Enhance Token Security with Microsoft Entra and Microsoft Intune
Last Updated on 23. January 2026
When an attacker steals a user’s token after a successful login, they gain the ability to impersonate the user and access protected resources without requiring a re-login. This method is becoming more commonly used to bypass security measures like Multi-Factor Authentication (MFA).
A commonly used attack scenario is the Adversary-in-the-Middle (AiTM) attack. In this case, a fake sign-in page is presented to capture credentials and the authentication token. The attacker uses the token directly, effectively bypassing MFA.
This blog post presents some easy to implement steps to better protect against token theft. There are many other protection options that are not covered here. As the security landscape continually evolves, it’s essential to regularly review and adjust security practices to remain prepared for new threats. This article will be updated periodically to incorporate new methods and insights.
Prerequisites and Licensing
Licenses
The measures and implementation steps described in this post rely on different functionalities and therefore require various licenses. The specific license needed is indicated in each respective section.
| Feature | License |
| Microsoft Entra Conditional Access | Microsoft Entra ID P1 |
| Token protection | Microsoft Entra ID P1 |
| Microsoft Intune | Microsoft Intune P1 |
| Safe Link and Safe Attachments | Microsoft Defender für Office 365 Plan 1 |
An overview of the Microsoft license packages and their features can be accessed at https://m365maps.com/.
Roles Based on the Principle of Least Privilege
The following Microsoft Entra roles can be used for the configuration:
| Role | Permission |
| Conditional Access Administrator | Can manage Conditional Access capabilities |
| Reports Reader | Can read sign-in and audit reports |
| Intune Administrator | Can manage all aspects of the Intune product |
| Security Administrator | Creating and managing security policies |
Identity Protection
Enable Token Protection
Required License: Microsoft Entra ID P1
Token protection cryptographically binds tokens to enrolled or registered devices. This ensures that a token can only be used on the device for which it was issued. As a result, it prevents tokens from being used on another device and exploited by attackers. Token protection leverages signatures composed of device information and security attributes.
