Protect Security Info Registration with Microsoft Entra Conditional Access and Microsoft Entra ID Protection
Registration of security information such as the Microsoft Authenticator app, FIDO2 security keys or OATH tokens is a critical component of modern identity security. To protect this sensitive process, Microsoft Entra Conditional Access is used in combination with Microsoft Entra ID Protection. If a user risk or sign-in risk is detected, the Conditional Access policy prevents registration under untrusted conditions. This ensures that security-relevant information is only registered in trusted scenarios.
If registration takes place under untrusted conditions, there is a risk that an attacker may register alternative authentication methods. This could allow continued access to a compromised account even after the password has been changed. To mitigate this risk, the registration of security information must occur under trusted and controlled conditions, as defined by security information Microsoft Entra Conditional Access policy enforcement.
An introduction to the capabilities of Microsoft Entra ID Protection, including a practical configuration guide, is provided in the following article: Microsoft Entra ID Protection: Protect Identities, Detect Risks and Mitigate Threats – cloudcoffee.ch
Prerequisites and Licensing
Licenses
To protect the registration of security information, Microsoft Entra Conditional Access and Microsoft Entra ID Protection are required. Both capabilities are included in Microsoft Entra ID P2.
Microsoft Entra ID P2 is included in the following license bundles, among others:
- Microsoft 365 E5
- Enterprise Mobility + Security E5 (EMS E5)
- As a standalone Microsoft Entra ID P2 plan
Alternatively, the requirements are also met with Microsoft Entra ID P1 in combination with the Microsoft Entra Suite.
An overview of Microsoft license bundles and their included features is available at https://m365maps.com/.
Roles
For configuring the protection of security information registration, the following roles are recommended based on the principle of least privilege. In addition, a role is required that grants access to sign-in logs to verify the effectiveness of the Microsoft Entra Conditional Access policy.
| Role | Permission |
| Conditional Access Administrator | Configuration and management of Microsoft Entra Conditional Access policies |
| Reports Reader | Read access to sign-in logs |
Protect Security Information with Microsoft Entra Conditional Access
Using Microsoft Entra Conditional Access and Microsoft Entra ID Protection ensures that the registration of security information only occurs under risk-free conditions. Both user risk and sign-in risk are taken into account.
Conditional Access: Protect User Risk
User risk assesses whether a user account might be compromised, for example due to stolen credentials or unusual activities.
The Microsoft Entra Conditional Access policy for securing user risk is configured in the Microsoft Entra admin center (https://entra.microsoft.com) under Entra ID > Conditional Access > Create new policy.
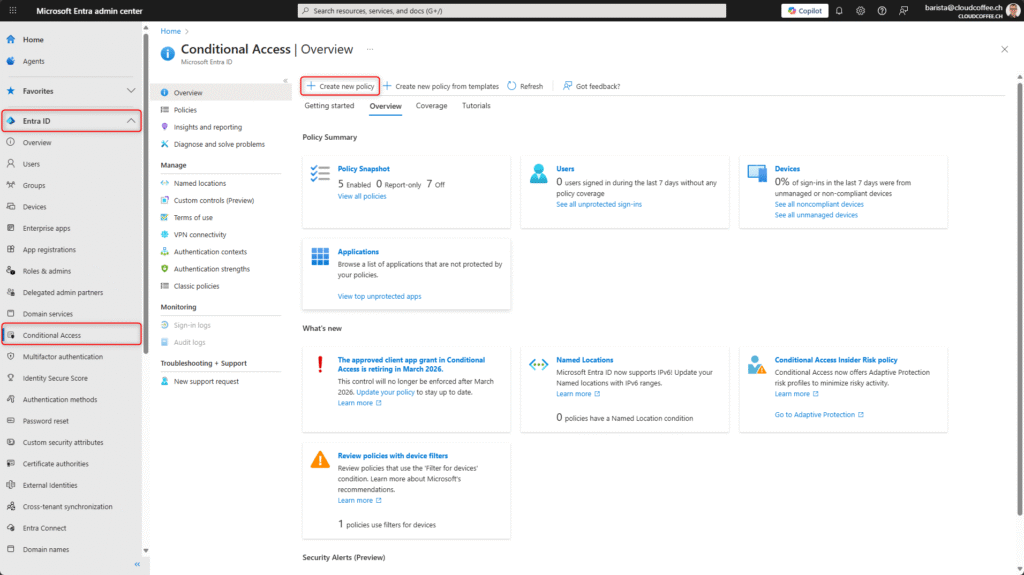
Assign a Name to the Microsoft Entra Conditional Access policy.
