WatchTra: Automated Attribute Compliance for Microsoft Entra ID
In many Microsoft Entra ID environments, the quality of user attributes remains an often underestimated factor in security and governance. WatchTra enhances attribute compliance in Microsoft Entra ID and ensures consistent identity data across the organization. In practice, attributes frequently contain inconsistent spellings or values, for example, “Switzerland” instead of “Swiss” or “IT” instead of “Information Technology”, as well as missing or outdated entries. Such discrepancies can result in incorrect dynamic group memberships, inaccurate reporting or incomplete policy enforcement.
However, a consistent validation of these attributes against organization-wide standards is rarely implemented in real-world environments.
WatchTra is an open-source tool that automates attribute compliance in Microsoft Entra ID and reliably detects deviations. It compares the actual attribute values with predefined standards and identifies inconsistencies with accuracy. Through the WatchTra Dashboard, administrators can centrally analyze incorrect or missing attributes, identify affected users, and clearly visualize all detected deviations.
This article provides a step-by-step guide to deploying and configuring WatchTra in an existing Microsoft Azure environment, from the initial prerequisites and definition of user attributes to leveraging the WatchTra Dashboard for continuous compliance monitoring in Microsoft Entra ID.
Prerequisites and Licensing
Azure Subscription
An active Microsoft Azure subscription is linked to the Microsoft Entra tenant and provides the necessary resources.
