Microsoft Entra ID: Admin Consent Workflow for Secure Application Permissions
Last Updated on 20. August 2025
The Admin Consent Workflow in Microsoft Entra ID is a feature designed to manage user consent for enterprise application permissions. It allows administrators to review, approve, or deny permission requests before access is granted. Instead of allowing users to grant extensive permissions directly, the Admin Consent Workflow ensures that only authorized applications can access sensitive data. For instance, an application might request permission to access a user’s profile or read the contents of their mailbox. By introducing this workflow, organizations can effectively enforce the principle of least privilege and reduce the risk of unintentional data exposure.
This blog post provides a guide on how to configure the Admin Consent Workflow in Microsoft Entra ID. It demonstrates how users can submit permission requests for applications and how these requests can be reviewed and processed.
Prerequisites and Licensing
Licensing
The Admin Consent Workflow in Microsoft Entra ID requires the following license:
- Microsoft Entra ID Free or higher
An overview of Microsoft licensing plans and their features is available at https://m365maps.com/.
Roles
For configuring the Admin Consent Workflow, reviewing requests, and approving or denying access requests, the following roles are appropriate based on the principle of least privilege:
| Role | Description |
| Global Administrator | Configure and enable the Admin Consent Workflow; review, approve, or deny permission requests |
| *Privileged Role Administrator *Cloud Application Administrator | Review, approve, or deny permission requests |
* Details about these roles can be found here: Grant tenant-wide admin consent to an application – Microsoft Entra ID | Microsoft Learn
Configuring the Admin Consent Workflow in Microsoft Entra ID
Configuring User Consent in Microsoft Entra ID
User Consent in Microsoft Entra ID controls whether, and to what extent, users are allowed to grant applications access to organizational data. Without centralized control, there is a risk that users may unintentionally authorize applications to access sensitive information without being aware of potential security or compliance implications.