Naming conventions are described here: Plan a Microsoft Entra Conditional Access deployment – Microsoft Entra ID | Microsoft Learn
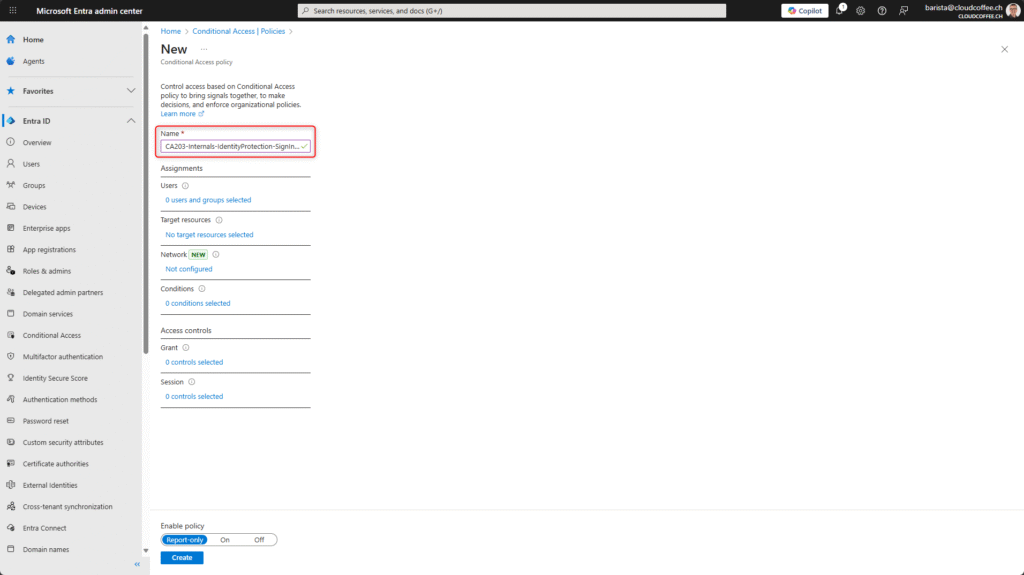
Apply the policy to All users.
Exclude emergency access accounts.
