Microsoft Entra Internet Access is a cloud-delivered solution that secures access to web content. It protects users, devices, and data from internet threats. This solution is part of Microsoft’s Security Service Edge (SSE), which also includes Microsoft Entra Private Access. This solution is based on the core principles of Zero Trust Network Access (ZTNA), which aims to apply the principle of minimal rights, explicit verification and assumption of an attack. Microsoft Entra Internet Access implements adaptive access controls, simplifies network security, and enables a consistent user experience, regardless of location. Microsoft delivers the solution over the Microsoft Wide Area Network, which covers more than 140 countries and 190 network edge locations.
This blog article shows the configuration steps for Microsoft Entra Internet Access to filter web content by category.
Prerequisites and Licensing
Licences
For Microsoft Entra Internet Access, each user requires one of the following licenses:
- Microsoft Entra Suite
- Microsoft Entra Internet Access
Detailed information and pricing for the various plans are clearly presented on the Microsoft product webpage: Microsoft Entra Plans and Pricing | Microsoft Security
Roles
Setting up and managing Microsoft Entra Internet Access requires the Global Secure Access Administrator role.
Setting up and managing conditional Microsoft Entra access requires either the Conditional Access Administrator or Security Administrator role.
Devices
The following requirements apply to the devices:
- Operating system Windows 10, Windows 11 or Android
- iOS and MacOS available as preview
- Windows Devices must be either Microsoft Entra joined or Microsoft Entra hybrid joined, Microsoft Entra registered devices aren’t supported
Onboard Microsoft Entra Internet Access
Microsoft Entra Internet Access is enabled in the Microsoft Entra admin center (https://entra.microsoft.com).
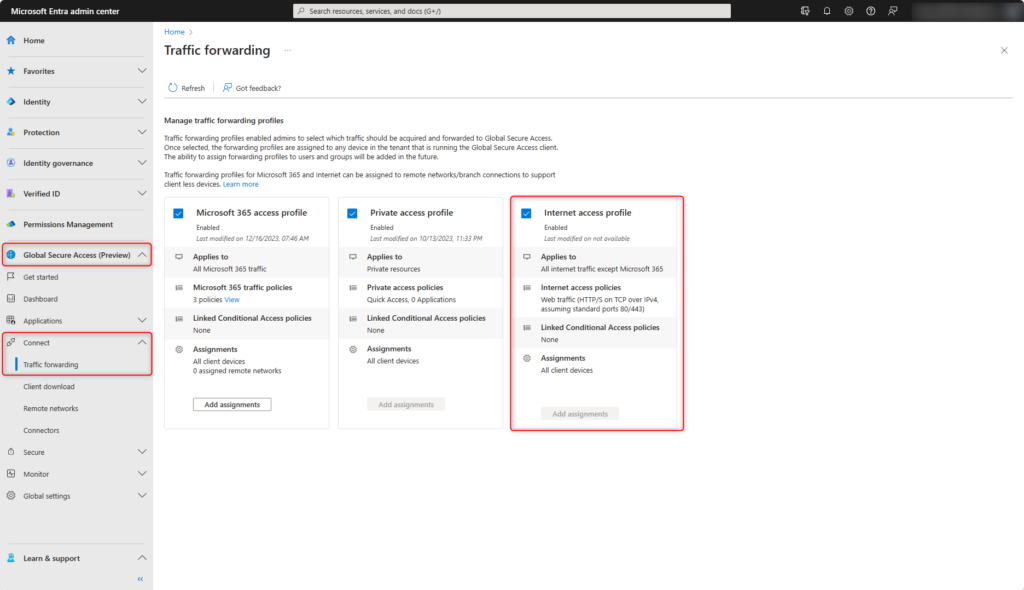
Traffic forwarding
Enable Internet access profile in Global Secure Access > Connect > Traffic forwarding.
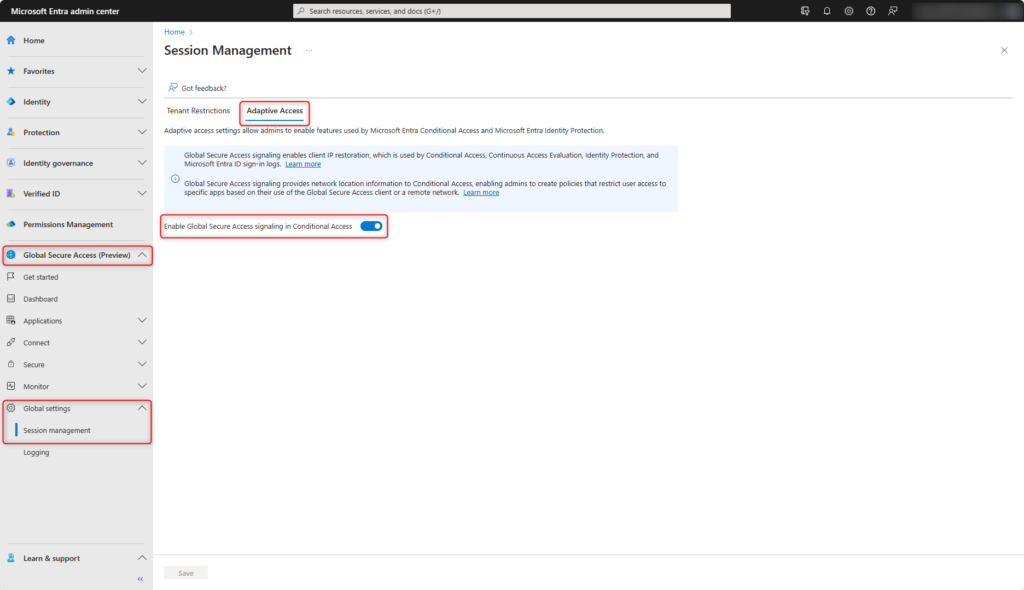
Adaptive Access
Enable Global Secure Access signaling in Microsoft Entra Conditional Access.
Enable Adaptive Access in Global Secure Access > Global Settings > Session management > Adaptive Access.