User consent is configured in the Microsoft Entra admin center https://entra.microsoft.com) by navigating to Entra I > Enterprise apps > Consent and permissions > User consent settings.
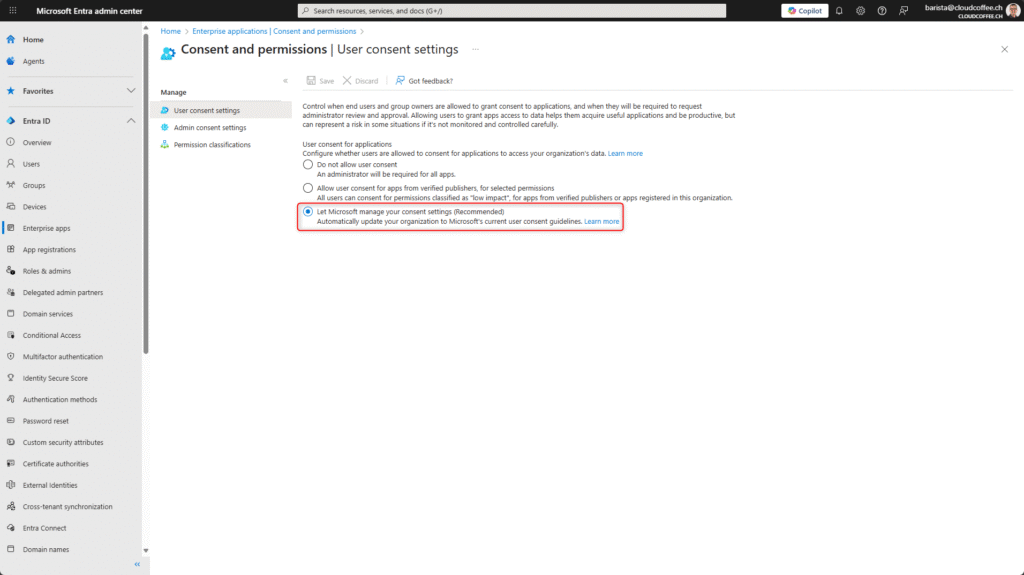
The following options are available when configuring user consent, allowing you to control third-party app access to organizational data:
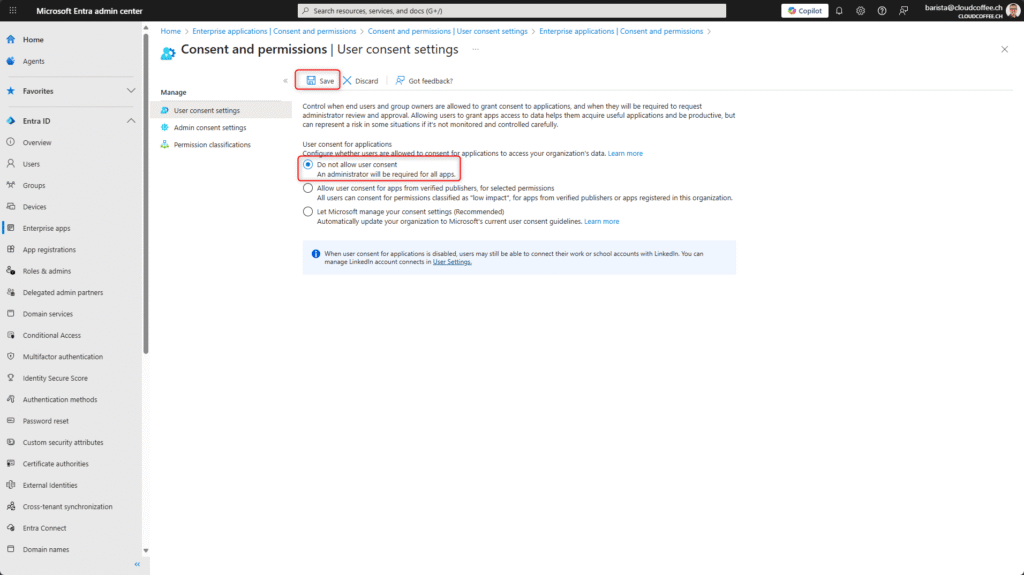
- Do not allow user consent
Only administrators can authorise applications to access data. This option offers the highest level of security, but requires more administrative effort. - Allow user consent for selected permissions
Users can authorize applications from verified publishers if the requested permissions are classified as low impact. Approved permissions are defined through permission classifications. This setting offers a balanced approach between security and usability. - Let Microsoft manage your consent settings
Users can authorize applications with low-impact delegated permissions themselves; however, critical permissions such as Files.Read.All, Files.ReadWrite.All, Sites.Read.All, and Sites.ReadWrite.All are excluded. The policy is automatically maintained by Microsoft and updated according to the latest security recommendations, with a minimum of 30 days prior notice for any changes.
For maximum security, it is recommended to select the Do not allow user consent option.
Enabling the Admin Consent Workflow in Microsoft Entra ID
Admin Consent in Microsoft Entra ID enables secure and controlled management of application permissions. It governs how users can submit consent requests for applications that require permissions they are not authorized to approve themselves. By leveraging the Admin Consent Workflow, access to sensitive resources is effectively controlled, enhancing the overall security of the environment.
Admin consent is configured in the Microsoft Entra admin center (https://entra.microsoft.com) by navigating to Entra ID > Enterprise apps > Consent and permissions > Admin consent settings.