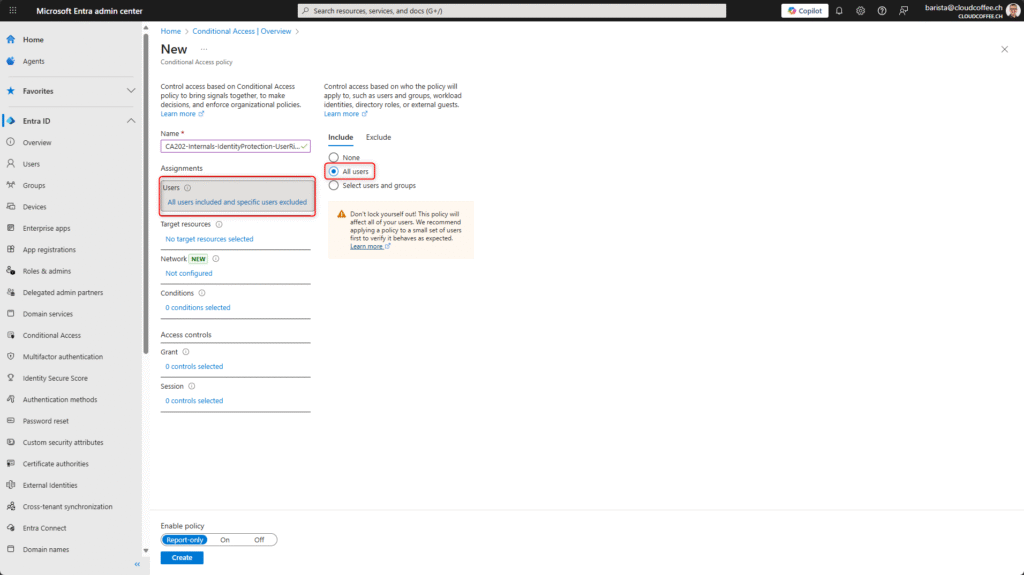
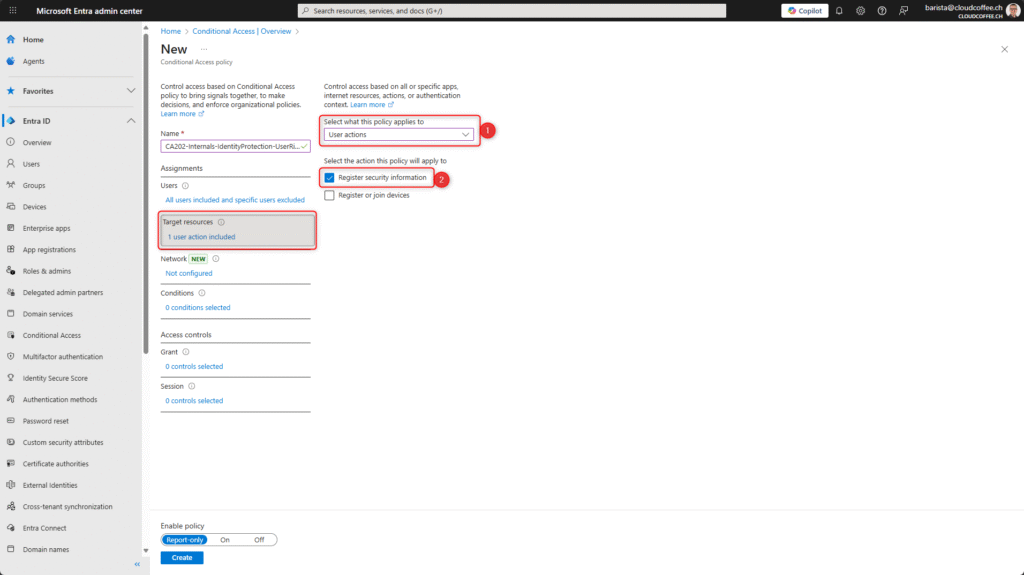
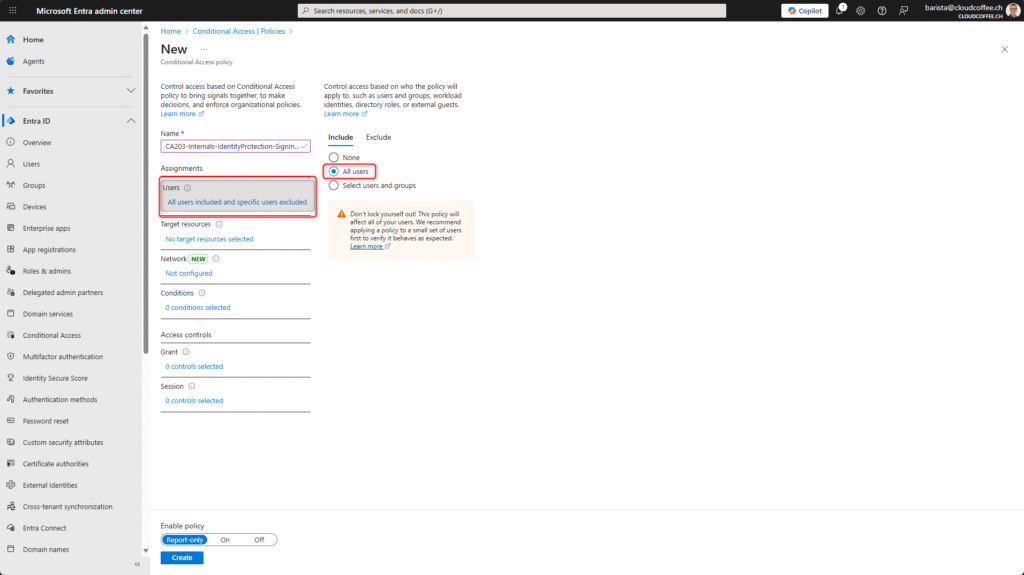
Under Target resources, select the option User actions (1) and enable Register security information (2).
