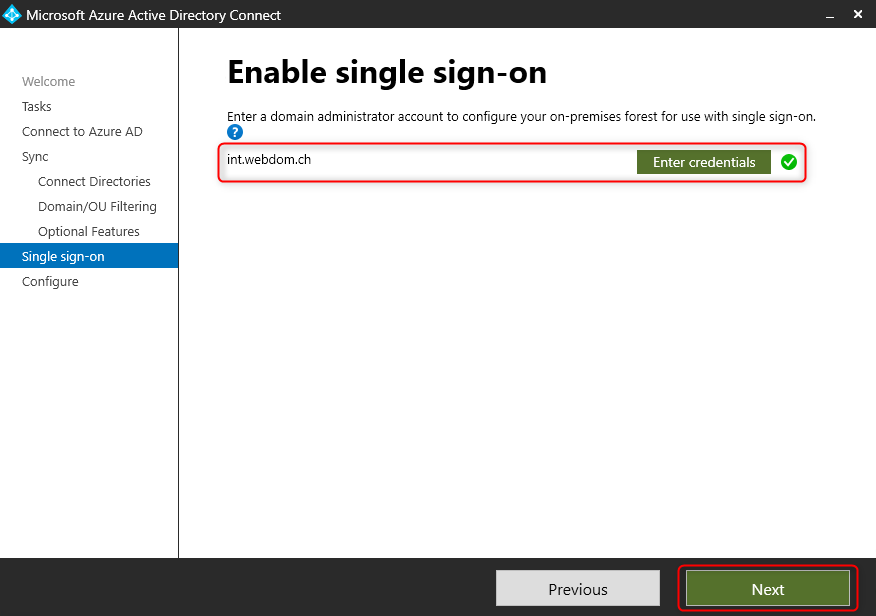
The settings are now checked, if everything is correct, the configuration can be activated by clicking “Configure”.
After the configuration is complete, close “Azure AD Connect” so that synchronization can begin.
The password hashes are now synchronized in the background. Before changing the sign in method, the completion of the password hash synchronization must be waited for.
Check Password Hash Synchronization Status
PowerShell can be used to verify that all password hashes have been synchronized. Successful completion of the synchronization is a prerequisite before the sign in method should be changed.
Open the PowerShell session “as administrator” on the server with Azure AD Connect installed and execute the following commands:
|
