Widely used legacy authentication protocols such as POP, SMTP, IMAP or MAPI are now a serious security vulnerability and thus very popular with attackers.
The numbers on legacy authentication from one analysis are stark:
(Source: https://techcommunity.microsoft.com/t5/azure-active-directory-identity/new-tools-to-block-legacy-authentication-in-your-organization/ba-p/1225302#)
- More than 99 percent of password spray attacks use legacy authentication protocols
- More than 97 percent of credential stuffing attacks use legacy authentication
- Azure AD accounts in organizations that have disabled legacy authentication experience 67 percent fewer compromises than those where legacy authentication is enabled
what makes legacy authentication so dangerous?
Legacy authentications do not support Modern Authentication, such as multi-factor authentication or conditional access.
This guide shows how to identify clients with legacy authentication and block them with “Azure AD Conditional Access”.
Note:
Starting October 1, 2022, default authentication for Exchange Online will be permanently disabled in all Microsoft 365 tenants regardless of usage, with the exception of SMTP authentication.
Prerequisites and Licensing
This guide uses “Azure AD Conditional Access”, which requires the following license:
- Azure AD Premium P1
The license is included in “Microsoft 365 Business Premium” and many more.
An overview of Microsoft 365 license packages with their features can be found at https://m365maps.com.
Identify vulnerable client apps
In the Azure AD sign-in logs, the client apps can be filtered by user with legacy authentication.
- Add column “Client App”
- Set the period
- Add “Client App” filter
- Select all “legacy authentication clients” types
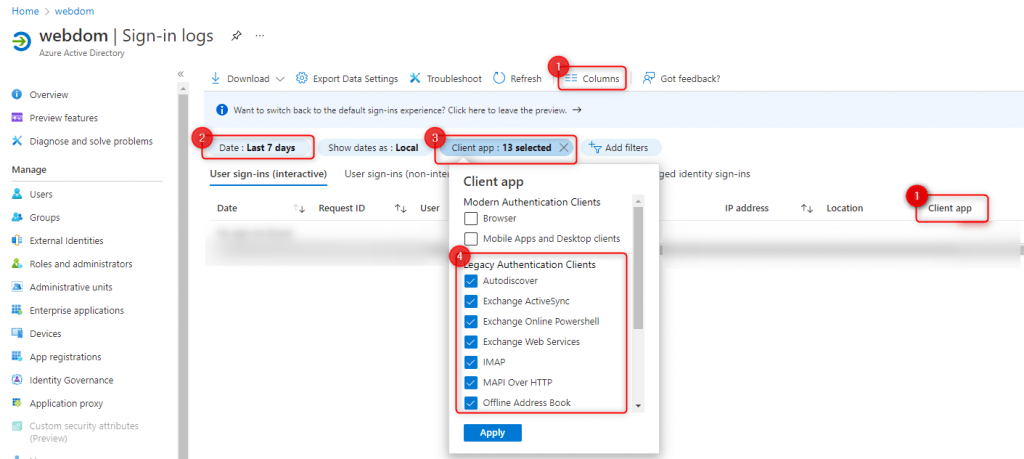
The filtered list now shows all client apps that still use legacy authentication.
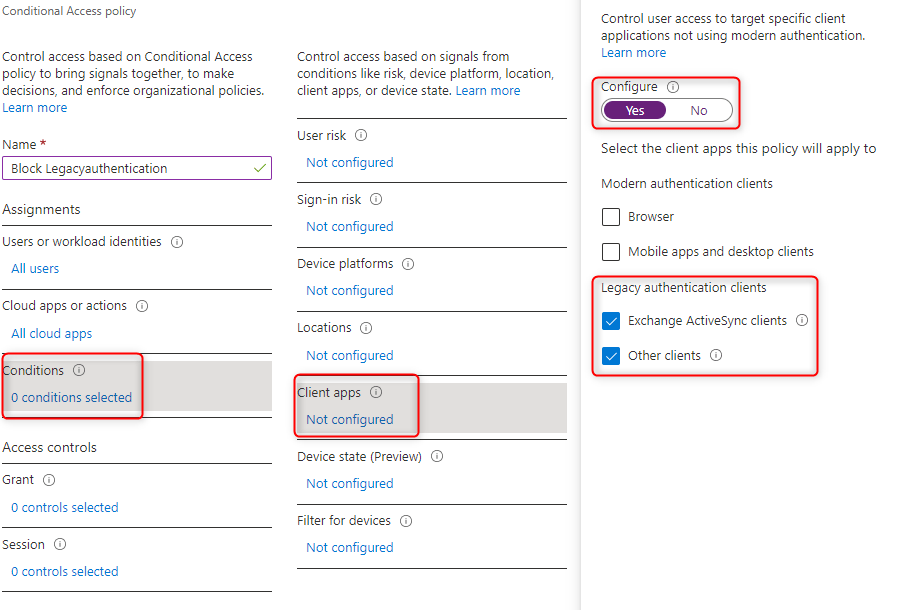
Block Legacy Authentications with Azure AD Conditional Access
After legacy authentications are no longer required, they can be blocked with Azure AD Conditional Access.