Microsoft Entra Internet Access configuration
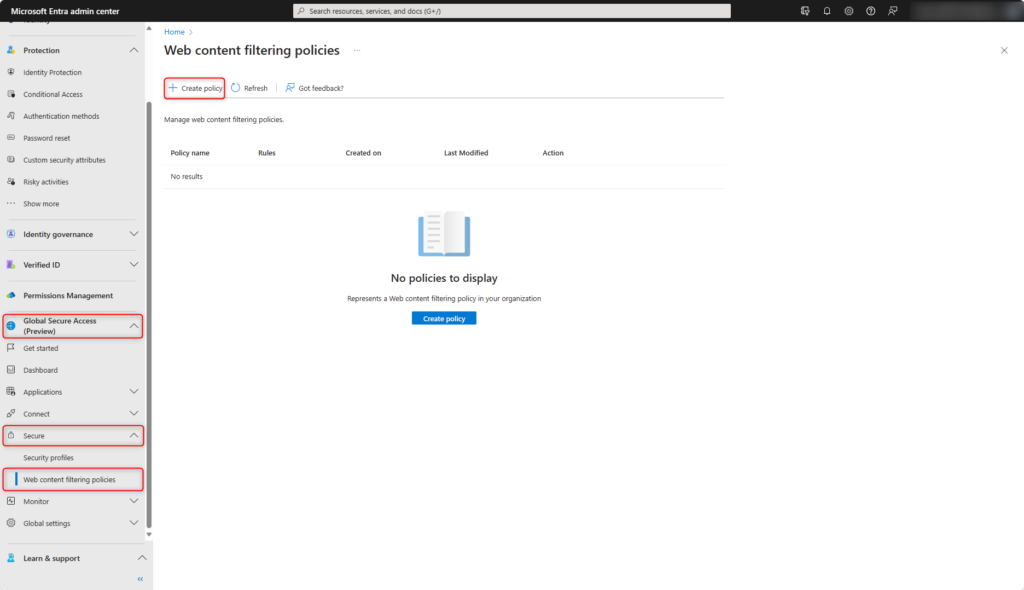
Web content filtering policies
Access to web content is blocked or permitted by category. It is also possible to block specific domains. In this example, access to websites in the category Gambling is blocked.
Create new web filter policy in Global Secure Access > Secure > Web content filtering policies > Create policy.
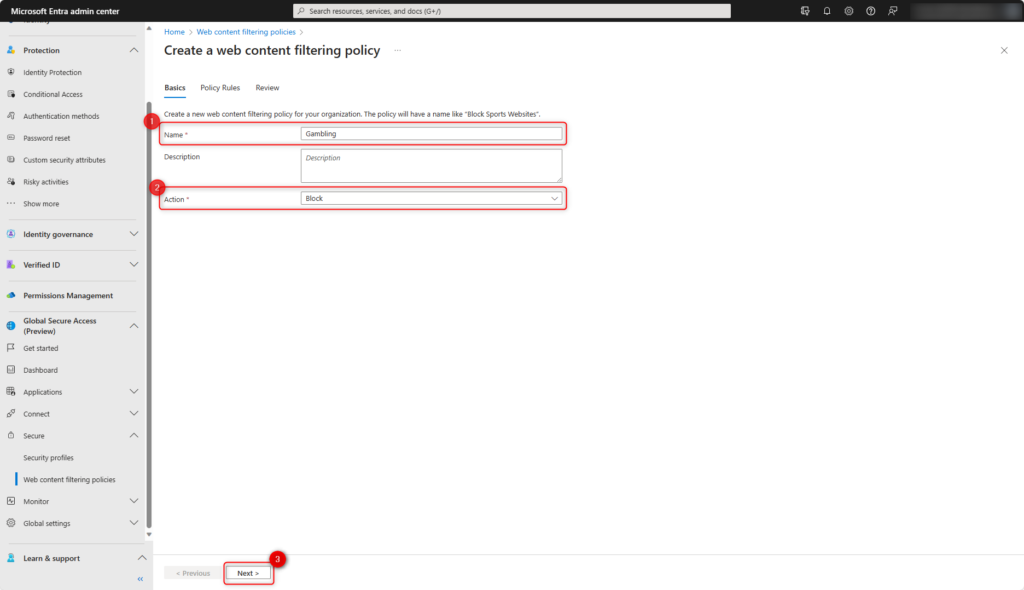
- Enter the Name of the web filter policy, e.g. Gambling
- Select the Action of the web filter policy (block or allow)
- Click on Next
- Select Add Rule
- Enter Name of the policy
- Set Destination type to webCategory
- Select web content filter category Gambling
- Create policy with Add
- Confirm policy with Next
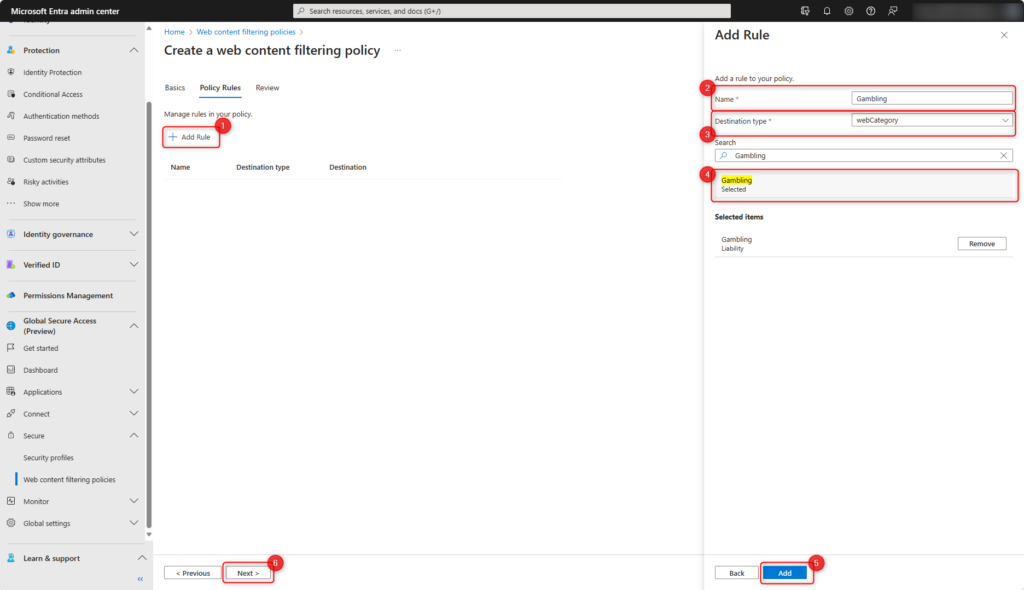
Check settings and click on Create Policy.
