Microsoft Intune Multi Admin Approval: Securing Device Actions such as Wipe, Retire and Delete
Multi Admin Approval (MAA) in Microsoft Intune is a security feature that requires a second user’s approval before critical changes can be executed. This four-eyes principle significantly increases security by ensuring that administrative actions are jointly performed by two users. Initially, the use of Multi Admin Approval in Microsoft Intune focused primarily on configuration objects such as app deployments or scripts.
With the latest enhancement, Microsoft has significantly elevated the feature by extending the approval process to include device actions. This now covers highly sensitive operations such as Wipe, Retire and Delete, which have a direct impact on managed endpoints. Multi Admin Approval in Microsoft Intune actively protects against misconfigurations while preventing devices from being accidentally or unauthorizedly deleted or retired. For organizations leveraging Microsoft Intune as their central device management platform, this feature delivers a higher level of governance and security.
This article demonstrates how to configure Multi Admin Approval (MAA) in Microsoft Intune for device wipe, outlines the prerequisites to consider and explains how to validate the settings to secure critical device actions. The same approach can easily be applied to other operations, such as device deletion or device retirement, ensuring these processes are also safeguarded.
Prerequisites and Licensing
Licenses
The Multi Admin Approval (MAA) feature in Microsoft Intune requires the following license:
An overview of Microsoft licensing plans and their available features can be found at https://m365maps.com/.
Roles
For configuring Multi Admin Approval (MAA), the following roles are suitable based on the principle of least privilege.
| Role | Permission |
| Intune Administrator | Configuring Access Policies for Multi Admin Approval |
| Groups Administrator | Creates and manages the Entra groups that contain the approvers |
Groups
The access policy created in the next step requires a Microsoft Entra group that contains the user accounts of the approvers.

Configuring Multi Admin Approval
The following steps configure Multi Admin Approval for the device wipe task. Other operations, such as device deletion or device retirement, can be set up using the same approach.
Create and Assign an Intune Role for Approvers
To ensure that users from the previously created Microsoft Entra group can view and manage requests in Microsoft Intune without requiring additional Microsoft Entra roles, a dedicated Microsoft Intune role is created and assigned to this group.
Sign in to the Microsoft Intune admin center (https://intune.microsoft.com), then navigate to Tenant administration > Roles > Create > Intune role.

Name the Intune role and click Next.

Set the Permissions as follows:
| Category | Permission | Description |
| Multi Admin Approval | Read access policy | This permission is only required if access policies are not approved by an Intune Administrator or Global Administrator. |
| Multi Admin Approval | Approval for Multi Admin Approval | Allows approving or rejecting requests protected by Multi Admin Approval. |
| Remote tasks | Wipe | Required for approvers to view and process device wipe requests protected by Multi Admin Approval. Without this permission, such requests will not be displayed. |

Configure Scope tags if needed.

Review the settings and create the Intune role by selecting Create.

Select the Intune role that was just created.

Go to Assignments > Assign

Name the Role assignment

Under Admin Groups, select the Microsoft Entra group containing the approvers.

Set the Scope Groups. In this example, the scope groups are defined as All users and All devices.

Select Scope tags, for example Default
Review the role assignment and complete the process by selecting Create.

Configure Access Policy
An access policy for Multi Admin Approval (MAA) in Microsoft Intune defines which changes only take effect after confirmation by a second user. For every change, administrators must provide a justification, which serves as the basis for the approvers’ decision. Only after approval and completion is the change applied in Microsoft Intune, ensuring these actions are consistently safeguarded.
Sign in to the Microsoft Intune admin center (https://intune.microsoft.com), then navigate to Tenant administration > Multi Admin Approval > Access policies > Create.

Name the access policy (1) and select the policy type Device wipe (2).

Select the Microsoft Entra group containing the approvers.

Enter a justification (1) for this access policy and submit it for approval (2).

After creation, the access policy remains pending until it is approved by a user from the assigned Microsoft Entra group.