1 2 3 |
Set-ExecutionPolicy RemoteSigned Import-Module ADSyncDiagnostics Invoke-ADSyncDiagnostics -PasswordSync |
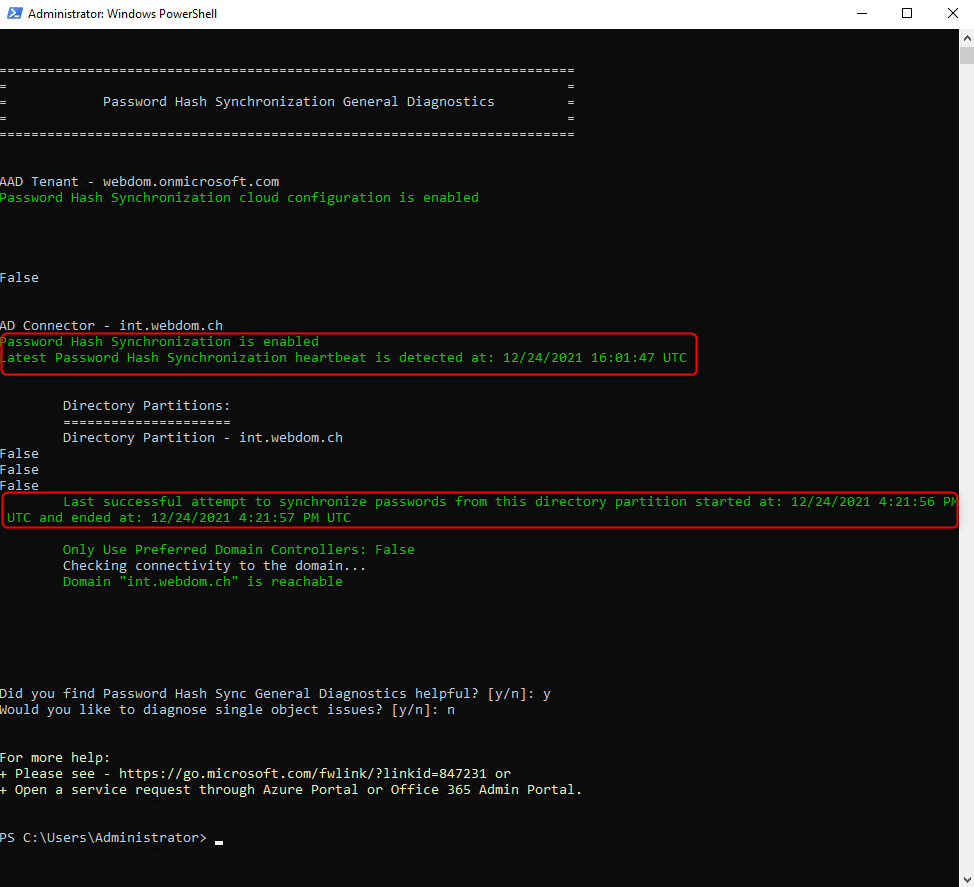
The following output shows that the last password hash synchronization was successful.
Make sure that the last heartbeat is not older than 120 minutes.
All times in the script are in UTC.
Switch sign in method
After successful Password Hash Sync the sign in can be switched from PTA (Passthrough Authentication) to PHS (Password Hash Sync).
Since all hashes have already been synchronized in the preparations, no impact is noticeable for the user.
Open “Azure AD Connect” and click on “Configure”

Select “Change user sign-in”
Sign in in to Azure AD requires an account with global administrator privileges.