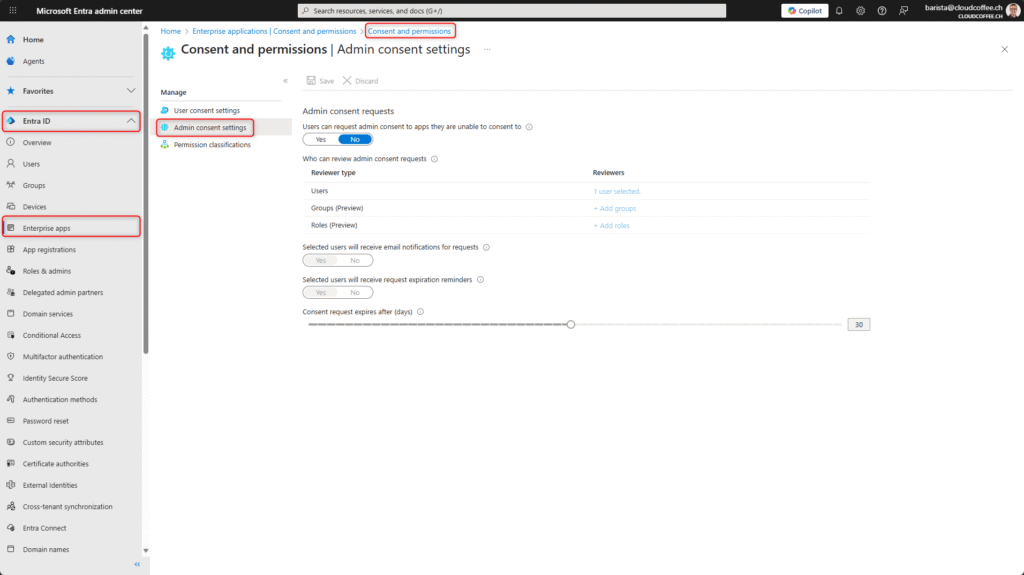
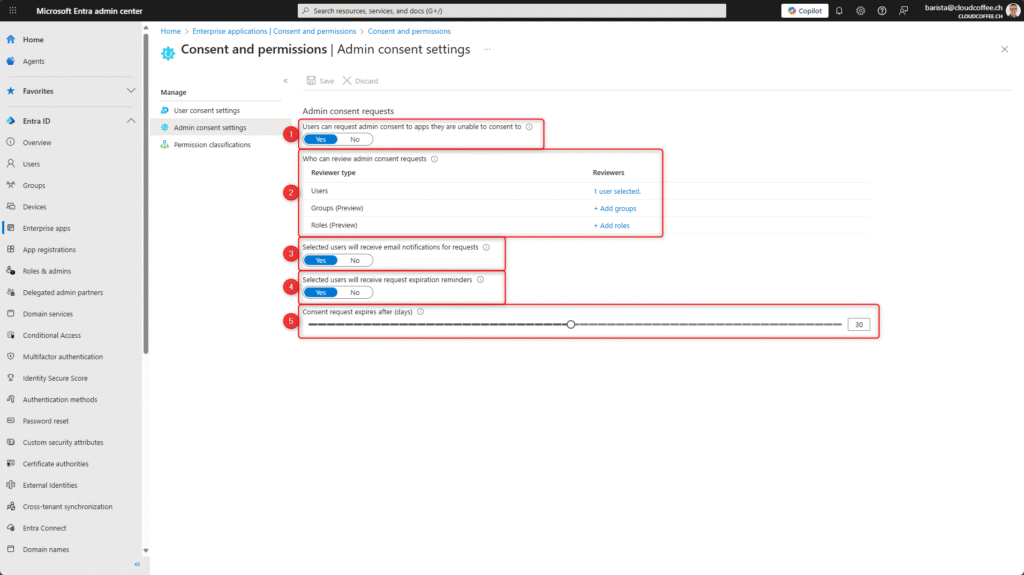
The following options can be configured in the Admin Consent Workflow to control the approval process:
- Enable Admin Consent Workflow
Set this option to Yes to activate the Admin Consent Workflow, allowing users to submit access requests to designated reviewers. - Assign reviewers
Specify users, groups, or roles responsible for reviewing and approving access requests. - Enable email notifications
Notify reviewers via email when new access requests are submitted. - Configure reminder emails
Send reminder emails to reviewers when a request is nearing expiration and has not yet been processed. - Define request expiration period
Set the maximum validity period for pending access requests before they automatically expire.