Token protection is generally available for Windows and in preview for iOS and macOS. It is supported in Microsoft Entra Conditional Access for mobile apps and desktop applications accessing Exchange Online, SharePoint Online and Microsoft Teams. With the Windows app, it also covers Azure Virtual Desktop, Windows 365 and Windows Cloud Login.
Token protection is enabled through Microsoft Entra Conditional Access.
Open Microsoft Entra admin center (https://entra.microsoft.com) and navigate to Entra ID > Conditional Access, then select Create new policy.
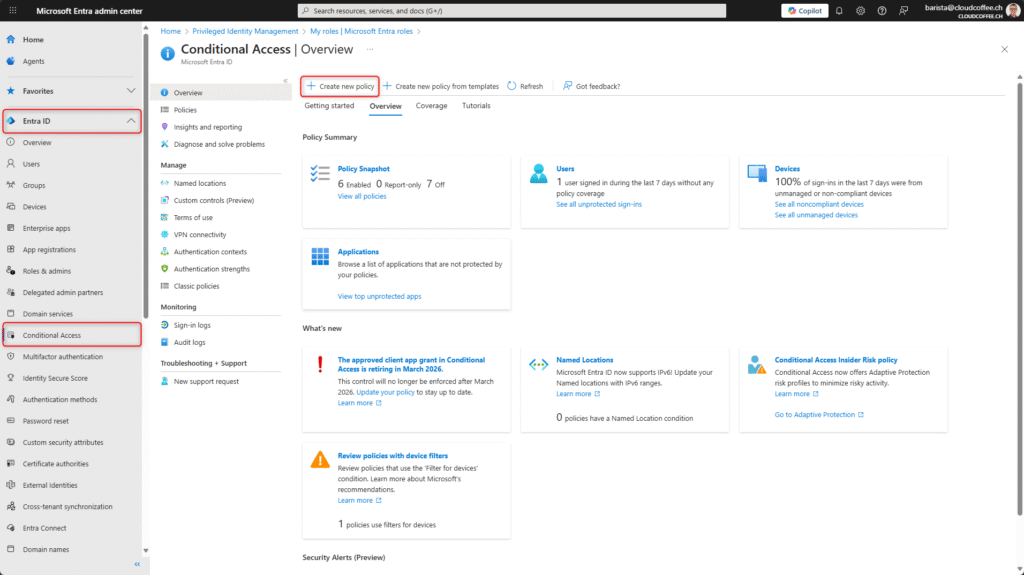
Assign a Name to the Microsoft Entra Conditional Access policy.
Naming conventions are outlined in the following documentation: Plan a Microsoft Entra Conditional Access deployment – Microsoft Entra ID | Microsoft Learn
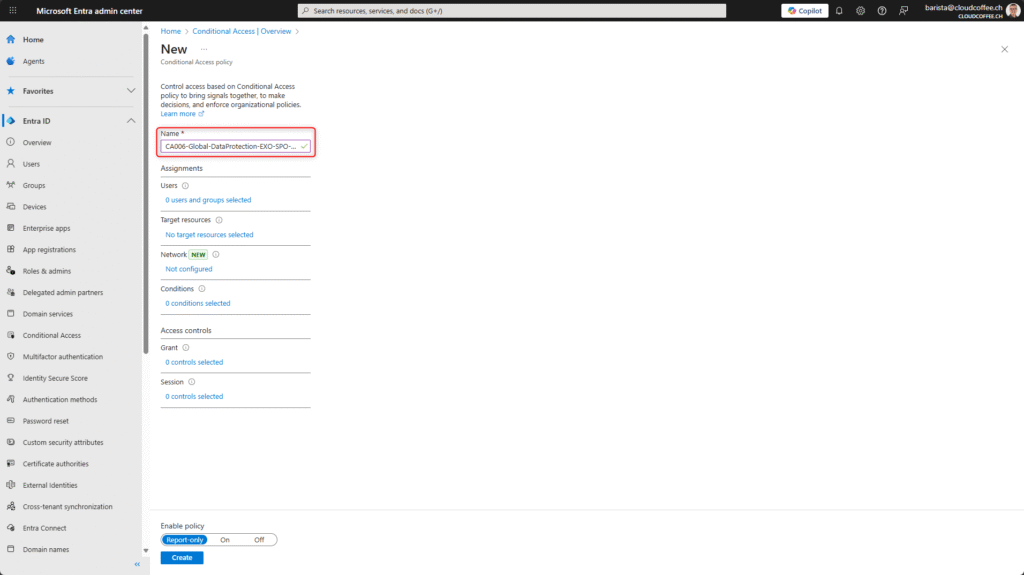
Select Users and groups for this policy. Emergency accounts should be excluded.
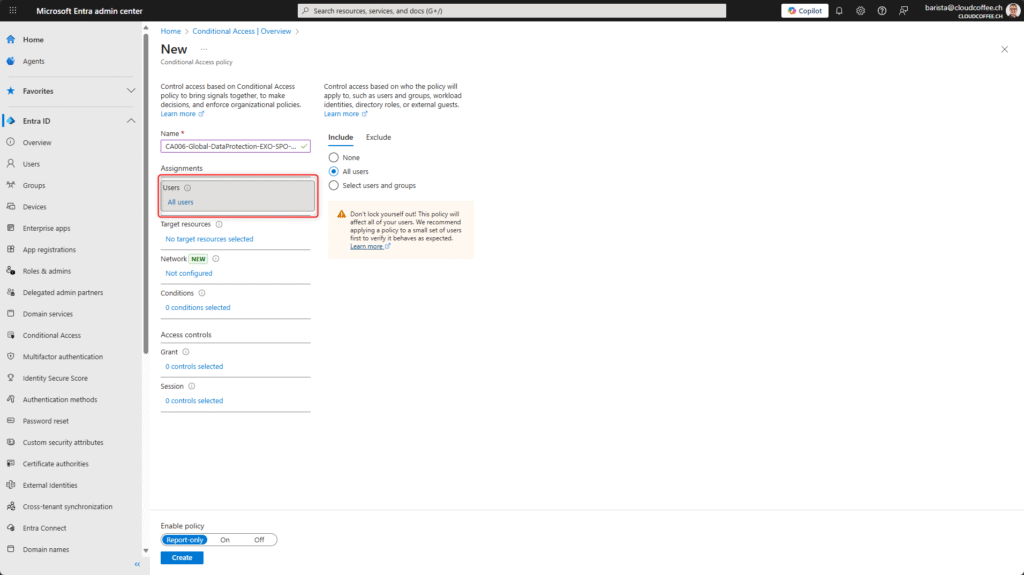