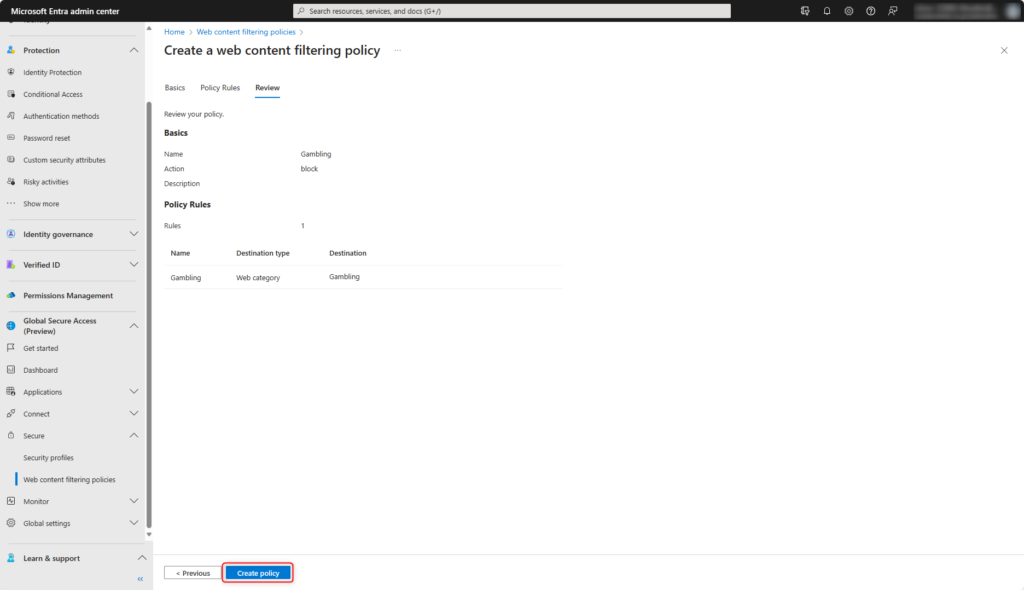
The new web content filtering policy has been created.
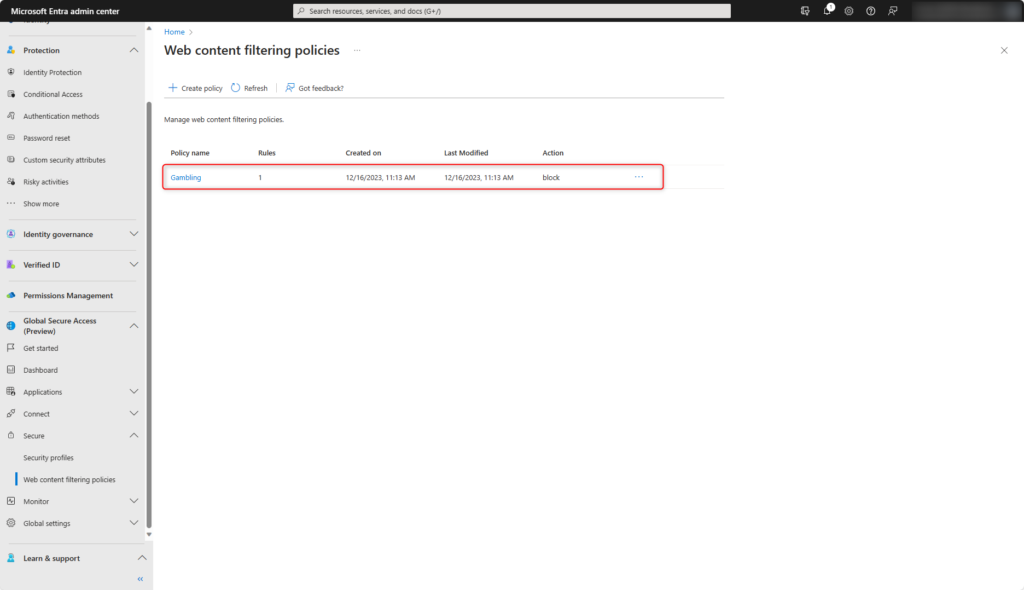
Security profiles
The web content filtering policies are organized in the security profiles. Security profiles are enabled user- and context-dependent with Microsoft Entra Conditional Access.
Create new security profile in Global Secure Access > Secure > Security profiles > Create profil.
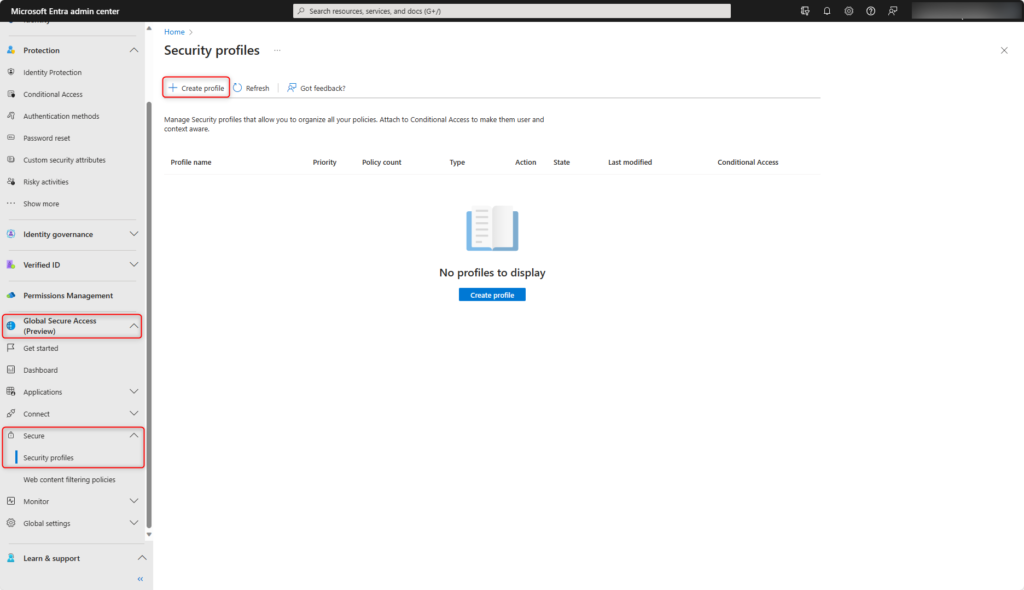
- Enter Name for the security profile, e.g. Illegal Activities
- Set State to enabled
- Set the Priority within all security profiles, the lower the value, the higher the priority of the security profile
- Click on Next
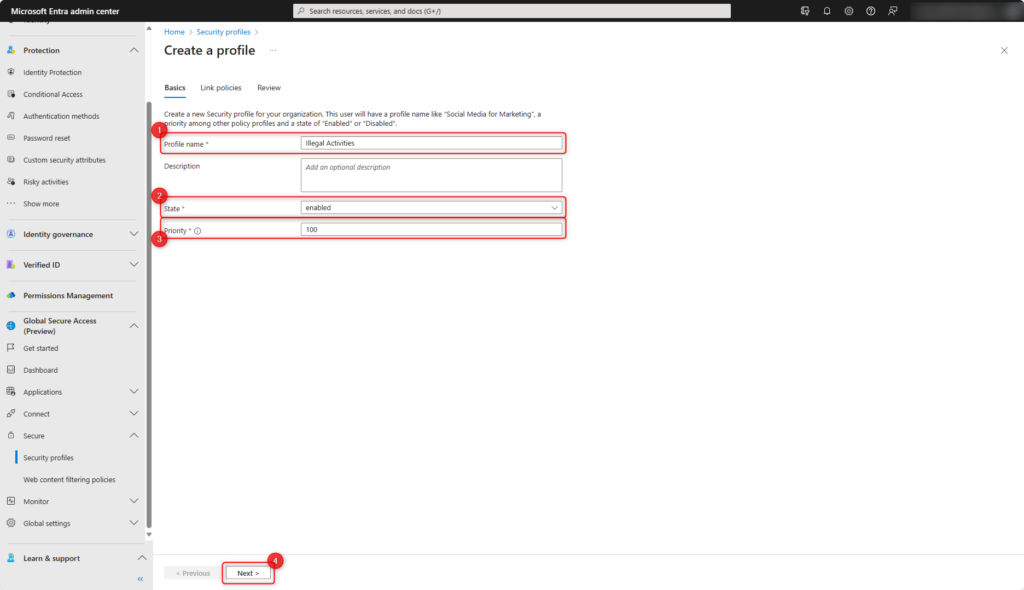
- Select Add Rule
- Enter Name of the policy
- Set the Priority within this security profile, the lower the value, the higher the priority of the policy
- Set the State of the policy (enabled or disabled).