Microsoft Azure Portal (https://portal.azure.com) > Subscriptions
Roles
Following the principle of least privilege, deploying WatchTra requires the following roles.
| Role | Permission |
| Application Administrator | Create and configure the app registration |
| Privileged Role Administrator | Grant admin consent (Microsoft Graph app roles) |
| Contributor | Provision and manage Azure resources |
Deploy WatchTra for Attribute Compliance in Microsoft Entra ID
Create the App Registration
WatchTra requires an app registration in Microsoft Entra ID to authenticate and access the necessary Microsoft Graph API permissions.
The app registration is created in the Microsoft Azure Portal (https://portal.azure.com) > Microsoft Entra ID > Manage > App registrations > New registration
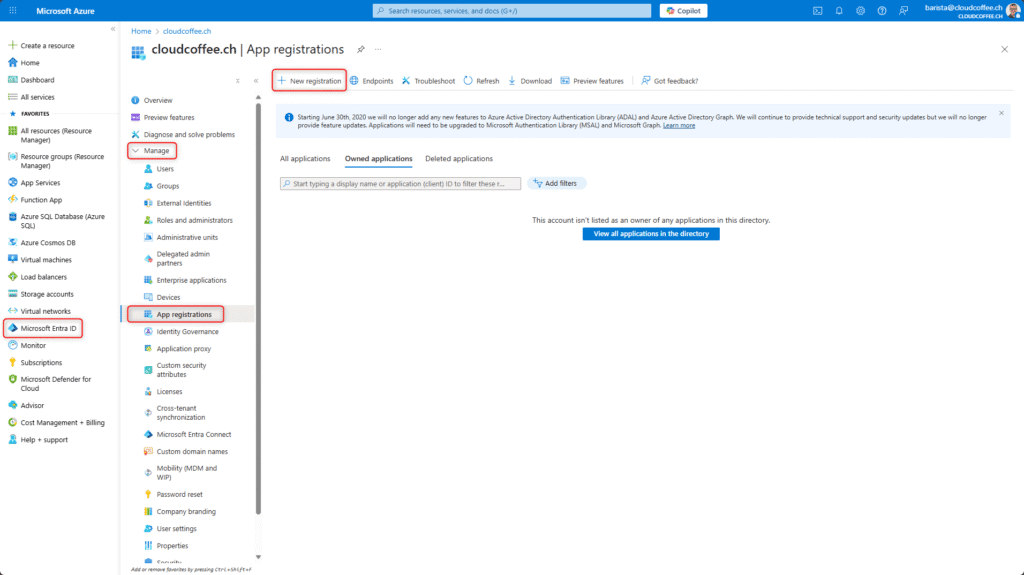
Enter the Name (1) for the application, e.g., WatchTra
Set Supported account types (2) to Accounts in this organizational directory only
The Redirect URI (3) field can be left blank
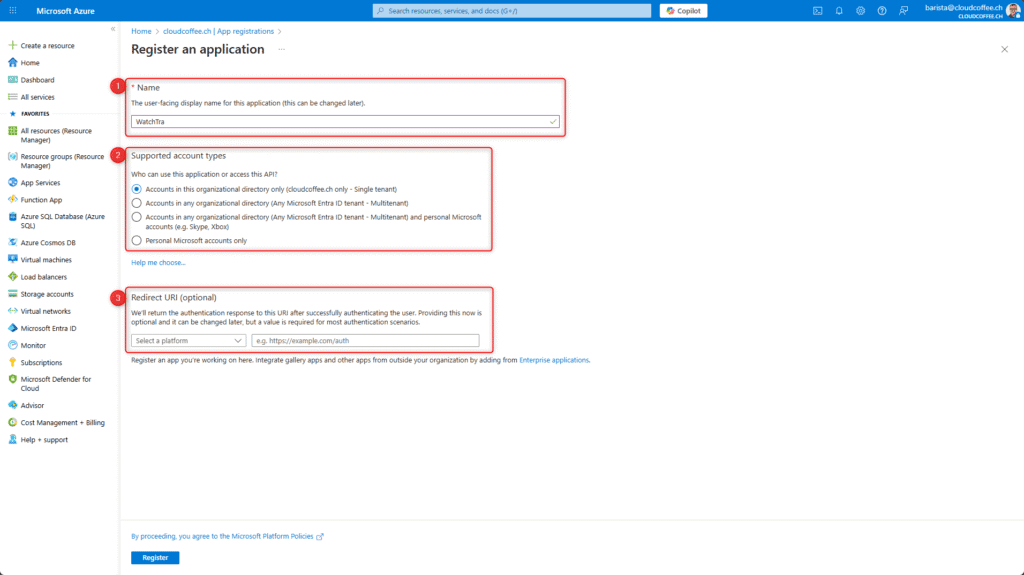
Under Manage > Certificates & secrets > Client secrets select New client secret to create a new key. The description and expiration period can be adjusted according to your organization’s requirements.
Make sure to copy the value of the client secret, as Azure displays it only once.
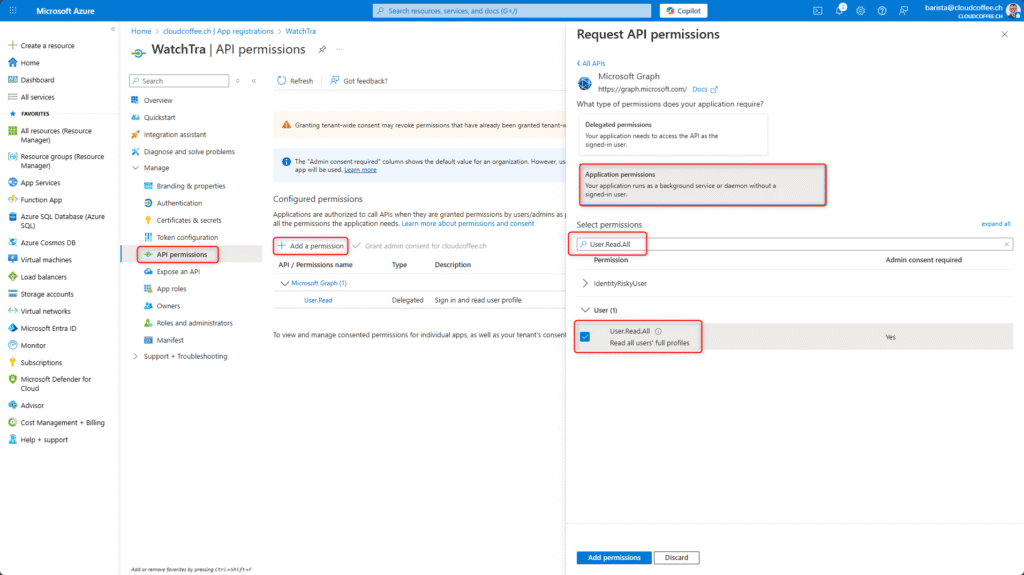
Add the following Microsoft Graph API permissions under Manage > API permissions > Add a permission > Microsoft Graph > Application permissions:
User.Read.All
Group.Read.All
GroupMember.Read.All
AuditLog.Read.All
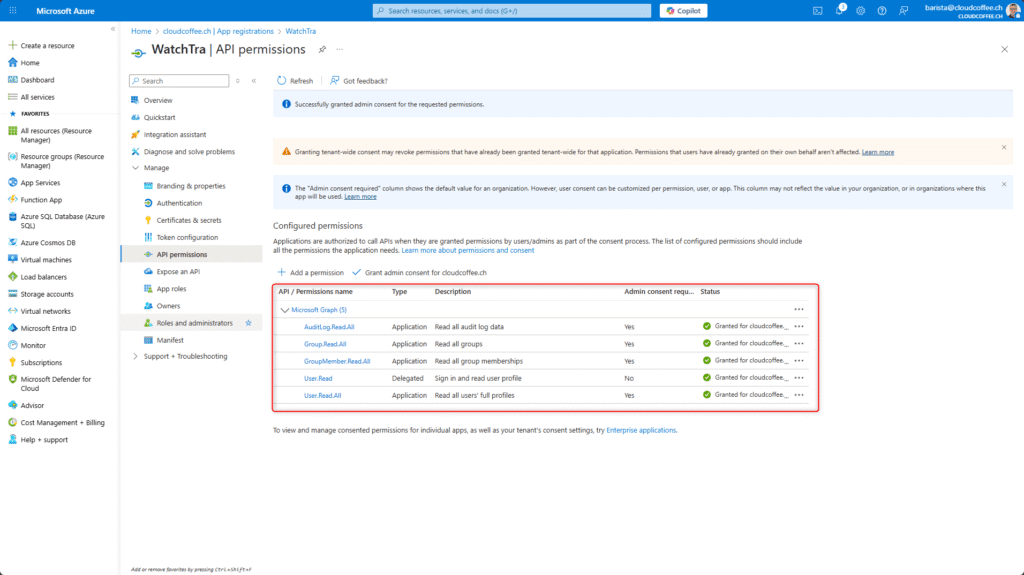
Grant Admin Consent

The app registration is now complete.