Select “Password Hash Synchronization” and “Enable single sign-on”
Single Sign On (SSO) increases user convenience and should be enabled.
The settings are now checked, if everything is correct, the configuration can be activated by clicking “Configure”.
After the configuration is complete, close “Azure AD Connect” so that synchronization can begin.
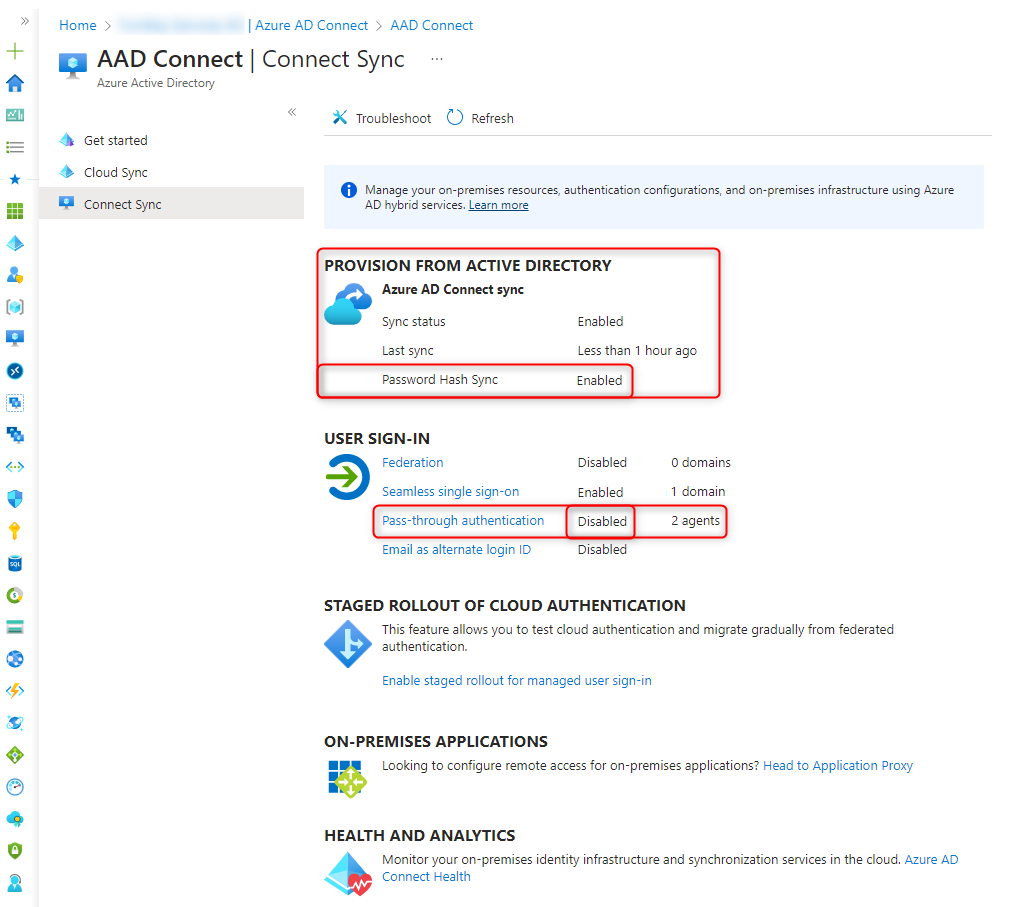
Check which sign in method is enabled
Im Azure Portal (https://portal.azure.com), you can check which sign in method is enabled.
After changing the sign in method, it takes about 15 minutes for the information to be displayed correctly.
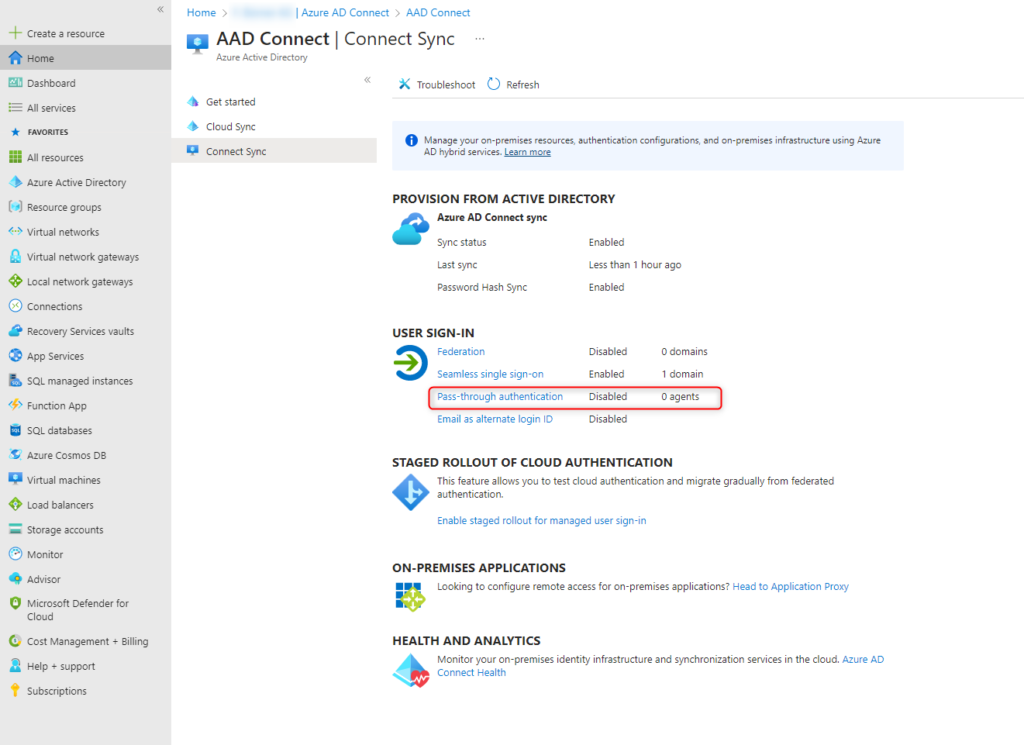
Azure Active Directory > Azure AD Connect > Connect Sync
Password Hash Sync is enabled
Passthrough authentication is disabled