- Add policy with Add
- Confirm policy with Next
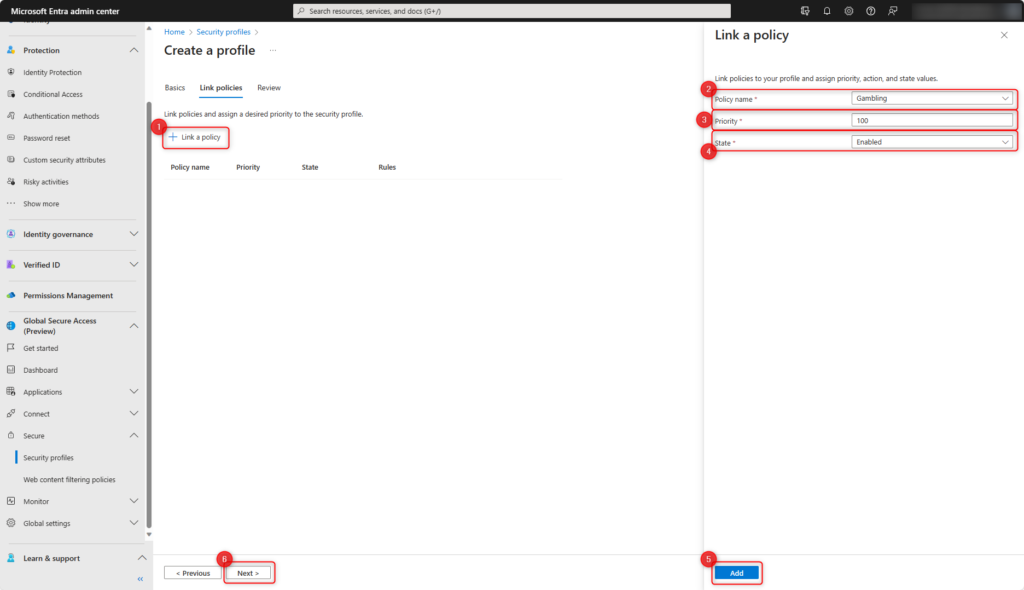
Check settings and click on Create profile.
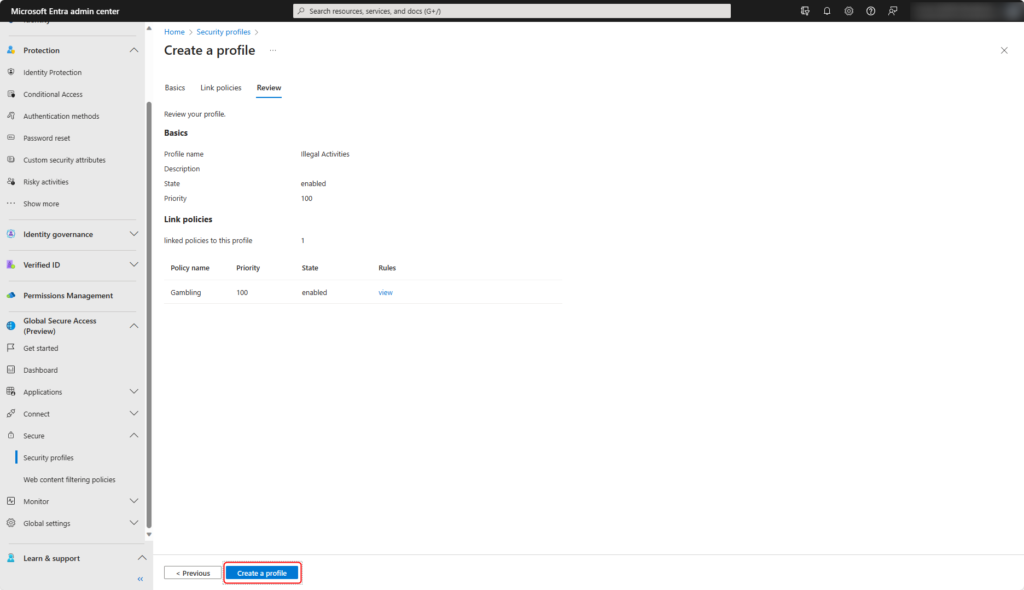
The new security profile has been created.