Deploy WatchTra to Azure
Once the app registration has been created, WatchTra can be deployed directly to Azure from the GitHub repository. During deployment, the process automatically creates and configures all required Azure components.
Open the WatchTra GitHub repository and select Deploy to Azure
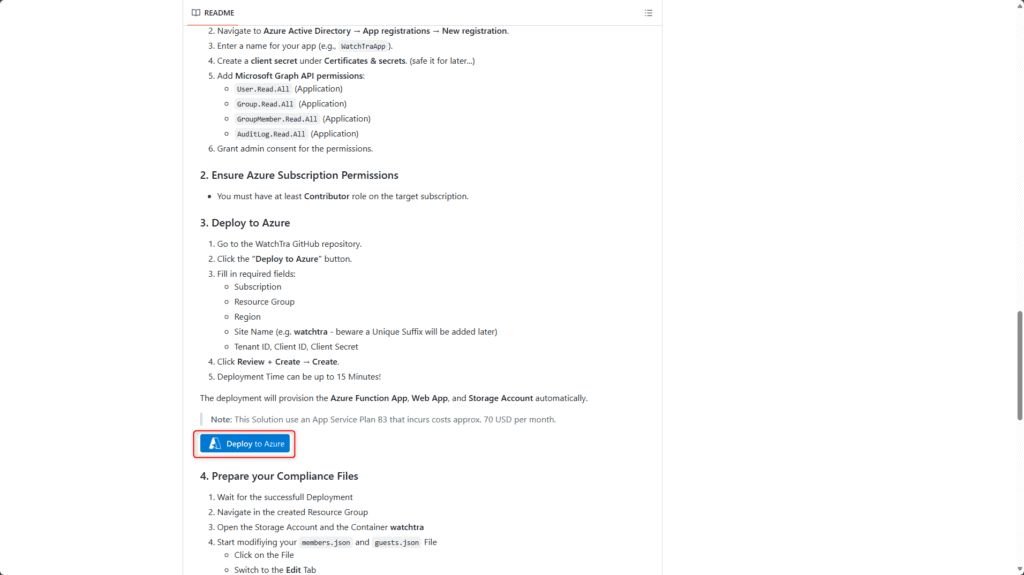
Fill in the following fields:
- Select Subscription
- Select or create a Resource group, e.g., rg-watchtra
- Select Azure region
- Enter Site name, e.g. watchtra, use lowercase letters only (a unique suffix will be added automatically)
- Tenant ID, from the App registration overview
- Client ID, from the App registration overview
- Client Secret, enter the value previously copied when creating the client secret
Select Review + create
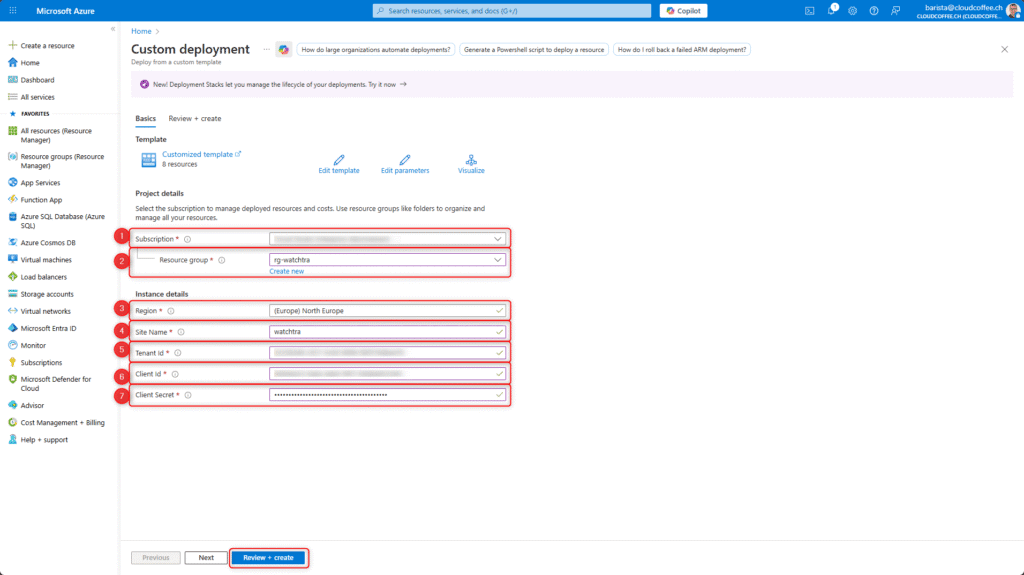
Review the configuration and select Create to start the Azure deployment.