Set the Target resources to Office 365 Exchange Online, Office 365 SharePoint Online and Microsoft Teams Services. As of the time of writing this blog post, these are the only resources that support token protection.
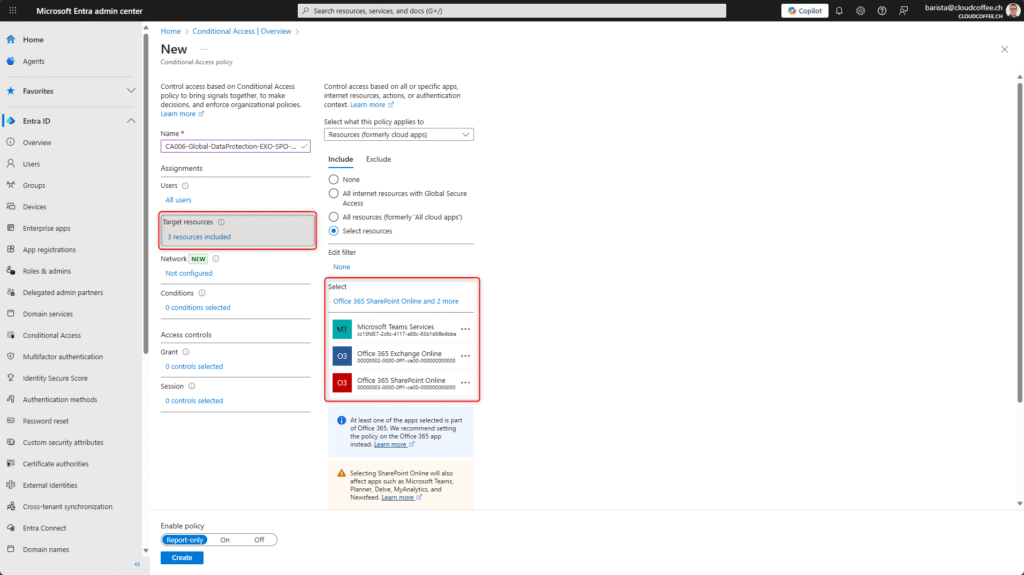
Set the Conditions for the Device platform to Windows (generally available). macOS and iOS are currently in preview.
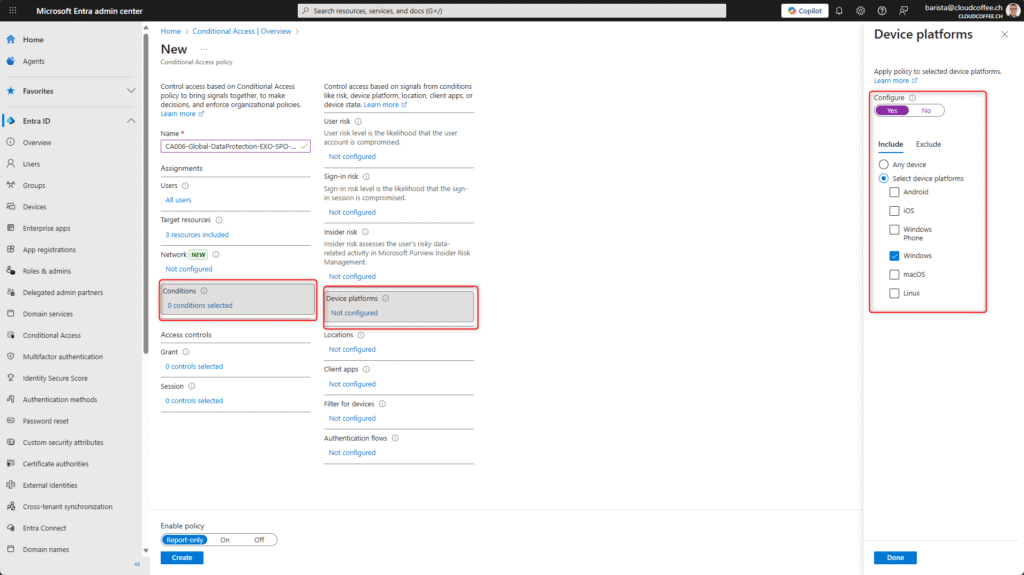
Set the Conditions for the Client apps to Mobile apps and desktop clients.
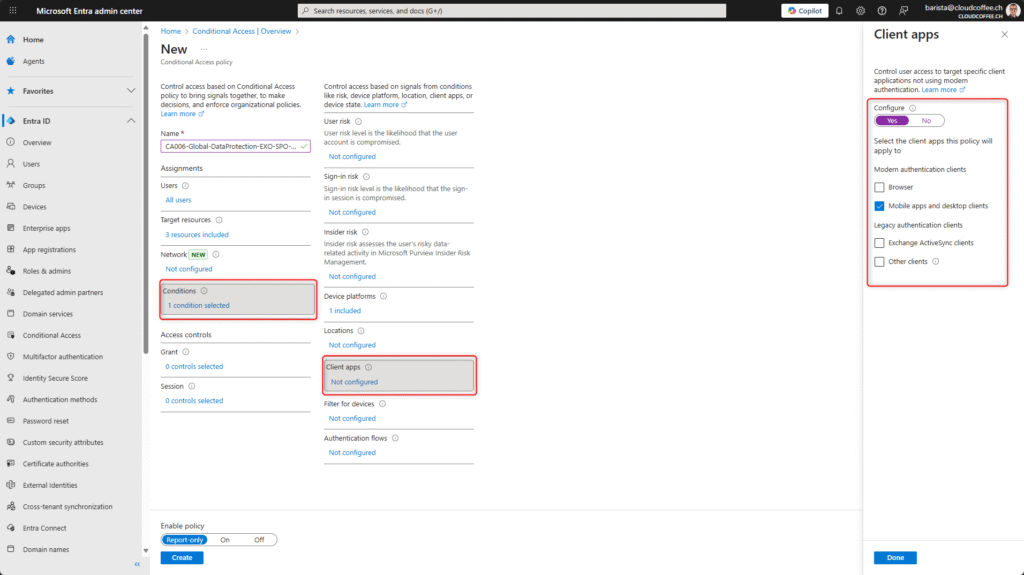
Under Session, enable the feature Require token protection for sign-in sessions.
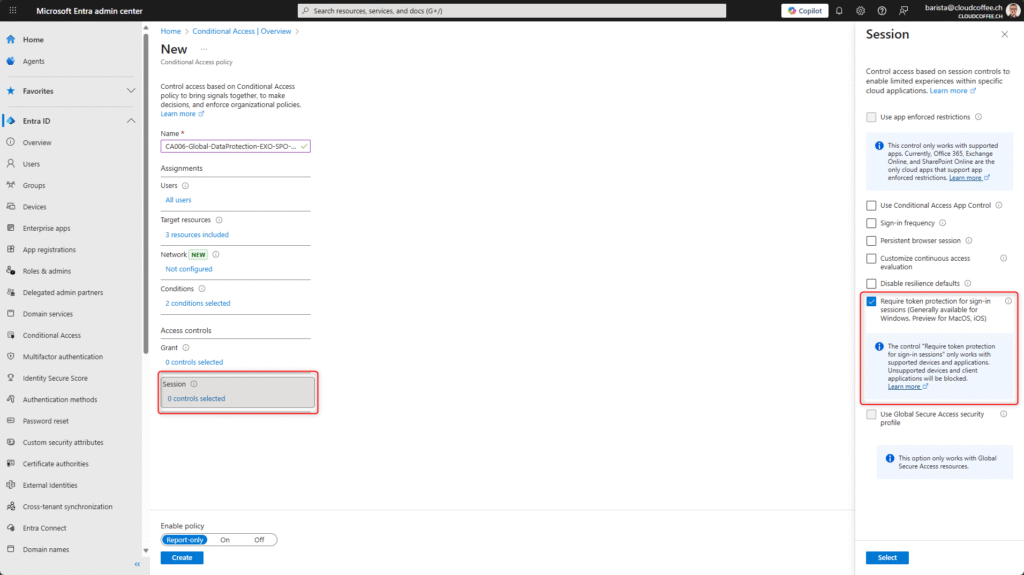
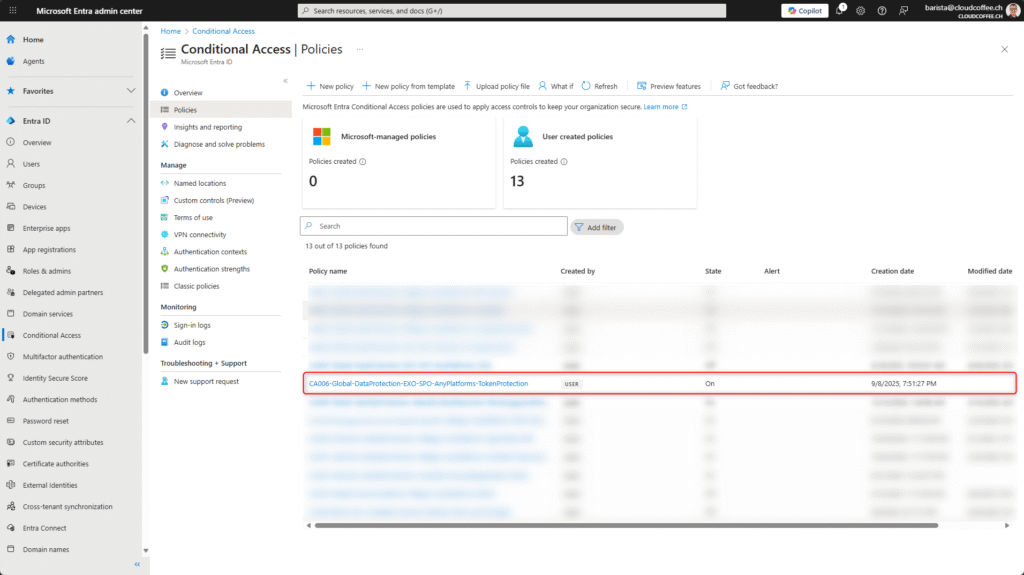
The policy is enabled with On and saved with Save.
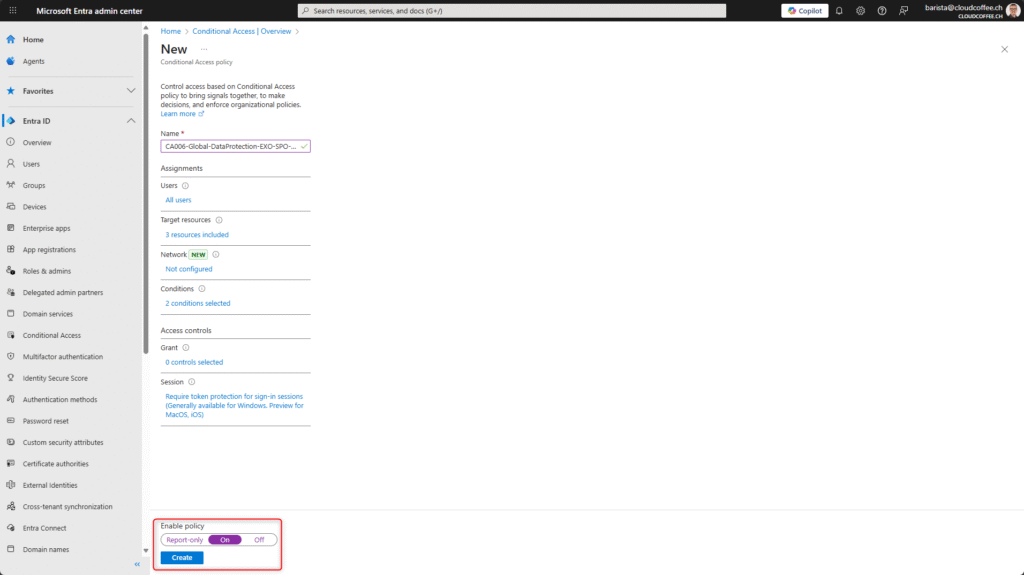
The policy has been successfully created, and token protection has been activated.
Functionality check
Sign-in with a enrolled or registered device
The implementation of Microsoft Entra Conditional Access for token protection can be tracked in the sign-in logs. In the following example, the sign-in was performed on an enrolled or registered device.
Microsoft Entra admin center (https://entra.microsoft.com) > Identity > Users > All users > Sign-in logs