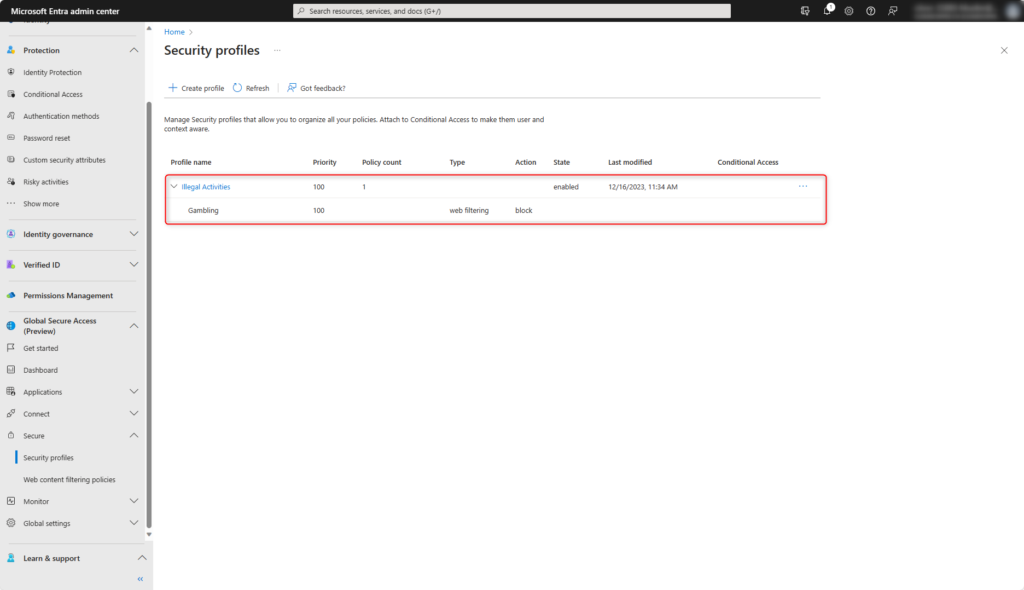
Enable security profiles with Microsoft Entra Conditional Access
The security profile are enabled according to your own requirements with Microsoft Entra Conditional Access.
Protection > Conditional Access > Create new policy
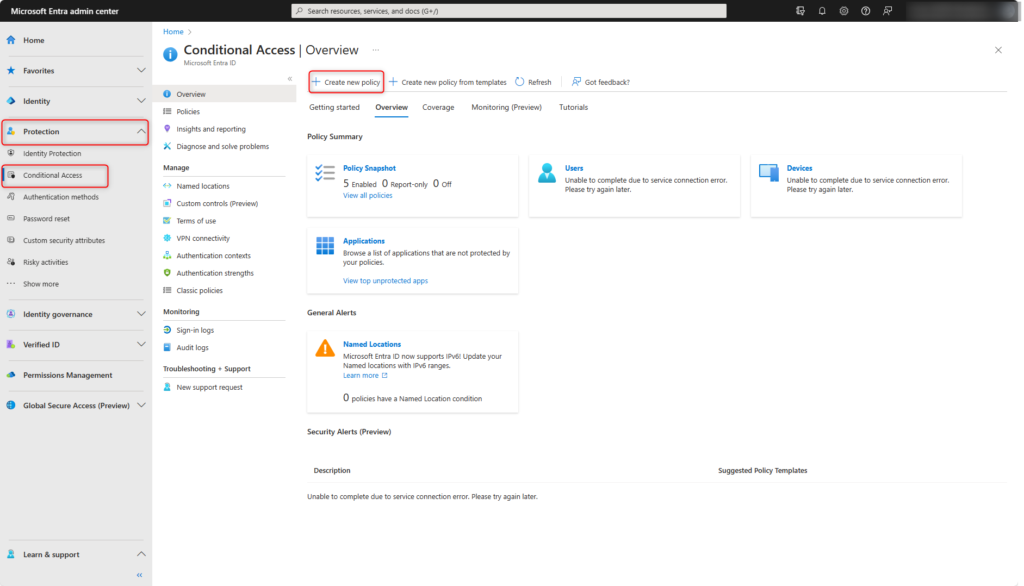
Specify users or user groups for Microsoft Entra Conditional Access under Users. If Azure emergency access accounts are used, exclude them from the policy.
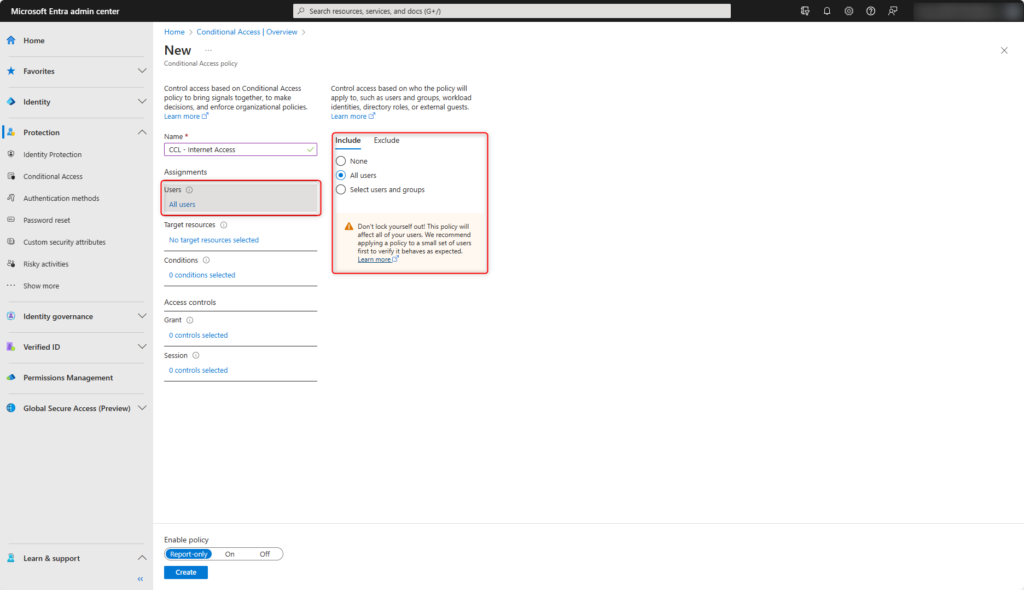
Microsoft Entra Conditional Access is done under Target resources on Global Secure Access (1) and the traffic profile Internet Traffic (2).