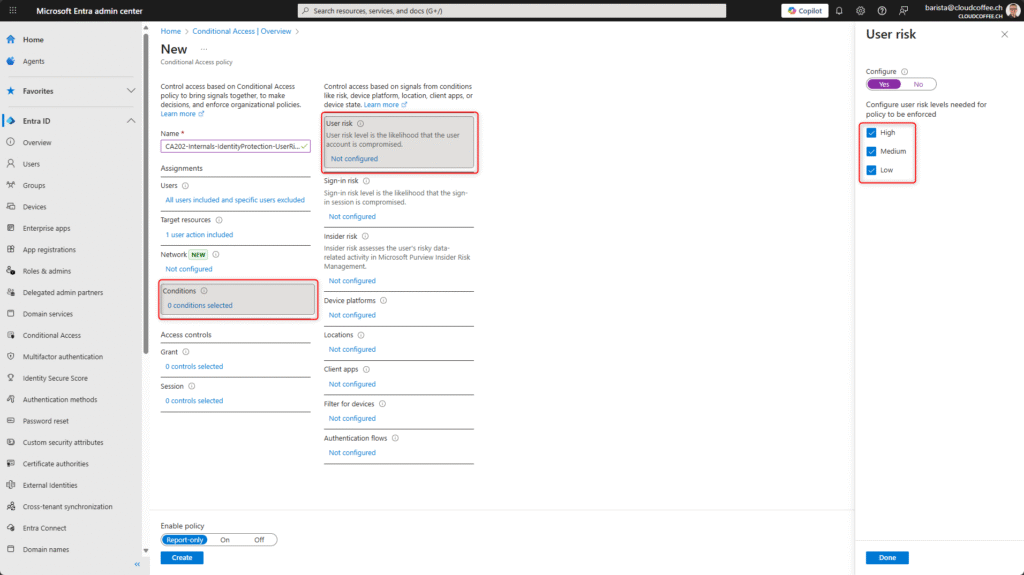
Under Conditions > User risk, enable the risk levels Low, Medium and High. This ensures that the policy is applied whenever any user risk is detected.
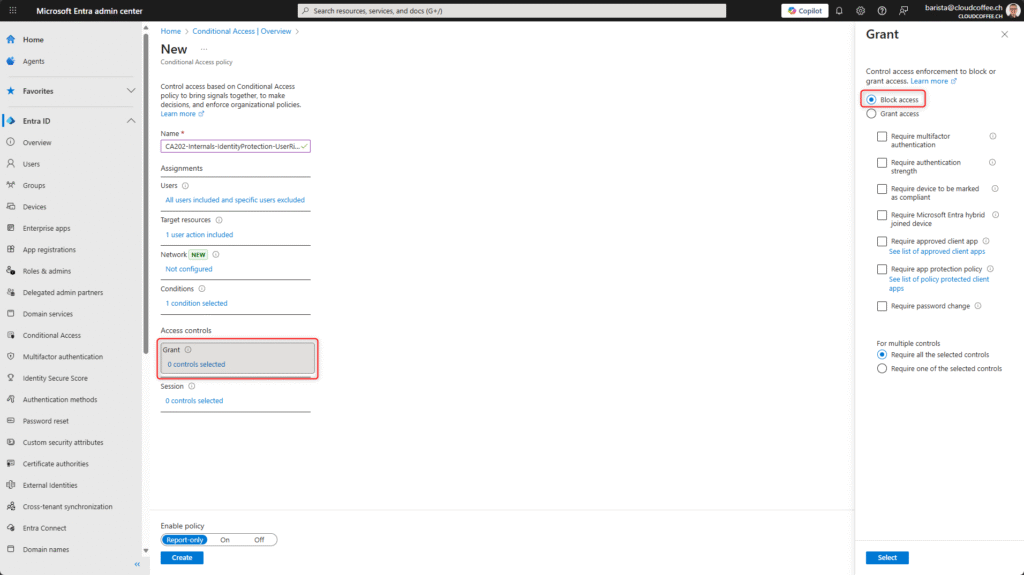
Under Grant, select the option Block access.