Approve Access Policy
Another member of the authorised Microsoft Entra group must review and approve the newly created access policy.
Sign in to the Microsoft Intune admin center (https://intune.microsoft.com) and navigate to Tenant administration > Multi Admin Approval > All requests, then select the request.

The request details are displayed and can now be reviewed. Enter a note (1) and either approve (2) or reject (3) the request.

The access policy is now approved.

Complete Access Policy
Once the access policy has been approved under the four-eyes principle, the requester can complete the request.
Sign in to the Microsoft Intune admin center (https://intune.microsoft.com) and navigate to Tenant administration > Multi Admin Approval > My requests, then open the request.

Activate the request by selecting Complete request.

After approval, the request is shown as Completed.

User Experience for Device Wipe
An administrator who attempts to wipe a device with Multi Admin Approval enabled must provide a justification (1) and initiate the approval process (2).

The approvers can view the request in the Microsoft Intune admin center (https://intune.microsoft.com) under Tenant administration > Multi Admin Approval > All requests.

After opening the corresponding request, its details (1) are displayed. Once a note (2) has been entered, the request can be approved (3) or rejected (4).
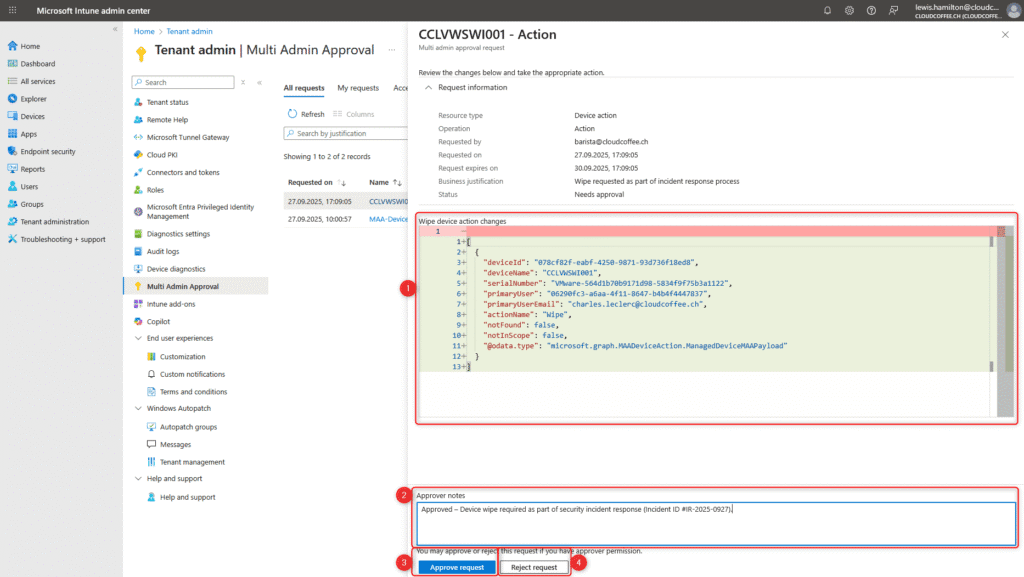
Once the request has been approved under the four-eyes principle, the requester can open the task in the Microsoft Intune admin center (https://intune.microsoft.com) under Tenant administration > Multi Admin Approval > My requests and execute it by selecting Complete request.

The request is now displayed as Completed.

In the Device action status, the pending Wipe task is displayed.

Conclusion
The introduction of Multi-Admin Approval for device actions significantly enhances the security posture in Microsoft Intune. When administrators initiate actions such as wipe, retire, or delete, Intune triggers a structured review and approval workflow before the action takes effect. This process cleanly separates request and approval steps, reducing the risk of misconfigurations, misuse or unintended changes. The combination of Intune roles, Entra groups and well-defined access policies establishes a consistent governance model that strengthens administrative control across the entire tenant.