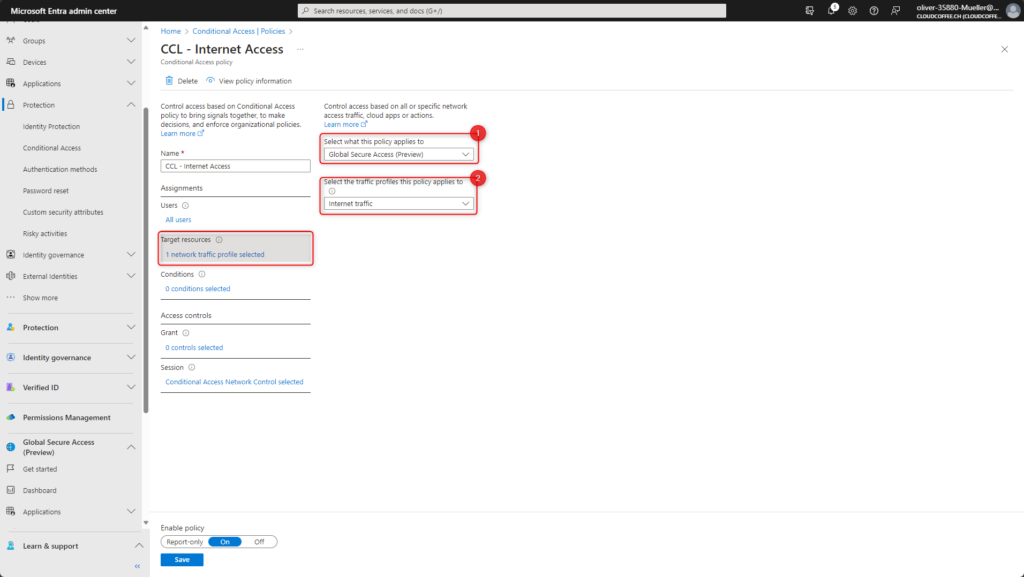
The previously created security profile is specified in the Session category under Use Global Secure Access security profile.
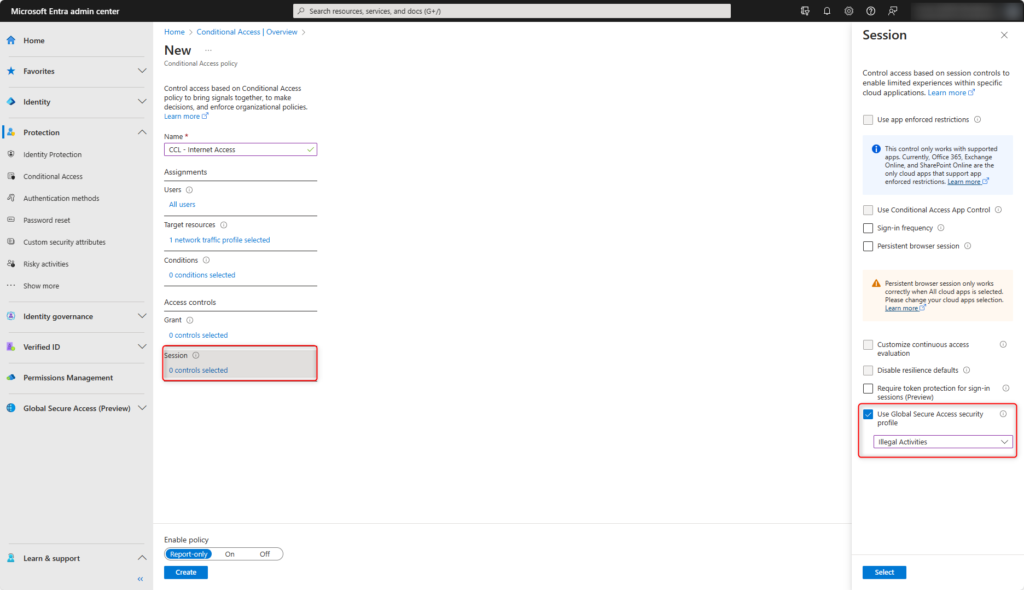
Enable policy and create it with Create.
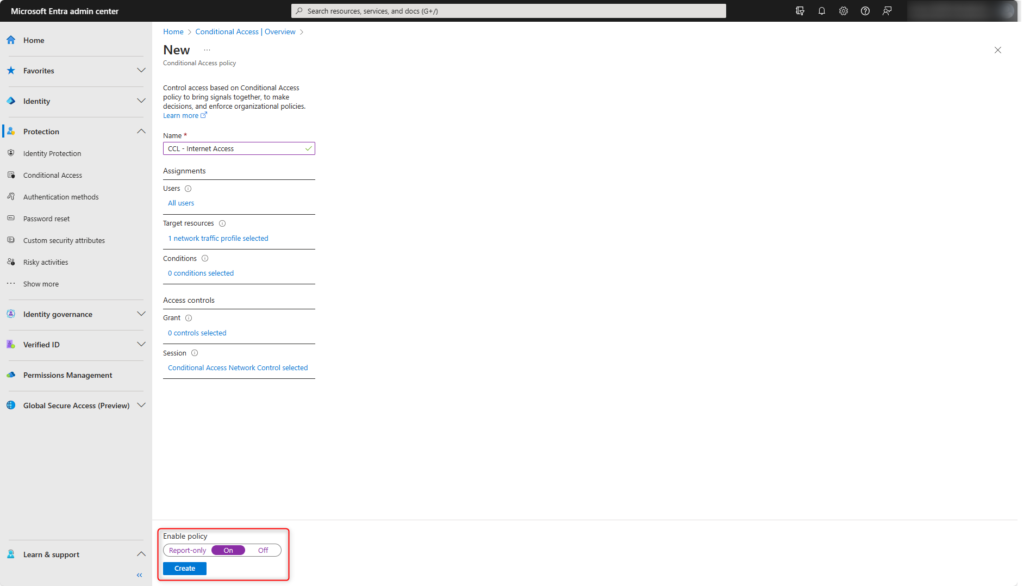
The policy has been created and enabled.
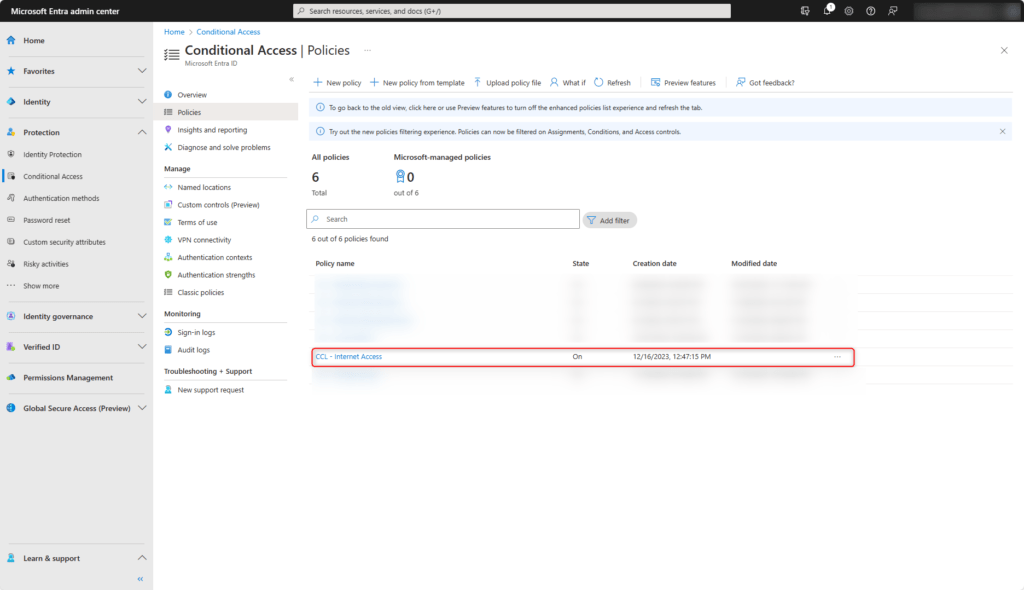
Onboard Clientsoftware
The Global Secure Access Client for using Microsoft Entra Internet Access is released for various operating systems. The deployment of the clientsoftware on Windows is described in the article Microsoft Entra Private Access: Onboard Clientsoftware.