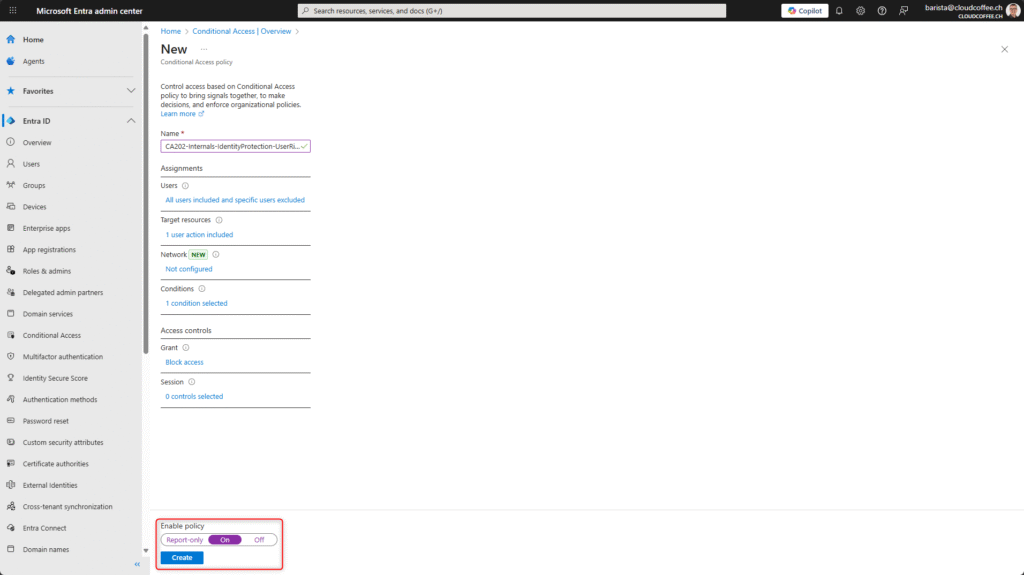
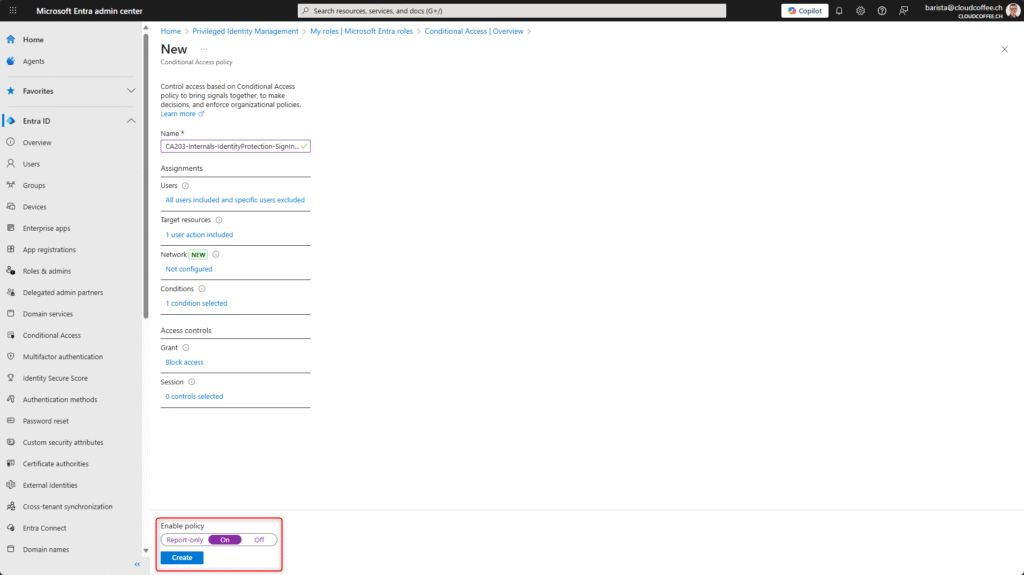
Enable the policy by selecting On and then save it with Create.
Conditional Access: Protect Sign-in Risk
Sign-in risk evaluates the risk of a current sign-in, such as from unfamiliar locations or anonymous IP addresses.
The Microsoft Entra Conditional Access policy for securing sign-in risk is configured in the Microsoft Entra admin center (https://entra.microsoft.com) under Entra ID > Conditional Access > Create new policy.

Assign a Name to the Microsoft Entra Conditional Access policy.
Naming conventions are described here: Plan a Microsoft Entra Conditional Access deployment – Microsoft Entra ID | Microsoft Learn
Apply the policy to All users.
Exclude emergency access accounts.