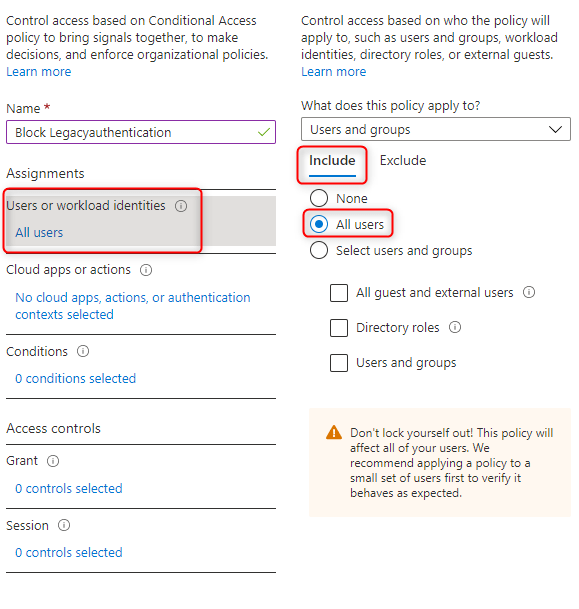
The policy should be assigned to all users and all cloud apps.
If needed, exclusions can be defined for accounts that cannot work without legacy authentication.
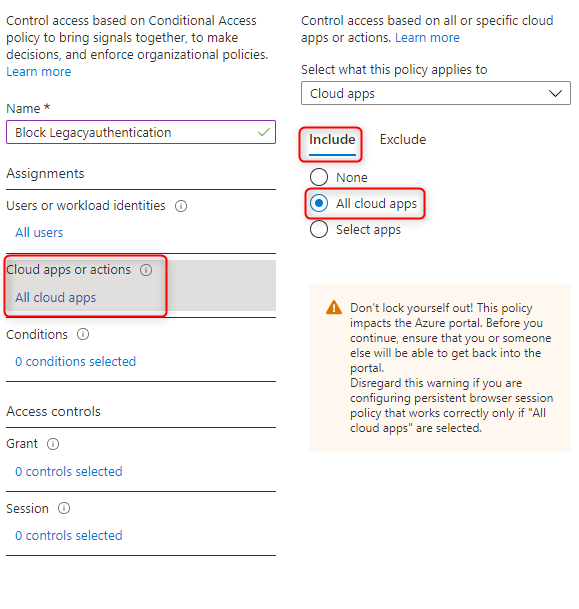
All legacy authentication clients are selected
The policy blocks access
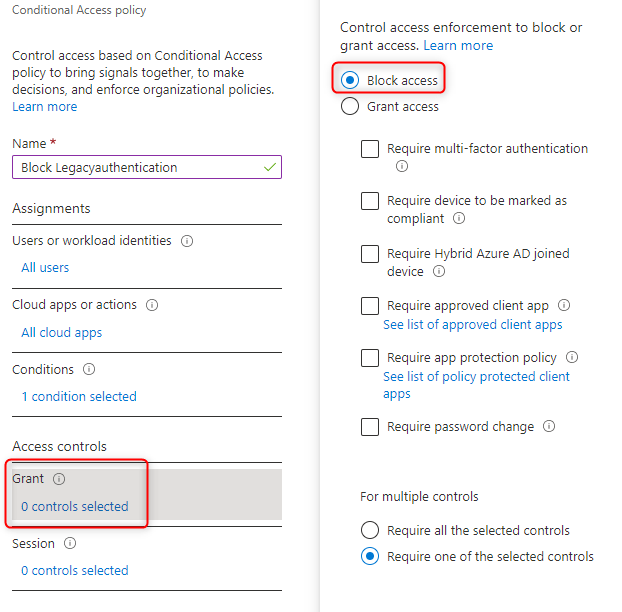
Finally, enable policy

Follow me on LinkedIn to always stay updated on my recent posts.
Was this post helpful to you? Show your enthusiasm with the delightful aroma of a freshly brewed coffee for me!