Functional check
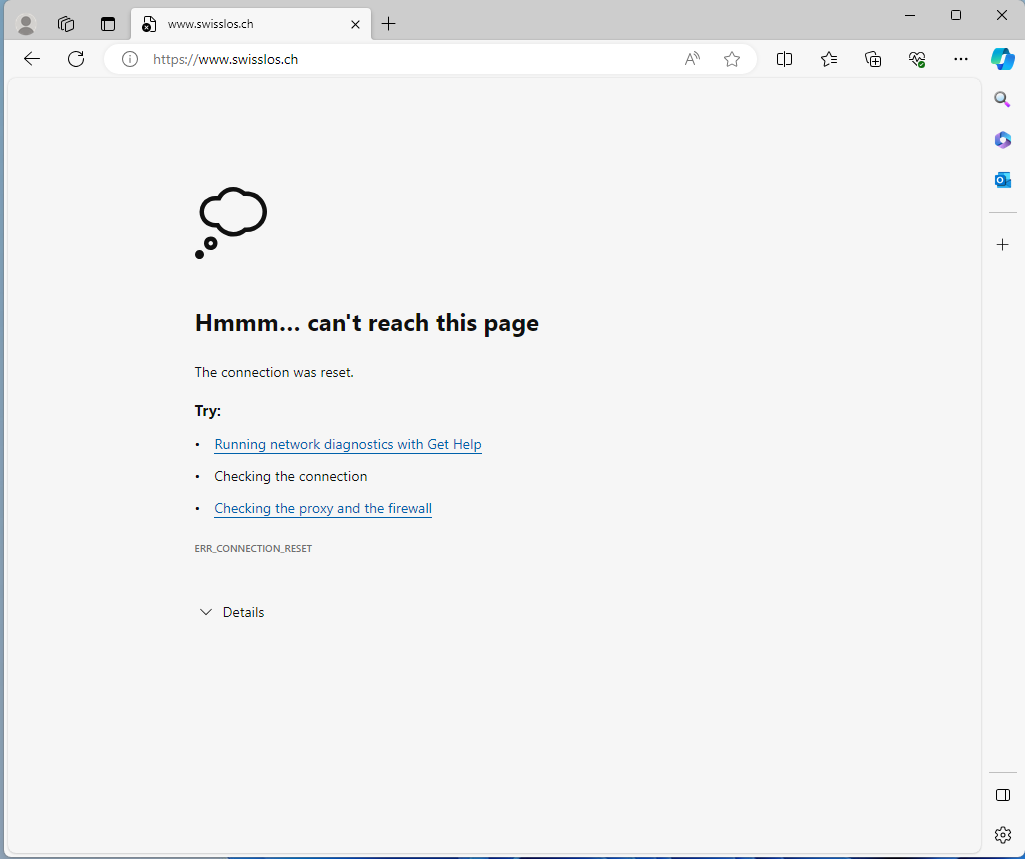
In this example, a device with Global Secure Access Client accesses the website https://www.swisslos.ch. The website is assigned to the web filter category Gambling and is blocked by the created security profile and Microsoft Entra Conditional Access.
At the time of writing this blog post, it is not yet possible to customize the notification about blockages.
Troubleshooting
Microsoft Entra admin center
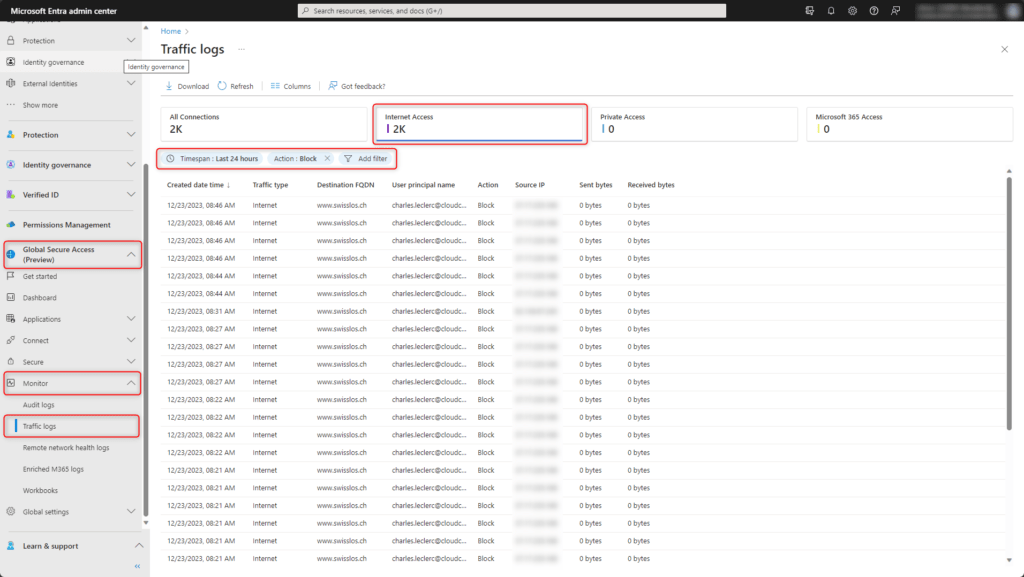
Traffic logs
The Traffic logs for the various services of Global Secure Access are found in Global Secure Access > Monitor > Traffic logs. The traffic logs offers many filtering options.
Device
The Global Secure Access Client offers various options in Advanced diagnostic to check the current status, collect and analyze traffic in real time.