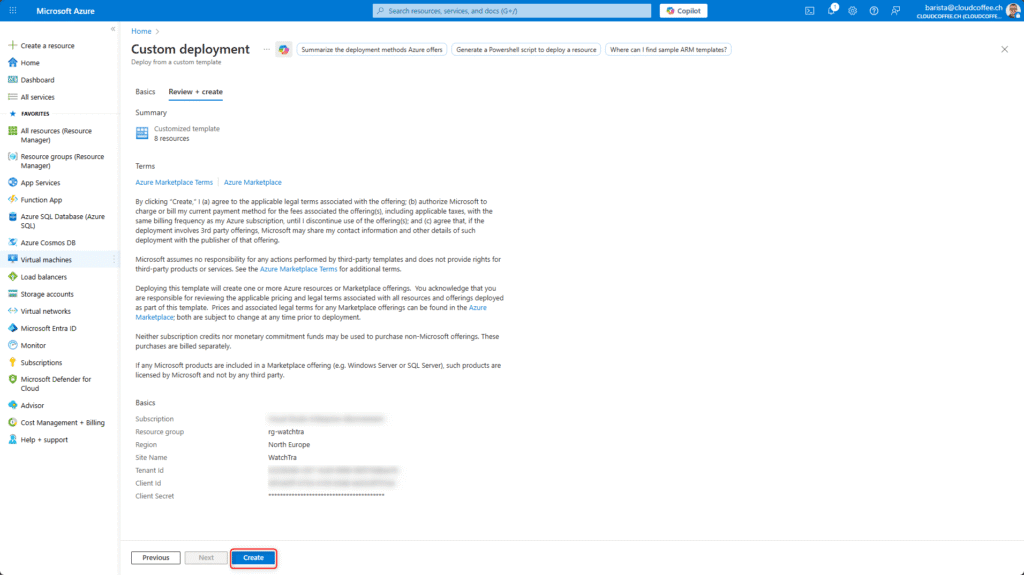
The deployment is typically completed within 15 minutes.
Afterwards, the required Azure resources, such as App Service, Function App and Storage Account, are automatically created.
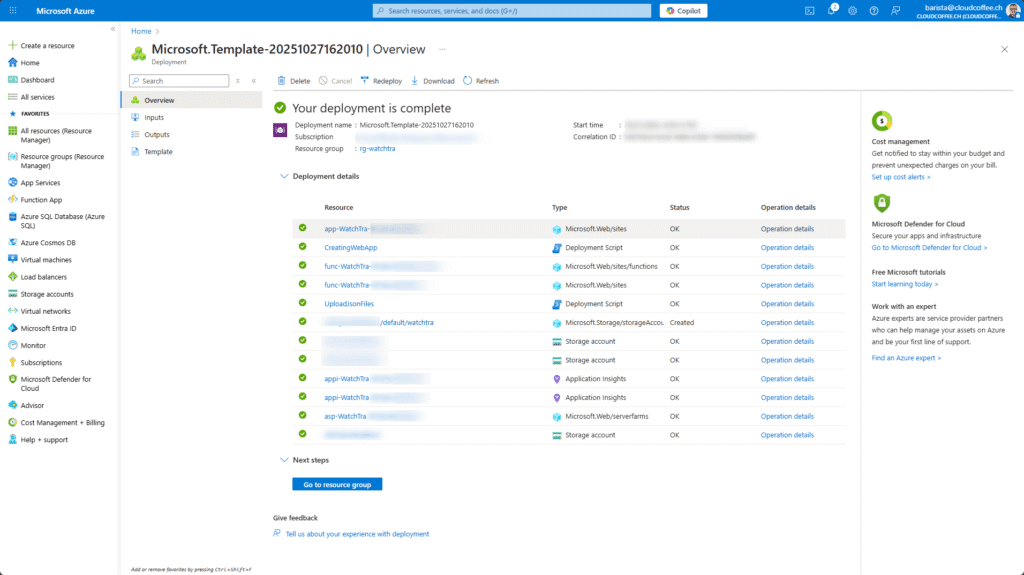
Define Attribute Defaults in JSON
After the deployment has completed, the JSON files must be adjusted to define which user attributes in Microsoft Entra ID are considered compliant. These files form the foundation of the compliance validation in WatchTra.