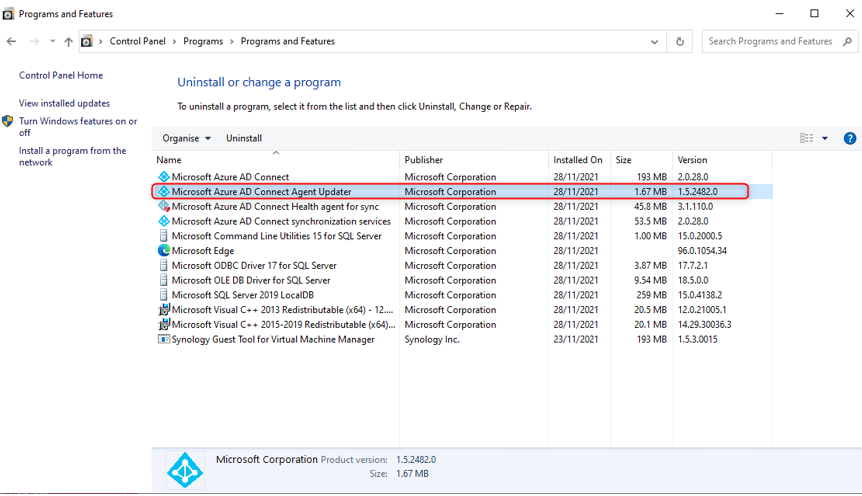
Uninstall PTA Agent
After successful sign in test and 1 week waiting period the Passthrough Authentication Agent (PTA) can be uninstalled from all servers.
Open “Control Panel” to uninstall “Microsoft Azure AD Connect Agent Updater”
After successful uninstallation of the Passthrough Authentication Agent (PTA), the following Azure AD Connect components remain, which are still required.
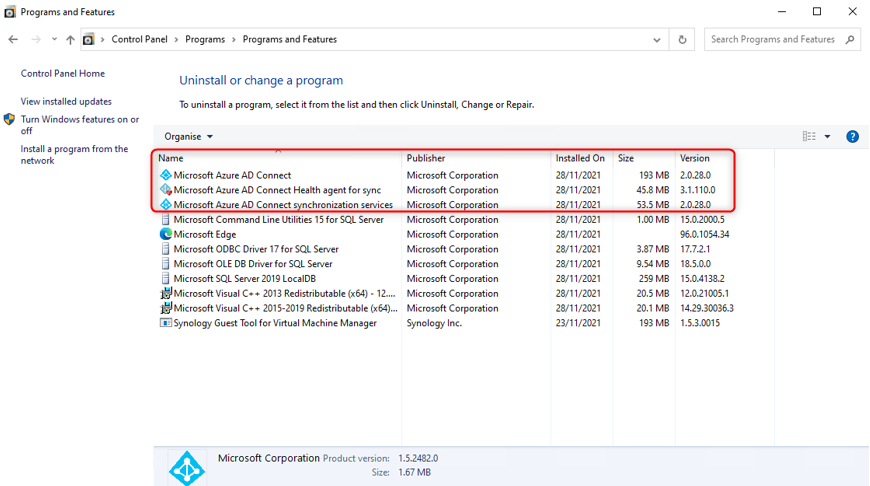
After 10 days, the Passthrough Authentication Agent is also no longer displayed in Azure AD Connect.
Troubleshooting
Password sync: no recent synchronization
A few days after switching the sign in method from Passthrough Authentication to Password Hash Sync, the following error message appeared in the Microsoft 365 Admin Center.