Sign-in with an unenrolled or unregistered device
If a user signs in from an unenrolled or unregistered device, they will be prompted to register or enroll the device before a token can be issued.

The sign-in log shows that the token could not be issued.
Microsoft Entra admin center (https://entra.microsoft.com) > Identity > Users > All users > Sign-in logs

Microsoft Entra ID Protection
Required License: Microsoft Entra ID P2
Microsoft Entra ID Protection provides a powerful mechanism for detecting risky sign-ins and compromised user accounts at an early stage and responding to them in an automated manner.
By combining real-time analytics, machine learning, and adaptive policies, it enables proactive identity protection.
A detailed configuration guide is available in the following post:
Microsoft Entra ID Protection: Protect Identities, Detect Risks and Mitigate Threats – cloudcoffee.ch
Device Security
Enforce Device Compliance
Required Licenses: Microsoft Entra ID P1 und Microsoft Intune P1
Device compliance can be verified using Microsoft Entra Conditional Access. The compliance criteria can be customized individually in Microsoft Intune. A detailed description of these configuration options is beyond the scope of this blog post. For more information: Create device compliance policies in Microsoft Intune | Microsoft Learn
Open Microsoft Entra admin center (https://entra.microsoft.com) and navigate to Protect > Conditional Access, then select Create new policy
Assign a Name to the Microsoft Entra Conditional Access policy.
Naming conventions are outlined in the following documentation: Plan a Microsoft Entra Conditional Access deployment – Microsoft Entra ID | Microsoft Learn