The JSON files are located in the previously created Storage Account:
Microsoft Azure Portal (https://portal.azure.com) > Resource Groups > previously created resource group > Select Storage Account
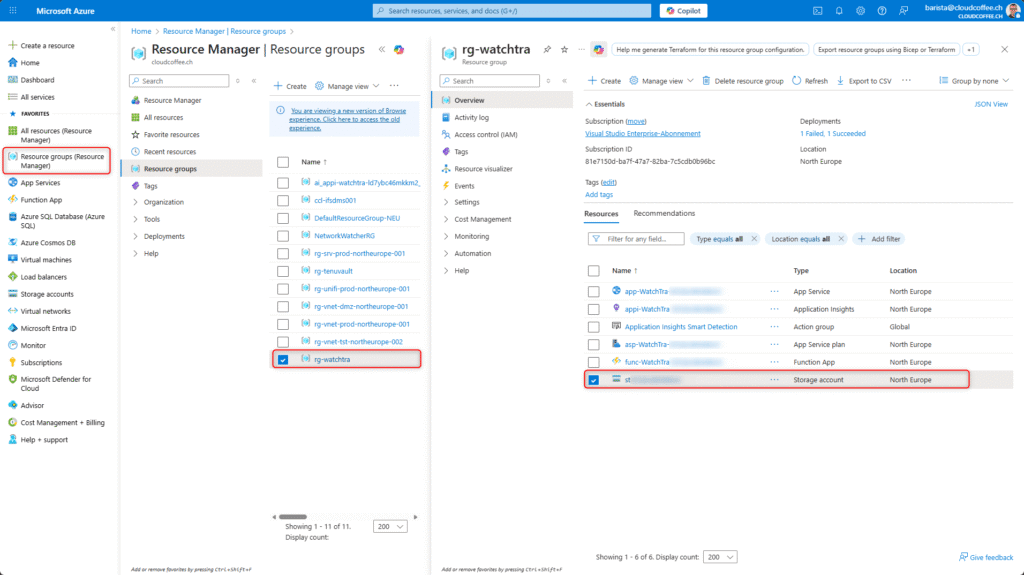
The files appear in the Storage Account under Data storage > Containers > watchtra.
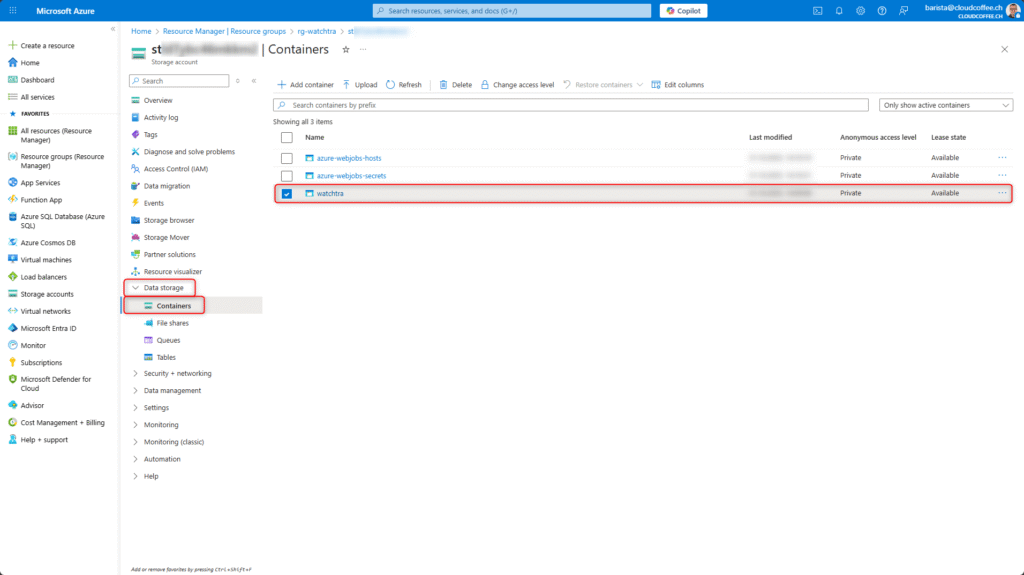
The members.json and guests.json files define the allowed user attributes for member and guest accounts in Microsoft Entra ID.