Permission Classifications in Microsoft Entra ID
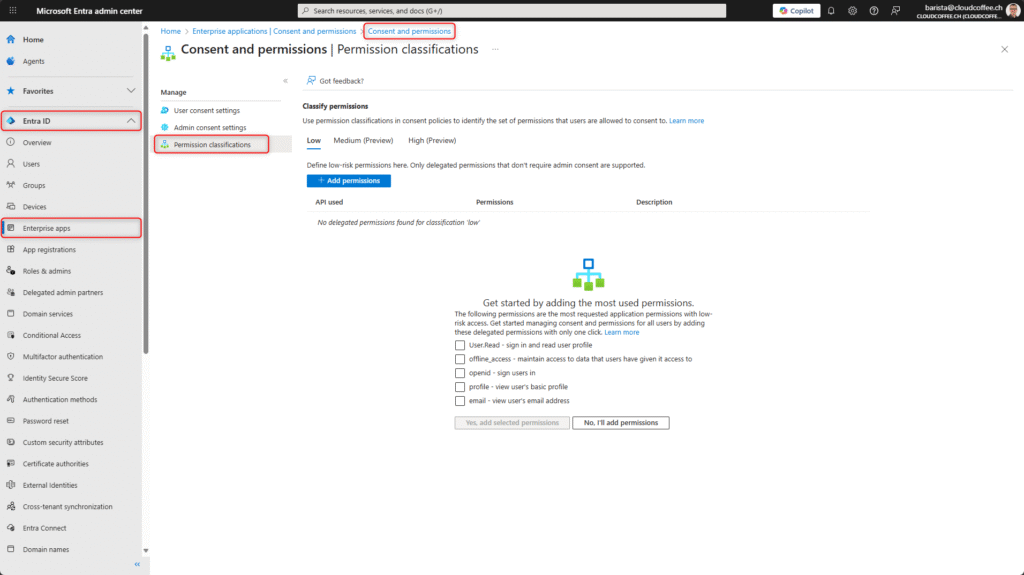
Permission Classifications in the Microsoft Entra admin center allow API permissions to be categorized based on their risk profile, such as low, medium, or high. This classification enables automated user consent decisions, allowing users to grant certain permissions without requiring additional approval.
API permission classifications are configured in the Microsoft Entra admin center (https://entra.microsoft.com) by navigating to Entra ID > Enterprise apps > Consent and permissions > Permission classifications.
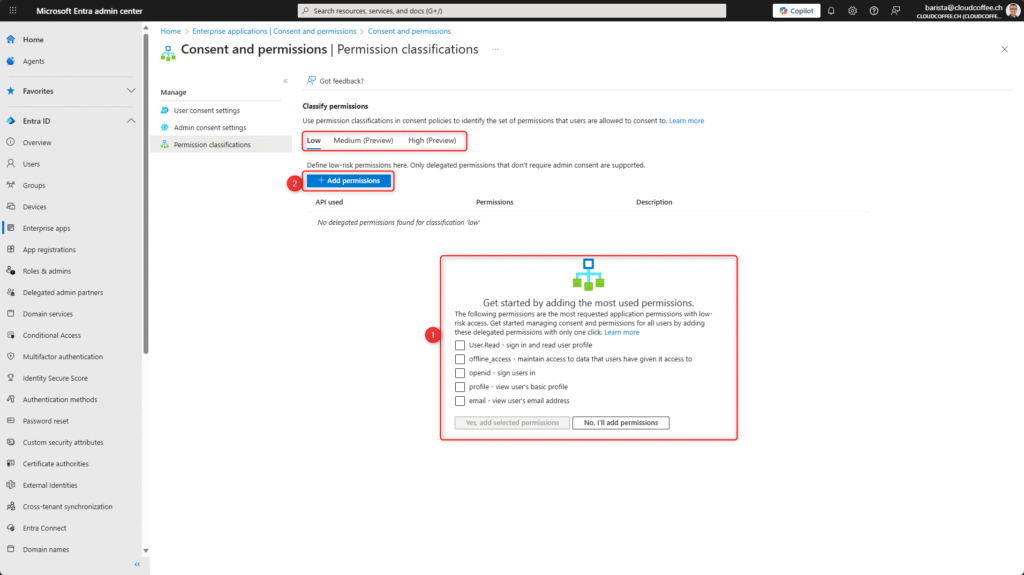
Classifications can be configured either broadly for most commonly requested application permissions (1), or granularly on a per-API basis (2).