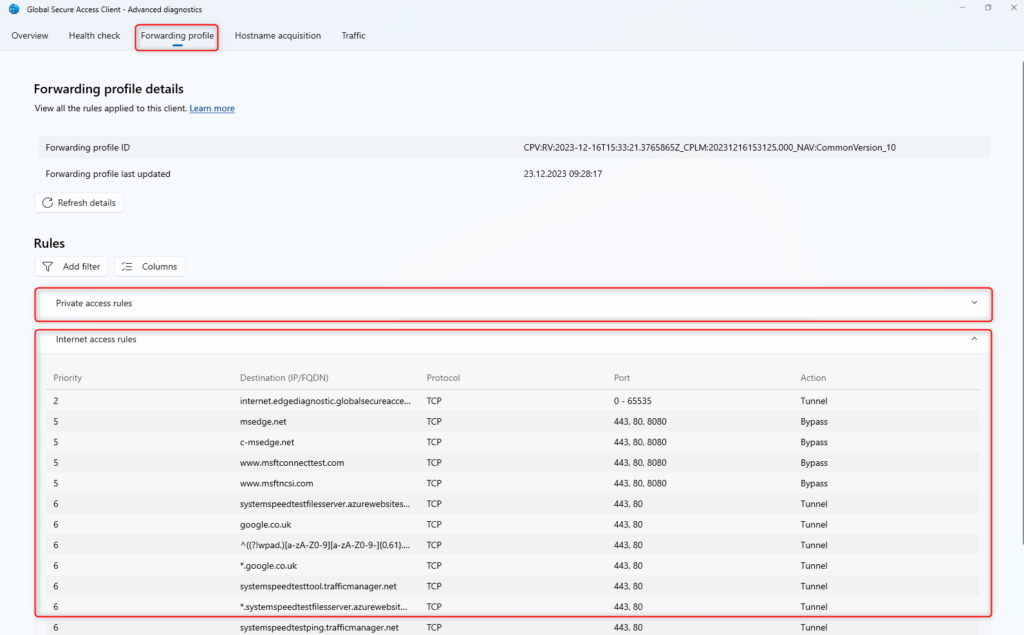
Forwarding profile
Enabled traffic forwarding profiles for this device are visible under Forwarding profile. When expanding a rule, detailed information about the traffic is displayed.
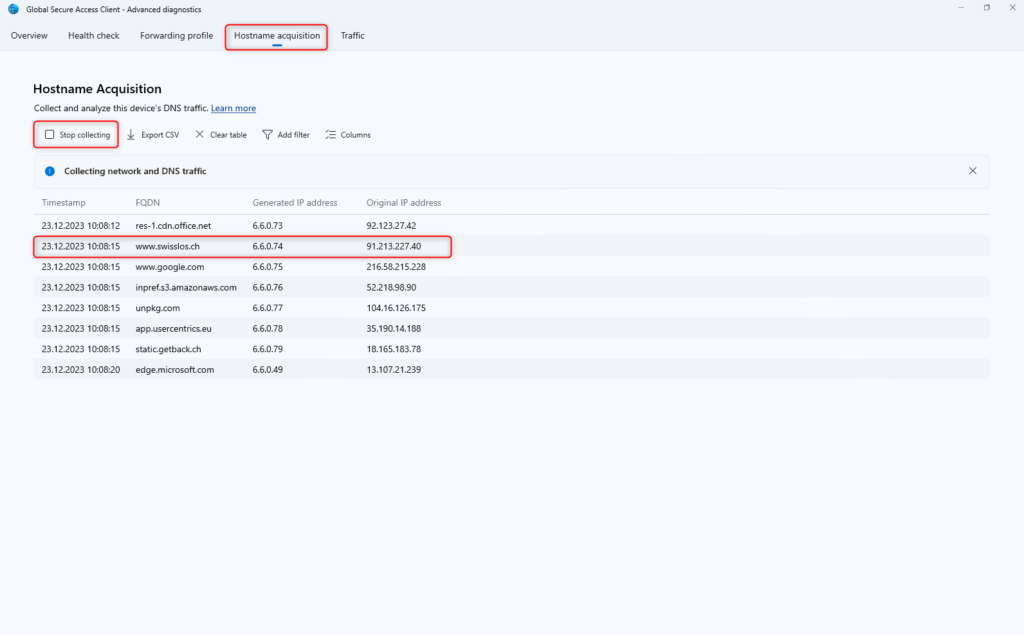
Hostname acquisition
In Hostname acquisition, the traffic can be collected and checked that the traffic is actually routed through Global Secure Access.
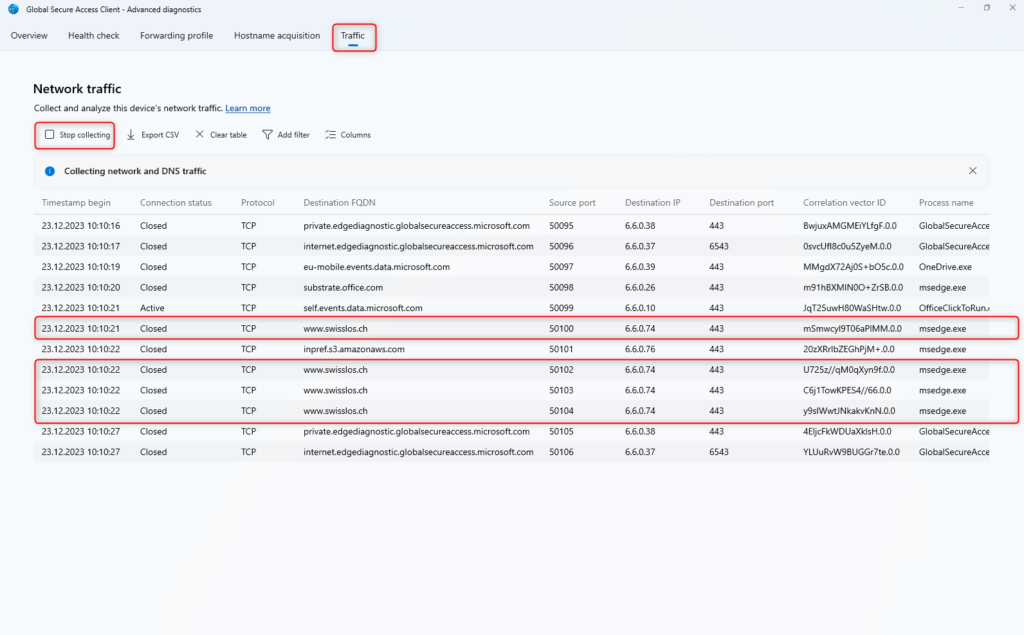
Traffic
Traffic shows the traffic of the device in real time.
Follow me on LinkedIn to always stay updated on my recent posts.
Was this post helpful to you? Show your enthusiasm with the delightful aroma of a freshly brewed coffee for me!