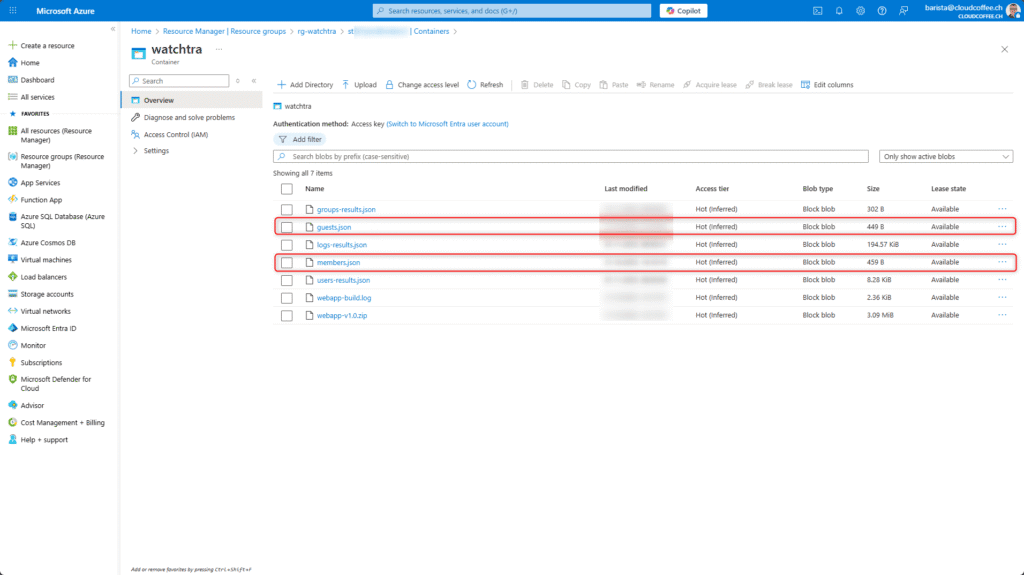
The structure and syntax of the files are self-explanatory. In the following example, the excludeUsers section defines which accounts are excluded from the compliance validation, typically emergency access accounts. This is followed by the attributes to be validated, along with their respective allowed values.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 | { "excludeUsers": { "allowed": [ "BreakGlass1@contoso.com", "BreakGlass2@contoso.com" ] }, "companyName": { "allowed": ["cloudfil.ch", "contoso.com"] }, "department": { "allowed": ["IT", "HR", "Finance", "Marketing"] }, "officeLocation": { "allowed": ["Bern", "Zurich", "Hamburg"]] }, "city": { "allowed": ["Zurich", "Bern", "Zurich", "Hamburg"] }, "country": { "allowed": ["Switzerland", "Germany", "France"] } } } |
Use WatchTra for Attribute Compliance in Microsoft Entra ID
Open the Web Application
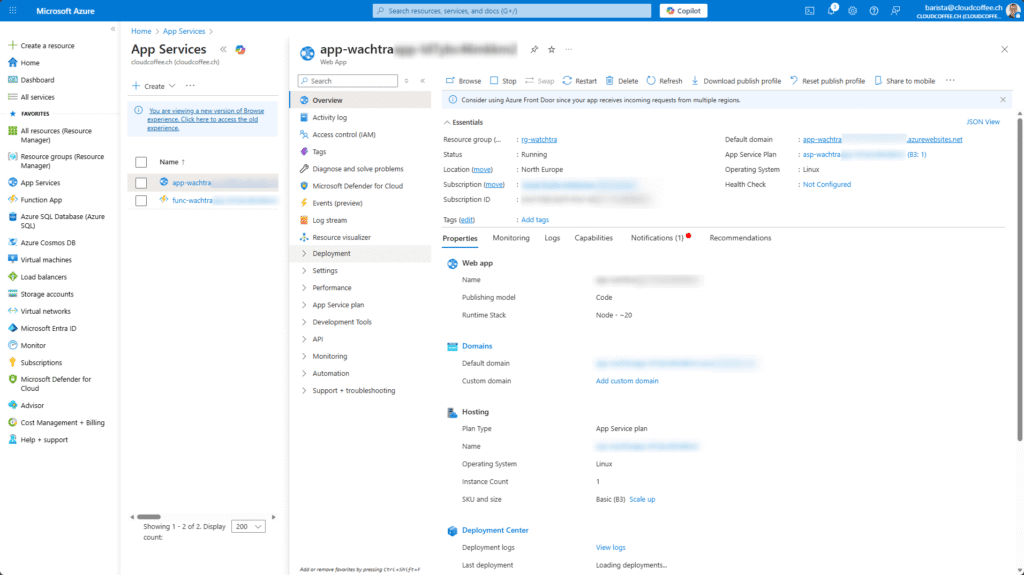
After deployment, WatchTra is available as a web application under App Services.
The URL to access the application is shown in the Overview section under Default domain.
Documentation
WatchTra includes integrated documentation under Docs, which is regularly updated and describes all dashboard features in detail.