Admin Experience and User Experience
User Experience
If a user is not authorized to approve a permission request for an enterprise application, a corresponding message is displayed. By providing a justification (1) and clicking Request approval (2), the Admin Consent Workflow is initiated.

The approval request has been successfully submitted and is now pending further action by an reviewer.

Admin Experience
Each reviewer receives the approval request via email.

Requests are managed in the Microsoft Entra admin centre (https://entra.microsoft.com) by navigating to Entra ID > Enterprise apps > Admin consent requests > My Pending
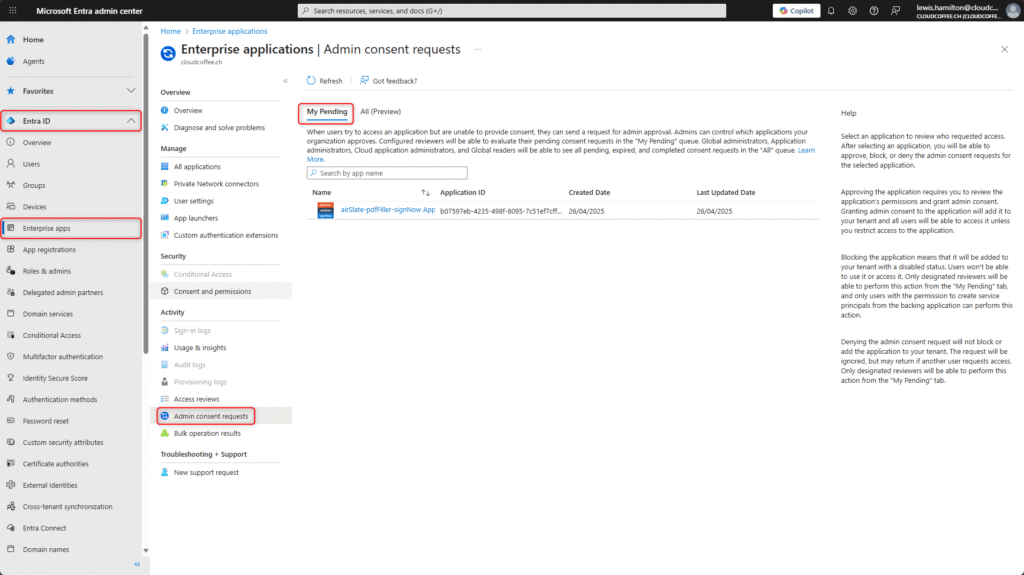
The reviewer now has the option to either deny (2) or block (1) it.
Denying means that the current approval request is rejected once. Blocking, on the other hand, prevents any future approval requests for this application from being submitted.