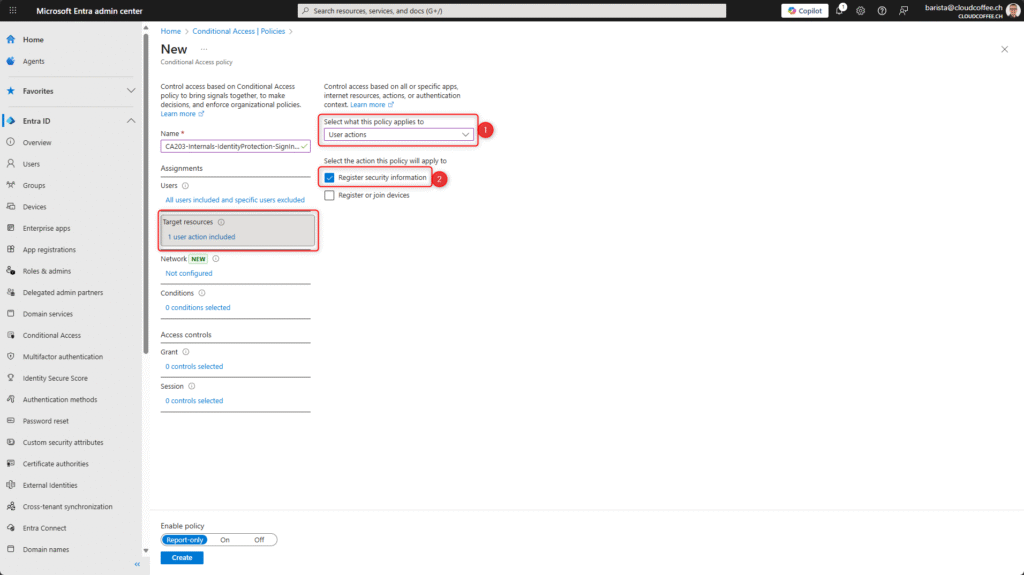
Under Target resources, select the option User actions (1) and enable Register security information (2).
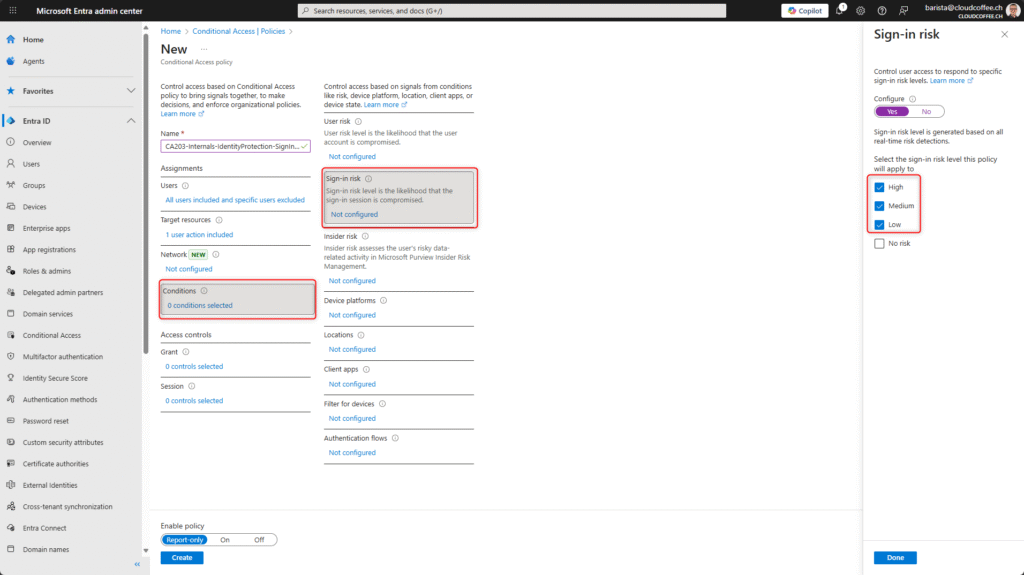
Under Conditions > Sign-in risk, enable the risk levels Low, Medium and High. This ensures that the policy is applied whenever any sign-in risk is detected.
Under Grant, select the option Block access.