Select Users and groups for this policy, ensuring that Emergency accounts and, if necessary, additional accounts are excluded to prevent accidental lockout.

Set the Target resources to All Resources (formerly All Cloud Apps). Alternatively, you can choose specific applications, such as SharePoint Online or Exchange Online.

If needed, additional granular criteria can be configured under Conditions, such as applying the policy only to specific device platforms like Windows, Android, or iOS.

Enable the option Require device to be marked as compliant under Grant. This enforces the device compliance policy from Microsoft Intune, allowing only devices that meet the requirements of this policy.

Review the configuration to ensure that accounts are not accidentally locked out. If needed, the Microsoft Entra Conditional Access policy can also be tested in Report-only mode.
The policy is enabled with On and saved with Save.

The policy has been successfully created and enforces device compliance.

Functionality check
User Sign-In
When trying to sign in to an application with a device that does not meet the compliance policies, the following error message will appear.
Error code 53000 indicates that the device does not meet the compliance requirements.
A comprehensive overview of the AADSTS error codes and their descriptions is available for further details: Microsoft Entra authentication & authorization error codes – Microsoft identity platform | Microsoft Learn

Sign-in Logs
The sign-in attempt will appear in the sign-in logs with the sign-in error 53000.
Microsoft Entra admin center (https://entra.microsoft.com) > Identity > Users > All users > Sign-In logs

Check Enrolled or Registered Devices
Required License: Microsoft Entra ID P1
A Microsoft Entra Conditional Access policy checks whether devices in Microsoft Entra are Microsoft Entra joined, hybrid joined or registered. If the devices are not enrolled or registered in any of these ways, access will be blocked.
Open Microsoft Entra admin center (https://entra.microsoft.com) and navigate to Protect > Conditional Access, then select Create new policy.

Assign a Name to the Microsoft Entra Conditional Access policy.
Naming conventions are outlined in the following documentation: Plan a Microsoft Entra Conditional Access deployment – Microsoft Entra ID | Microsoft Learn

Select Users and groups for this policy, ensuring that Emergency accounts and, if necessary, additional accounts are excluded to prevent accidental lockout.