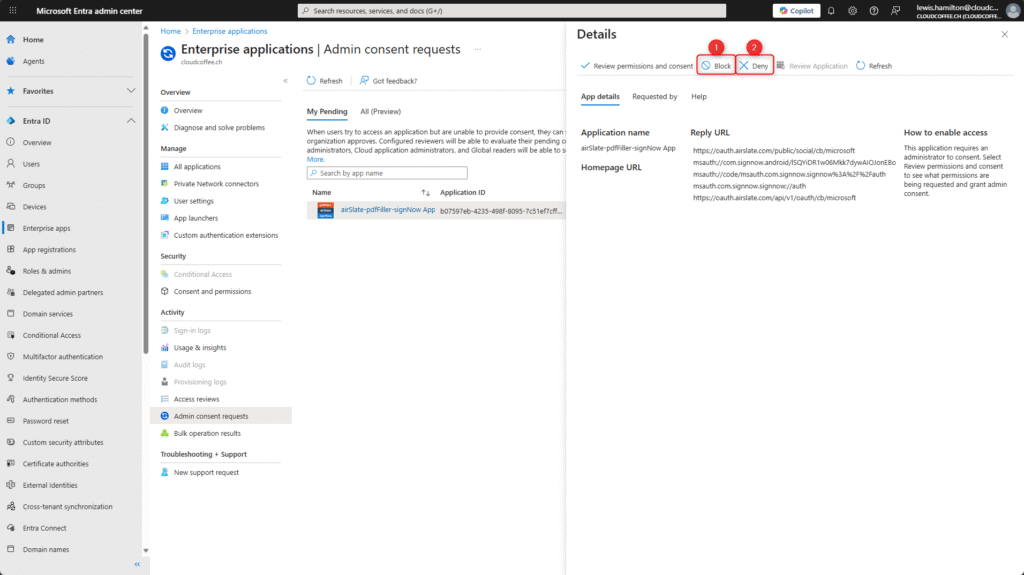
The reviewer can view, deny, or block an approval request. To view the requested permissions and approve them, one of the following roles is required: Global Administrator, Privileged Role Administrator or Cloud Application Administrator.

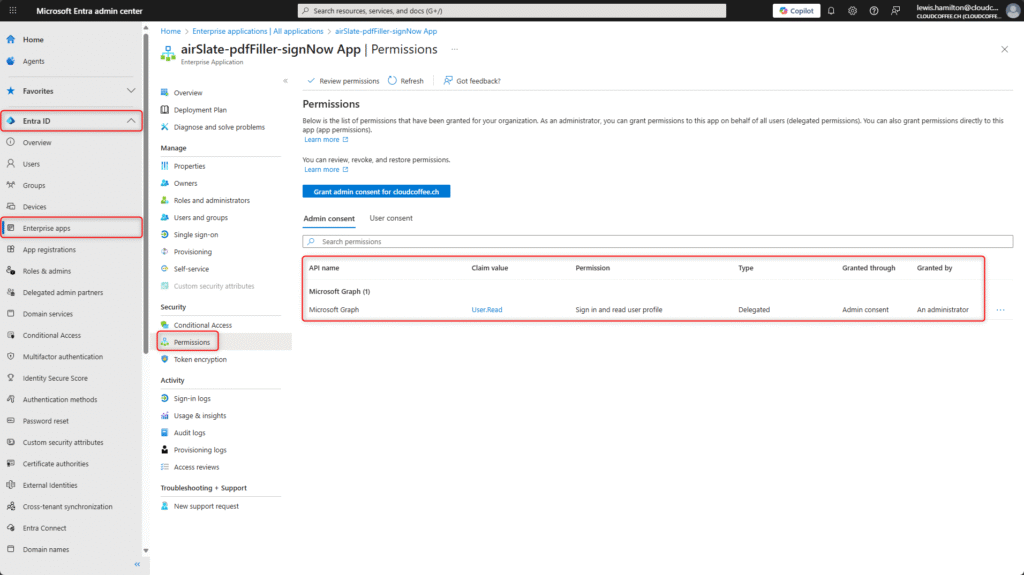
If the requested permissions are appropriate, the request can be approved by clicking Accept.

In the Microsoft Entra admin center (https://entra.microsoft.com) navigate to Entra ID > Enterprise apps > All applications > Select application > Permissions, to view the granted permissions. The application is now authorized and ready for use within the organization.
Good to Know
Microsoft’s Recommended Consent Policy Starting August 2025
Beginning in August 2025, Microsoft will introduce the recommended consent policy Let Microsoft manage your consent settings. This Microsoft-managed consent policy serves as the new standard recommendation for Microsoft Entra ID and allows end users to grant only low-risk delegated permissions. The permissions Files.Read.All, Files.ReadWrite.All, Sites.Read.All and Sites.ReadWrite.All are excluded. Microsoft automatically updates this consent policy and announces any changes at least 30 days in advance.