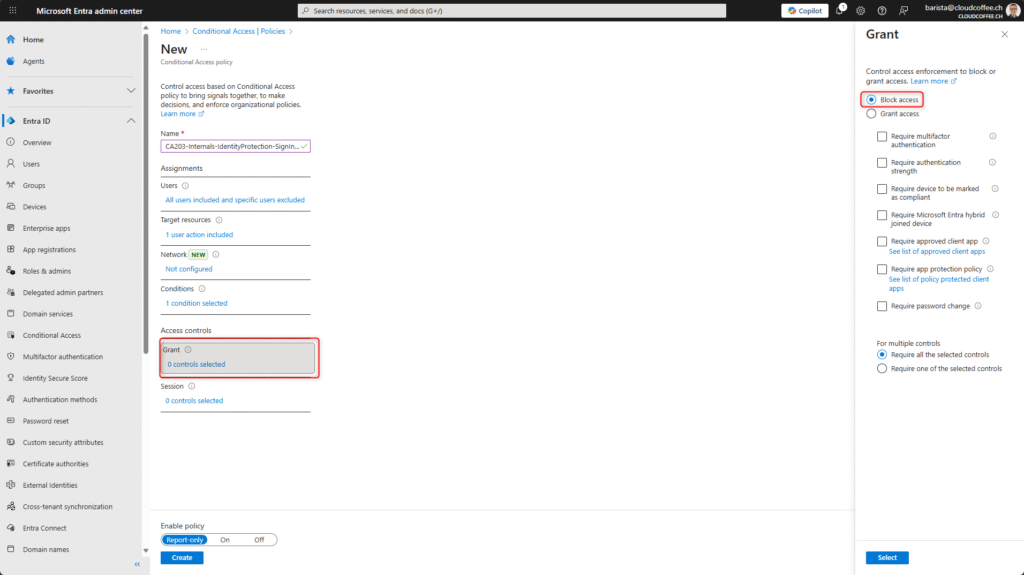
Enable the policy by selecting On and then save it with Create.
Functional Verification: Validate Microsoft Entra Conditional Access
Risk Simulation Using Tor Browser
To validate the Microsoft Entra Conditional Access policy, a sign-in attempt is performed using a user account via the Tor Browser. The anonymous IP address triggers a sign-in risk.
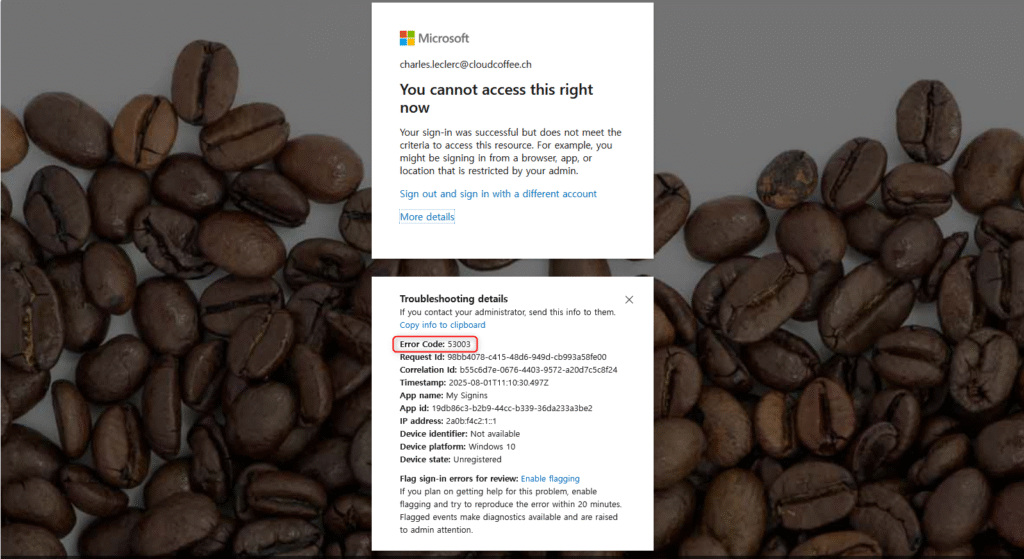
After a successful sign-in at https://myaccount.microsoft.com and accessing the Security info page, access is denied with Error Code 53003. This error code indicates that a Microsoft Entra Conditional Access policy is active and has blocked the request.
