Microsoft Entra Connect: Migration to Application Based Authentication (ABA)
With the introduction of Application Based Authentication (ABA), Microsoft introduces modern authentication mechanisms to Microsoft Entra Connect. Previously, the synchronization service used a service account with a locally stored password to sign in to Microsoft Entra ID, an approach considered outdated and potentially vulnerable from a security perspective.
Application Based Authentication (ABA) replaces the service account with a registered application in Microsoft Entra ID that authenticates using the OAuth 2.0 client credential flow. The sign-in process is handled through a certificate that is automatically provisioned and managed by Microsoft Entra Connect. This transition offers several benefits: it eliminates the need for locally stored passwords, reduces the attack surface and aligns with modern cloud security standards.
This article provides a step-by-step guide for migrating Microsoft Entra Connect from the traditional service account to Application Based Authentication (ABA).
Prerequisites and Licensing
Licensing
Microsoft Entra ID Free, which is included in every Microsoft tenant, is sufficient for deploying Microsoft Entra Connect. A paid license is not required for directory synchronization.
Roles
In accordance with the principle of least privilege, the following role is required to install and configure Microsoft Entra Connect:
| Role | Description |
| Hybrid Identity Administrator | Deployment of Microsoft Entra Connect, Management of directory synchronization |
Microsoft Entra Connect
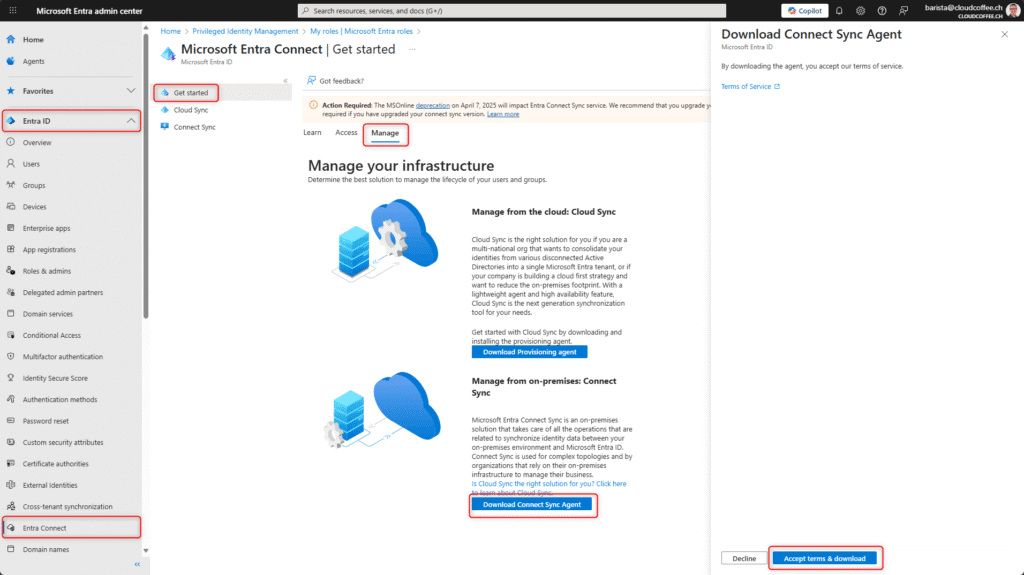
A functional Microsoft Entra Connect installation is required to migrate to Application Based Authentication (ABA). Support for ABA is available as of version 2.5.76.0 (General Availability, GA). The latest version can be downloaded directly from the Microsoft Entra admin center (https://entra.microsoft.com) by navigating to Entra ID > Entra Connect > Get started > Manage > Download Connect Sync Agent > Accept terms & download.
Identifying the Microsoft Entra Connector Account
The Microsoft Entra Connector account is used to authenticate with Microsoft Entra ID and follows the naming format Sync_*@tenant.onmicrosoft.com. During the migration to Application Based Authentication (ABA), this account is automatically removed. Nevertheless, it is recommended to identify the Microsoft Entra Connector account prior to the migration and verify that it has been deleted afterwards.
In the Synchronization Service Manager, navigate to Operations, select the entry with *.onmicrosoft.com and then choose Properties.

The currently used Microsoft Entra Connector account is shown under Connectivity > UserName.
Note down the username for later verification.

Additionally, the account can be found in Microsoft Entra admin center (https://entra.microsoft.com) > Entra ID > Users.

Upgrade of Microsoft Entra Connect
Launch the previously downloaded AzureAdConnect.msi installation file on the server and initiate the process by selecting Upgrade.

The upgrade of the Microsoft Entra Connect components begins.

Sign in using an account that is assigned the Hybrid Identity Administrator role.

Review the configuration and start the upgrade by clicking Upgrade.
The migration to Application Based Authentication (ABA) is performed automatically.

Microsoft Entra Connect has been successfully upgraded after a brief installation process.

Post-Upgrade Validation
Microsoft Entra Connect
Details of the Application Based Authentication (ABA) configuration can now be viewed in the Microsoft Entra Connect settings.
Microsoft Entra Connect > Configure > View or export current configuration
The Certificate Details section displays the relevant information for Application Based Authentication (ABA), such as the certificate thumbprint (1) and the certificate expiration date (2).

With the Automatic Rotation Enabled setting, Microsoft Entra Connect ensures that the certificate is automatically renewed before it expires.

Microsoft Entra Admin Center
During the upgrade of Microsoft Entra Connect, the application ConnectSyncProvisioning_* is created automatically.
Microsoft Entra admin center (https://entra.microsoft.com) > Entra ID > App registrations > All applications

Under Certificates & secrets, the thumbprint of the app registration is displayed. This value matches the thumbprint shown in the Microsoft Entra Connect settings.


Synchronization Service Manager
In Synchronization Service Manager > Operations, all tasks should be completed with the status Success.

Microsoft Entra Connector Account
The previously identified Microsoft Entra Connector account was automatically removed and no longer appears in the Microsoft Entra admin center (https://entra.microsoft.com) > Entra ID > Users.

Good to Know
Manually Rotate the Application Certificate
If needed, the application certificate can also be rotated manually via Microsoft Entra Connect.
Microsoft Entra Connect > Configure > Rotate application configuration

Sign in using an account that is assigned the Hybrid Identity Administrator role.

Review the configuration and rotate the application certificate by clicking Configure.

The application certificate has been successfully rotated.

The new certificate is displayed under Microsoft Entra Connect > Configure > View or export current configuration.