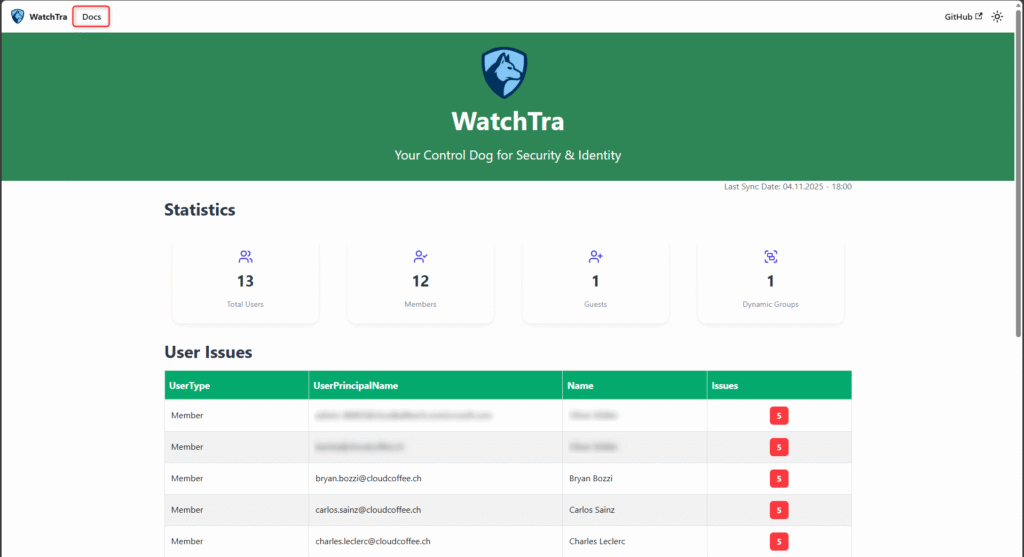
Dashboard
The WatchTra Dashboard provides a centralized overview of the compliance status of all user attributes in Microsoft Entra ID. It summarizes the data retrieved during the most recent synchronization and visualizes the results across clearly structured sections. Through the dashboard, deviations and non-compliant attributes can be quickly identified.
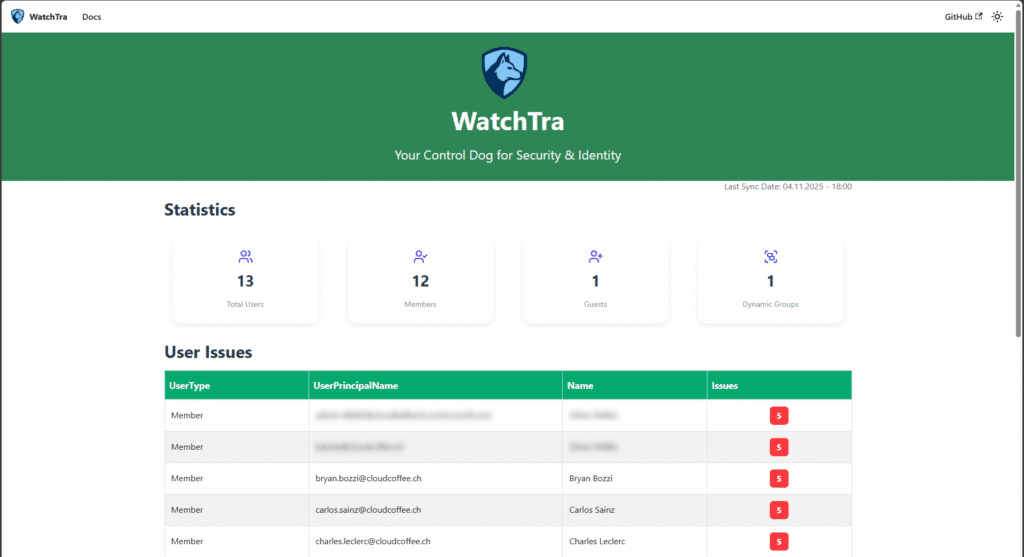
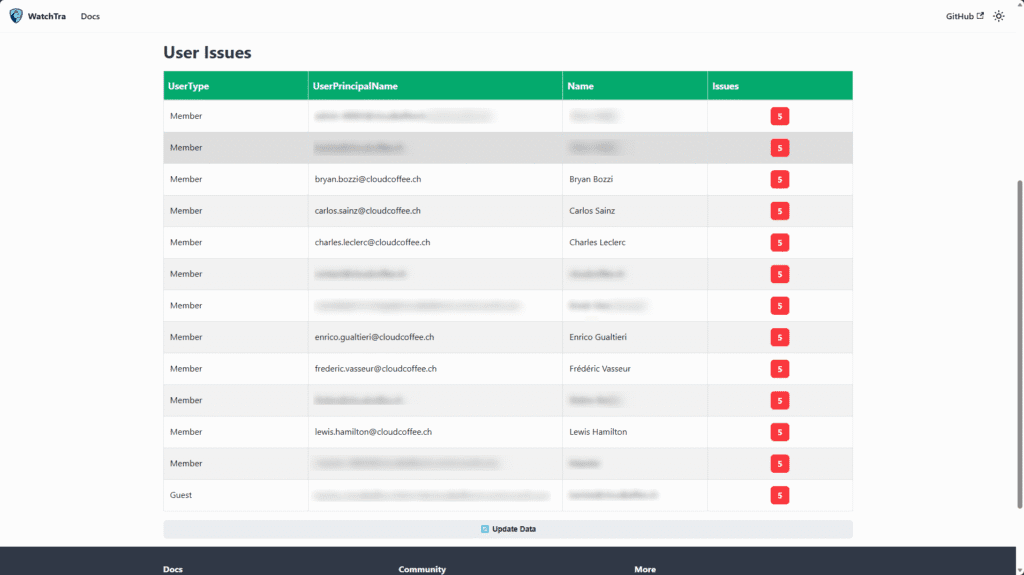
User Issues
Under User Issues, all user objects with deviations from the defined attribute values are listed.