A complete list of all AADSTS error codes with descriptions is available at: Microsoft Entra authentication & authorization error codes – Microsoft identity platform | Microsoft Learn
Sign-in Logs
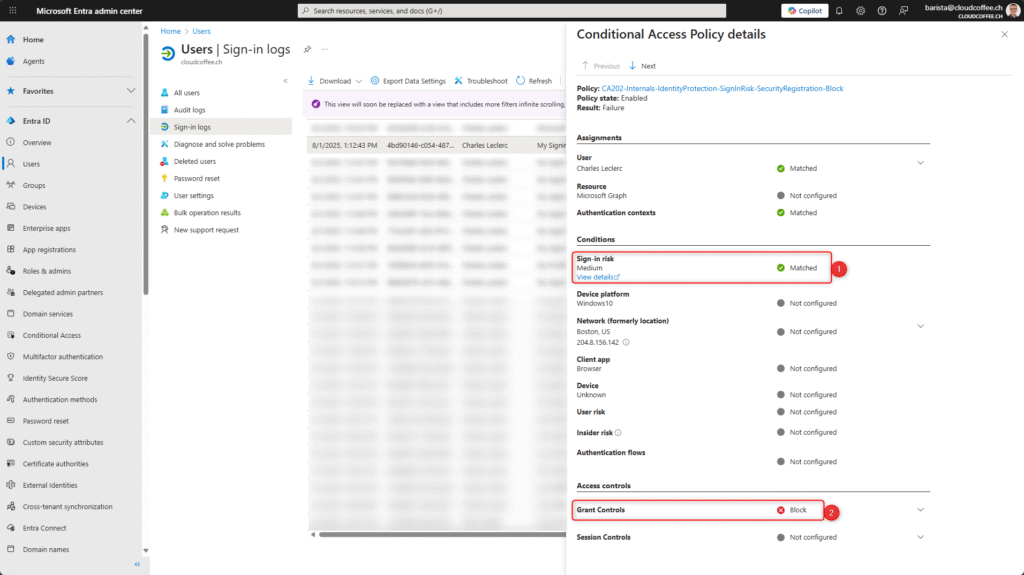
The blocking of security information registration by the Microsoft Entra Conditional Access policy is recorded in the sign-in log with Error Code 53003.
Microsoft Entra admin center (https://entra.microsoft.com) > Entra ID > Users > Sign-in logs
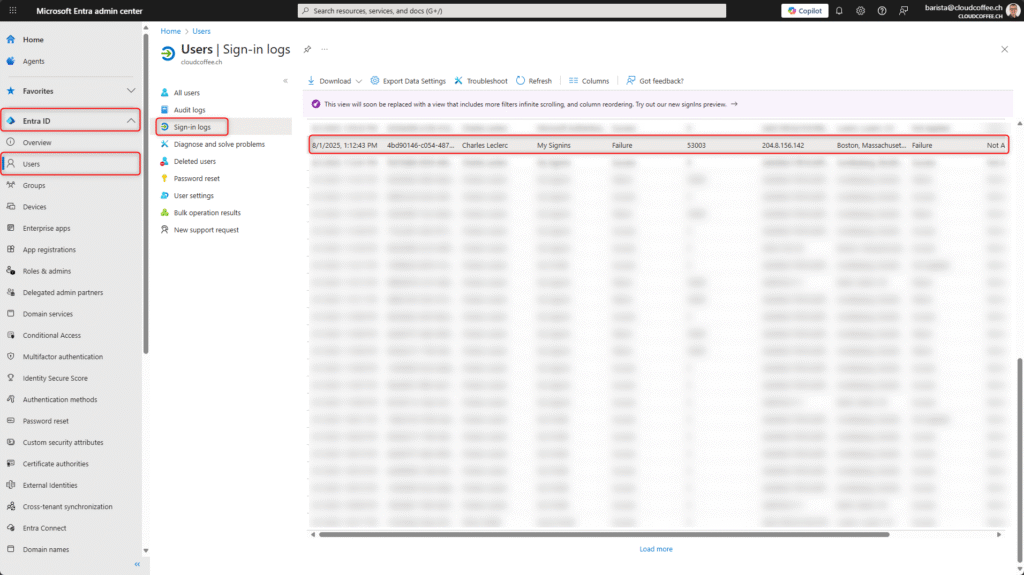
The details show that the Microsoft Entra Conditional Access policy has blocked the registration of new security information (2) due to the detected sign-in risk (1).