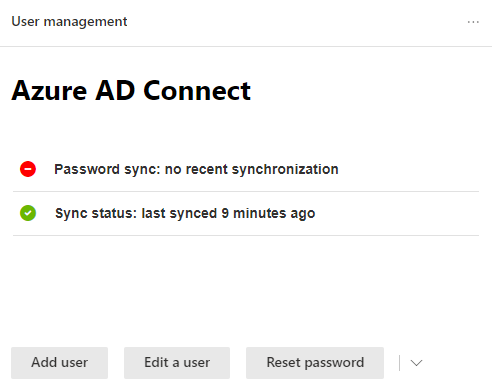
Password sync: no recent synchronization
The following error is regularly displayed in the event log.
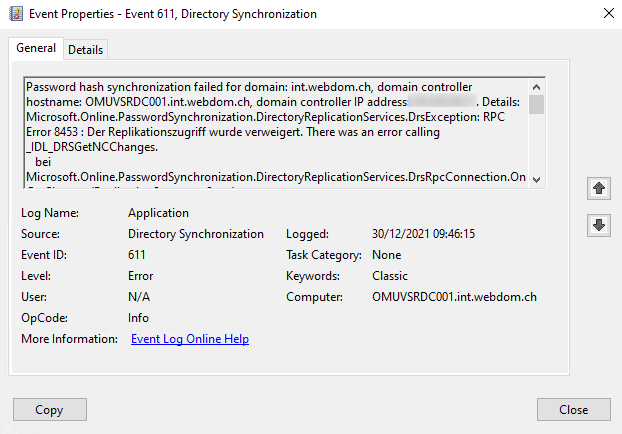
Event ID 611
Source Directory Synchronisation
Password hash synchronization failed for domain: int.webdom.ch
RPC Error 8453: Replication access was denied
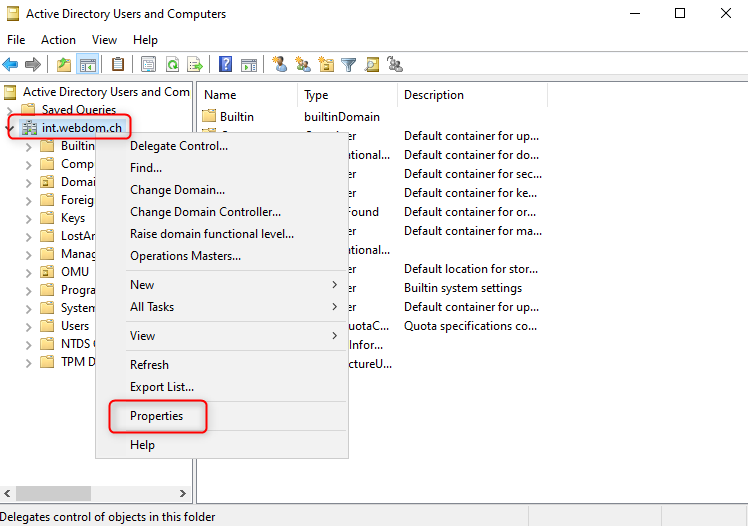
The cause of the error is the permissions assigned to the user performing the AD synchronization.
The user account requires the following permissions:
- Replicating Directory Changes Allow
- Replicating Directory Changes All Allow
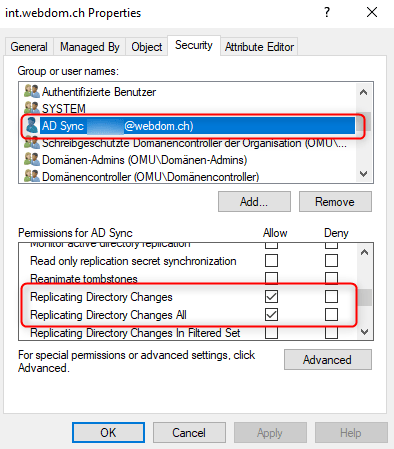
During the following synchronization, the password sync is performed successfully again.
Follow me on LinkedIn and get informed about my latest posts.
Was this post helpful to you? Show your enthusiasm with the delightful aroma of a freshly brewed coffee for me!