This view serves as the starting point for making corrections in Microsoft Entra ID.
The detail view allows administrators to review the affected attributes and their current values.
Good to Know
Updates
Data is updated automatically through an Azure Function that synchronizes all user attributes in Microsoft Entra ID with the allowed values defined in the JSON files every hour. The synchronization can also be triggered manually from the WatchTra Dashboard.
No Data Stored or Tenant Access Required
WatchTra does not store any data outside its own Azure subscription and does not access any credentials. All processing is performed exclusively within the Azure resources deployed in the respective tenant. The solution uses read-only access through the Microsoft Graph API to evaluate user attributes. This ensures that no sensitive data is exported or permanently stored.
Cost Optimization
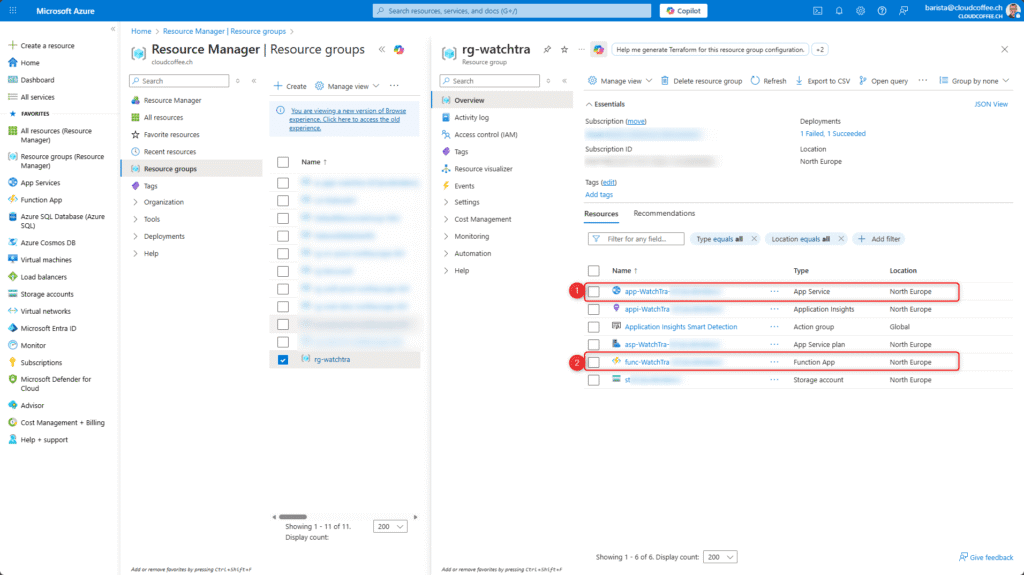
Azure provides the necessary resources for running WatchTra, resulting in monthly costs of approximately USD 70 (App Service Plan B3). If the automatic update is not required, both the App Service (1) and the Azure Function (2) can be stopped to reduce continuous costs. Before running a compliance validation, make sure that both components are started again.
Sources and Further Information
WatchTra is an open-source project by Nico Wyss (LinkedIn, Instagram, Github) and Oliver Müller (LinkedIn, BlueSky). The complete source code, technical background information and the latest releases are available on GitHub.
Conclusion
WatchTra provides a simple, transparent and technically robust way to continuously monitor attribute compliance in Microsoft Entra ID. The solution combines automation with clear visualization, delivering real value for administrators aiming to enhance data quality and governance. With its open architecture and flexible JSON configuration, WatchTra can be seamlessly integrated into existing Azure environments and tailored to meet individual compliance requirements.