Set the Target resources to All Resources (formerly All Cloud Apps). Alternatively, you can choose specific applications, such as SharePoint Online or Exchange Online.

The devices enrollment is checked under Conditions.
1. Select Filter for devices
2. Set Configure to Yes
3. Select the option Exclude filtered devices from policy
4. Set TrustType to the desired values when multiple registration types are allowed, ensuring that the logical operator is set to OR
– Microsoft Entra joined
– Microsoft Entra hybrid joined
– Microsoft Entra registered
5. Click Add expression
6. The filter criterion will be inserted
7. Save the filter with Done

Activate the Block access option under Grant. The policy should block all devices that do not meet the device filter criteria.

Review the configuration to ensure that accounts are not accidentally locked out. If needed, the Microsoft Entra Conditional Access policy can also be tested in Report-only mode.
The policy is enabled with On and saved with Save.

The policy has been successfully created and enforces the device filter.

Functionality check
User Sign-In
When attempting to sign in from a device that is not Microsoft Entra joined, Microsoft Entra hybrid joined or Microsoft Entra registered, the following error message will appear:
Error code 53003 indicates that the sign-in was blocked by a Microsoft Entra Conditional Access policy.
A comprehensive overview of the AADSTS error codes and their descriptions is available for further details: Microsoft Entra authentication & authorization error codes – Microsoft identity platform | Microsoft Learn

Sign-in Logs
The sign-in attempt will appear in the sign-in logs with the sign-in error 53003.
Microsoft Entra admin center (https://entra.microsoft.com) > Identity > Users > All users > Sign-In logs


Configuring Credential Guard and Local Security Authority (LSA)
Required License: Microsoft Intune P1
Windows devices can be better protected against modern threats by configuring Credential Guard and Local Security Authority (LSA), significantly complicating attacks and reducing the risk of sign-in token theft.
Credential Guard and Local Security Authority (LSA) are managed with a configuration policy in the Microsoft Intune admin center (https://intune.microsoft.com).
Devices > Manage devices > Configuration > Policies > Create > New Policy

Select the platform Windows 10 and later (1), profile type Settings catalog (2), and create the policy by clicking Create (3).

Name the configuration profile (e.g., WCP_PreventTokenTheft) and click Next.

Click Add settings (1), set the filter to Device Guard (2), and select Credential Guard (3).
Set the Credential Guard (4) option to Enabled with UEFI lock.

Click Add settings (1), set the filter to Local Security Authority (2), and select Configure LSA Protected Process (3).
Set the Configure LSA Protected Process (4) option to Enabled with UEFI lock.

Create Scope tags according to individual requirements.

Assignments can be customized according to specific requirements.

The settings are shown for review, and by clicking Create, the policy will be created.

The policy is now created and will be deployed to the devices.

The policy will be applied to the assigned devices after a short time.

Content and Phishing Protection
Microsoft Entra Global Secure Access
Required License: Microsoft Entra ID P1
Microsoft Entra Global Secure Access uses the Microsoft Traffic Profile to provide secure and modern access to Microsoft 365 applications – regardless of where users or devices are located.
Access is controlled through policies based on the Zero Trust principle, ensuring that only trusted connections are allowed.
A step-by-step guide for configuring the Microsoft Traffic Profile in Microsoft Entra Global Secure Access is available in the following post:
Microsoft 365: Secure Access with Entra Global Secure Access – cloudcoffee.ch
Microsoft Defender for Office 365: Safe Links and Safe Attachments
Required License: Microsoft Defender for Office 365 Plan 1
Safe Links and Safe Attachments are features of Microsoft Defender for Office 365 designed to protect against malicious URLs and manipulated file attachments.
Safe Links analyzes URLs within Microsoft 365 apps (such as emails, Teams, and Office applications) and blocks access to websites deemed harmful.
Safe Attachments scans file attachments in an isolated environment (sandbox) before delivery to detect potentially harmful code.
A detailed configuration guide is available in the following post:
Microsoft 365 Defender: Safe Links and Safe Attachments – cloudcoffee.ch


